Let’s start with the basics.
When most people think of the internet, they picture what they can search on Google: websites, blogs, news articles, shopping pages, YouTube videos, and social media posts.
But here’s the catch: that’s only a small part of the internet. In fact, it’s just the tip of the iceberg.
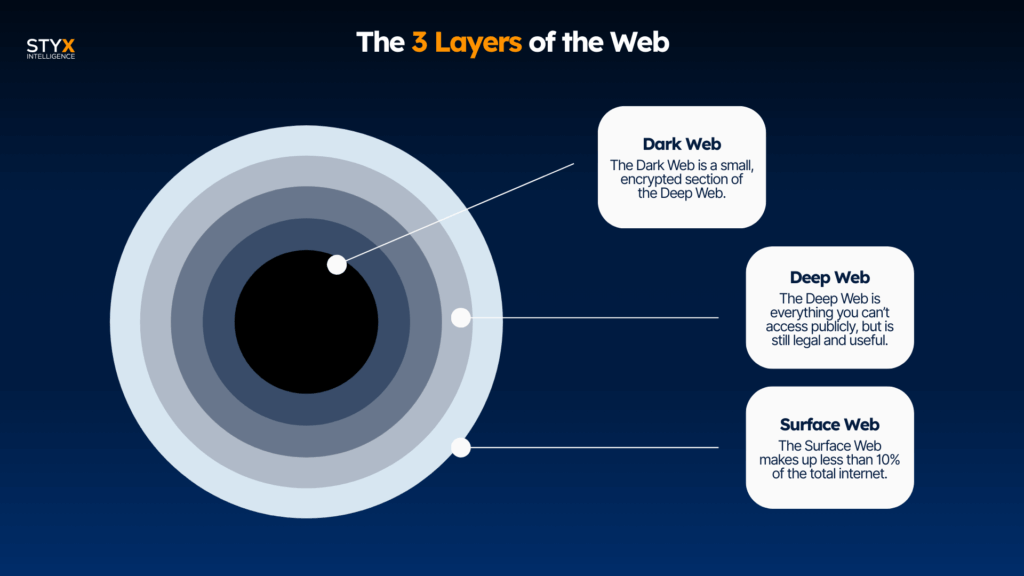
The internet is made up of three main layers.
1. Surface Web (The Part You See)
The Surface Web is everything indexed by search engines, the public side of the internet. It includes:
- News websites
- E-commerce stores
- Public social media profiles
- Wikipedia, blogs, marketing sites
If you can find it on Google or Bing, it’s part of the Surface Web.
But here’s the shocker:
The Surface Web makes up less than 10% of the total internet.
That means over 90% of the internet is hidden from search engines.
So, where is the rest?
2. Deep Web (The Part Behind Logins and Paywalls)
The Deep Web is everything you can’t access publicly, but is still legal and useful. Think:
- Your email inbox (Gmail, Outlook)
- Online banking dashboards
- Netflix or streaming accounts
- Internal business systems and CRMs
- Medical records, academic databases
- Draft content in CMS platforms
- Cloud storage and file-sharing tools
Basically:
If it requires a login, it’s part of the Deep Web.
These pages aren’t indexed by search engines. They’re protected for privacy, security, or business reasons.
You use the Deep Web every day, even if you don’t realize it.
3. Dark Web (The Hidden Underground)
Now here’s where things take a turn.
The Dark Web is a small, encrypted section of the Deep Web. You can’t get to it with Chrome, Safari, or regular search engines.
You need special tools like:
- Tor Browser (The Onion Router)
- I2P (Invisible Internet Project)
- Tails OS (A privacy-focused operating system)
On the Dark Web, websites use “.onion” domains and are intentionally anonymous.
What lives here?
- Hacking forums
- Illegal marketplaces
- Stolen data dumps
- Exploit kits
- Malware-as-a-service
- (And yes, some legit stuff too, like journalists sharing censored stories)
While it sounds mysterious or cinematic, the Dark Web is very real, and very active. It’s where threat actors buy, sell, and launch many of the cyberattacks we see today.
Learn more: What is Dark Web Monitoring?
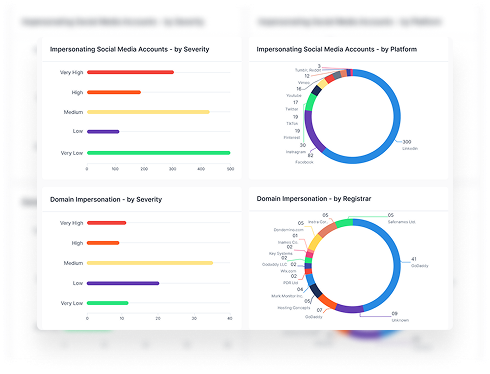
How Cyber Threats Spread Across the Surface Web, Deep Web, and Dark Web
Let’s get practical.
