What Is Social Media Impersonation?
Social media impersonation is when someone creates a fake social media account to pose as your business, your executives, or your employees. They might copy your logo, use photos from your website, or even mimic the tone of your posts.
The goal?
Trick your customers, partners, or employees into trusting them and then exploit that trust.
Social media impersonations can cause significant harm.
Scammers can use fake profiles to:
- Steal personal or company data
- Spread malware
- Launch phishing attacks
- Trick customers into handing over payment info
- Hurt your brand’s reputation
And it doesn’t stop at your company.
Impersonations in social media also target executives, customer service teams, recruiters, and anyone with a digital presence. They use these identities to launch social engineering attacks, doxing attacks, or trick employees into sharing sensitive information.
Because social media is public, fast-moving, and built on trust, it’s the perfect place for these scams to thrive.
This type of attack is part of a larger problem, brand impersonation and executive impersonation, both of which often start on social media.
Learn more: What is Brand Protection? (And Why You Should Probably Care)
How Social Media Impersonation Works
Social media impersonation is more than one person copying your name. It’s fast, automated, and often part of a much bigger scam.
Here’s how it usually plays out:
1. Attackers gather your public info (your digital footprint)
They start with what’s already online, including executive names, employee bios, brand assets, product images, press releases, or even customer reviews. Most of this lives on your website, social platforms, and news coverage.
For example, on LinkedIn, scammers can get:
- Employee names, titles, and departments (for fake emails or social engineering)
- Executive profiles and bios (to impersonate leadership or run CEO fraud)
- Profile photos and company headshots (for fake profiles or deepfakes)
- Company logo, tagline, and brand visuals (to create spoofed pages or domains)
- Company updates and press releases (to craft convincing phishing lures)
- Team structure and org charts (to identify targets and chain of command)
- New hires and promotions (often targeted in onboarding scams)
- Job listings and tech stack details (to guess internal tools and processes)
- Links to personal websites, emails, or Calendly (for spoofing or phishing)
- Activity feed (likes, comments, shares) (to tailor scam messaging)
That public data becomes the blueprint for the attack.
Learn more: How to Spot and Take Down Fake LinkedIn Accounts.
2. They create fake social media accounts
Scammers spin up accounts that look real, using stolen names, photos, logos, and bios. Sometimes they add slight misspellings (“@StyxxOfficial” instead of “@StyxOfficial”) or switch between underscores, dashes, or other minor changes that are easy to miss at a glance.
They can even copy your entire profile, including banner image, company description, and hashtags, to pass as legit.
3. They use automation to scale and spread
Attackers use bots or cheap tools to:
- Create dozens of similar accounts at once
- They use bots to like, share, or comment to boost visibility and fake legitimacy
- They can even buy followers and engagement to make it look even more legit
- Follow real users
- Comment on your real posts with malicious links
- Send DMs pretending to be support, HR, or leadership
- Share fake updates or offers to boost reach
It’s very fast… and that’s what makes it dangerous.
4. They exploit trust
Once they’ve blended in, the goal is simple: start the attacks and exploit whoever clicks.
- Fake support pages trick customers into giving login credentials
- Fake execs message employees to send wire transfers or internal files
- Scam job offers lead to malware installs or data theft
- Fraudulent promotions gather emails, passwords, or payment info
- Public misinformation damages your reputation in real time
This is called the trust chain, and once it breaks, it’s hard to repair.
Finally…
5. Your reputation (and relationships) take the hit
By the time the fake account is reported, damage is often done. Customers are confused. Employees fall for scams. And partners lose confidence.
And if no one’s watching, these accounts can stay live for days or weeks.
Types of Social Media Impersonation Attacks
When doing social media impersonations, attackers use different angles depending on who they want to fool and what they want to steal.
Here are the most common types of social media impersonations you should watch for:
1. Brand impersonation
Fake company pages that mimic your logo, name, tone, and posts. These accounts can:
- Share scam promotions or giveaways
- Link to phishing pages
- Post false updates or changes in service
- Trick customers into thinking they’re interacting with your real brand
These profiles often appear during events, outages, or promotions, when customers are most engaged.
How can you protect your brand? Learn more about brand monitoring here
2. Executive impersonation
Fake profiles of CEOs, board members, or other leaders. Often used to:
- Contact employees for “urgent” help (wire transfers, login access, etc.)
- Message partners or media with false announcements
- Add credibility to scams targeting your customers
Because these impersonators carry authority, they can do serious damage quickly.

3. Employee impersonation
Cloned profiles of frontline or public-facing staff, like customer support, recruiters, or business development roles. Used to:
- Interact with customers and trick them into sharing account info
- Lure job applicants into phishing schemes
- Spread malware links under the guise of legitimate outreach
If you’ve got employee bios on your website or LinkedIn, you’re already exposed to this risk.
4. Fake support accounts
These pop up in comment threads, forums, or replies to actual posts. They pretend to be your help desk or IT team, usually offering a link to “fix” something. These are built to:
- Steal credentials
- Drop malware
- Capture sensitive customer data
They’re often found responding to actual complaints or service issues in real time, making them harder to spot.