Each layer of the web isn’t just a concept; it’s a channel attackers use. Understanding what happens on each one shows you how threats start, how they spread, and how they hurt your business.
Here’s what’s really going on.
Surface Web: Where Attacks Get In Front of People
This is the public web, the one your customers, employees, and partners see every day. It’s also the first place where threat actors show up when they want to impersonate you.
What you’ll find here:
- Fake websites that look like yours, used to steal logins, data, and money
- Impersonated executives on LinkedIn and social media, targeting employees, partners, and the press
- Spoofed job listings that harvest PII under your name
- Scam ads using your logo to push malware
- Fake donation pages, fake customer support, fake login portals
Most of these threats use your brand to look real.
Why it matters: It’s where scams look the most convincing, and where most people interact with your brand. If something bad shows up here, it hits trust fast.

Deep Web: Where Leaks and Misconfigurations Happen
You use the Deep Web every day, and so does your company. It includes everything behind a login or paywall, including:
- Email systems
- CRMs
- Internal wikis and file shares
- Project tools like Jira or Notion
- Private cloud storage
- Employee portals
- Test environments
These aren’t indexed by search engines, but they’re still vulnerable.
Attackers use it when:
- Employees leave documents public without realizing it
- Contractors use personal apps to handle sensitive work
- Vendors misconfigure cloud services (more about third-party risk management here)
- Links to sensitive files get passed around, and never closed down
- No one tracks how exposed your internal tools really are
- Credentials get leaked and reused across platforms (learn more about data leakage here)
Why it matters:
Leaked data often starts here. Once exposed, attackers grab it, then move it to the dark web to sell or use in attacks.
Dark Web: Where the Damage Gets Distributed
Once stolen, your data doesn’t just disappear… it ends up on forums, marketplaces, and private groups. This is the Dark Web.
Here’s what you’ll find:
- Credentials for sale: Including corporate logins, VPN access, and privileged accounts
- PII dumps: Everything from customer emails to full identity kits
- Stolen financials: Invoices, wire info, banking logins
- Exposed source code and internal documentation
- Phishing kits, ransomware builders, malware-as-a-service
- Access offers: Threat actors selling their way into your network
- Target lists: People planning who to attack next
- Sell access to breached vendors
Learn more: Data Leakage and Dark Web Monitoring
You’re not just dealing with random hackers. This is a supply chain where one breach becomes ten more.
Why it matters:
If your company, execs, or vendors show up here, you’ve got a problem. This is where exposure turns into attack campaigns.

Why You Must Understand How Surface Web, Deep Web, and Dark Web Work
Understanding the difference between the surface web, deep web, and dark web is actually threat intel. It is for any team trying to protect their brand, customers, or data.
Attackers don’t stay in one lane. They move fast across layers.
Here’s how it works:
1. It Often Starts in the Deep Web
You won’t see it happen. But it’s where a lot of exposure begins.
Someone on your team shares a Google Doc with “Anyone with the link” access.
A dev forgets to shut down a test environment.
An old employee portal is still live with real data in it.
These aren’t breaches. They’re unintentional leaks. But attackers don’t care how they get in, just that they can.
They scan for misconfigured cloud tools, open file shares, and forgotten subdomains.
When they find something valuable such as credentials, internal files, invoices, contact lists, they take it.
And then they move on.
Learn more: Data Leakage and Dark Web Monitoring
2. It Gets Monetized on the Dark Web
As you know by now, the dark web isn’t some mystery. It’s a marketplace, and it’s busy.
Stolen data from the deep web ends up here:
- Credentials for company logins
- Customer PII from HR or CRM exports
- Financial data, invoices, and tax info
- Remote access tools or VPN details
- Corporate email accounts with access to vendors
These are bought, sold, and traded. Sometimes, within hours of being stolen.
You won’t know it’s happening unless someone’s watching.
And by the time you do, attackers may have already moved on to the next step.
3. It Shows Up on the Surface Web (Where It Hurts)
This is the part that hits hardest, because it’s public.
Armed with the data, attackers create:
- Fake login pages with your brand’s look and feel
- Social media accounts pretending to be your execs
- Scam job postings targeting real roles at your company
- Customer support impersonators on WhatsApp or Facebook
They look real. They’re built fast. And when someone falls for it, they won’t blame the scammer. They’ll blame your brand.
Even if the breach didn’t start with you.
This Is Why the Layers Matter
The Surface Web, Deep Web, and Dark Web aren’t just a breakdown of how the internet works… they’re a real-world path attackers take:
- Find a weakness in a cloud tool or file share (deep web)
- Sell the access or leak the data (dark web)
- Launch a public attack that damages trust (surface web)
And if you’re not monitoring all three, you’re playing defence blind.
Common Myths That Waste Time
Misunderstanding how the surface web, deep web, and dark web actually work leads to blind spots, and attackers take advantage of that.
Here are the most common myths that waste time, stall security decisions, or give teams a false sense of control.
“The dark web is illegal.”
Wrong. Accessing the dark web isn’t illegal in most countries. What people do there might be, but the network itself is legal, just encrypted and anonymous.
Plenty of journalists, whistleblowers, and researchers use the same tools as threat actors. Avoiding the dark web out of fear doesn’t help. It just makes it easier to ignore signs of trouble.
“I don’t use the deep web.”
Yes, you do, every time you log into email, your banking app, or a cloud file system.
The deep web is just the part of the internet that isn’t indexed by search engines. It includes anything behind a login, password, or paywall.
It’s not a threat on its own, but when your company leaves something exposed here, it becomes one fast.
“Google shows everything.”
Not even close. Google sees the surface web, and only a slice of it.
Search engines don’t crawl your internal tools, cloud platforms, SaaS dashboards, or dark web content. They don’t catch misconfigurations or private file links. If you rely on Google alerts to stay ahead, you’re seeing almost nothing.
“The dark web is only for hackers.”
That’s false, and it’s why many companies ignore it until it’s too late.
Threat actors use the dark web to coordinate attacks, sell stolen data, and share exploit kits. But they’re not the only ones there. The dark web is used for information sharing, leak monitoring, and reputation tracking — if you know where to look.
Skipping it because it sounds shady means you’ll miss early signs of brand impersonation, credential leaks, or insider chatter.

“The dark web is where every attack starts.”
Also wrong.
Many attacks start with public data, scraped from the surface web or leaked from the deep web. The dark web is often where stolen assets go after the breach.
If you only focus on the dark web, you’ll miss how threats build over time — from a misconfigured cloud folder to a fake job post to a stolen identity for sale.
Bottom line:
Understanding the surface, deep, and dark web is how you can map out where threats come from, and what to watch before damage is done.
Monitoring Across All Layers
Most teams monitor what they own.
Internal tools. Corporate email. Endpoint protection. Firewalls.
But that’s not where most of the threats live.
If you want to stay ahead of real attacks, you need visibility across all three layers of the internet, surface web, deep web, and dark web, because that’s where attackers operate.
Here’s what to track, and why.
Surface Web
This is what customers, partners, and attackers see first.
What to monitor:
- Spoofed websites or landing pages using your brand
- Lookalike domains targeting customers or employees
- Executive impersonation on LinkedIn, X, Facebook
- Scam job listings on recruiting sites
- Fraudulent ads or sponsored content using your name
Why it matters:
These threats hit reputation fast. They show up in search results, inboxes, and newsfeeds. Most people won’t know they’re fake, and won’t care when they find out. They’ll just stop trusting your name.
Deep Web
This is where companies leak data without realizing it.
Most of the time, it’s not malicious, just sloppy.
What to monitor:
- Misconfigured cloud tools (Google Drive, SharePoint, Notion, etc.)
- Employee files shared publicly without protection
- Exposed subdomains or test environments
- Internal documentation or org charts visible outside the company
Why it matters:
Attackers scan for these constantly. Once they find a weakness, they take what they can, and move it to the dark web. A single open folder can lead to credential theft, vendor fraud, or phishing campaigns built on real internal data.
Dark Web
Once data is stolen, this is where it goes.
What to monitor:
- Leaked credentials tied to your domain
- PII or sensitive data from your customers or staff
- Listings offering access to your systems or third-party vendors
- Chatter in breach forums or private marketplaces
- Tools or exploits targeting your software or infrastructure
Why it matters:
This is where attacks are planned and monetized. If you wait for it to hit the news or your help desk, you’re too late. Early detection on the dark web lets you shut things down before they turn into full-scale incidents.
Your Risk Doesn’t Stop at the Firewall
You’re not just defending a network anymore.
You’re defending your name, across platforms you don’t control, systems you don’t own, and layers of the internet most teams ignore.
Threats don’t stay in one place. They move fast.
From an exposed doc in the deep web, to a data dump on the dark web, to a fake site on the surface that tricks your customers.
If you’re not looking across the surface web, deep web, and dark web, you’re missing where attacks start, and where damage spreads.
Visibility is how you stay ahead.
Most companies still focus on what’s inside their network. That’s not enough. The real damage often starts outside.
Find out what’s exposed across the web, surface to dark.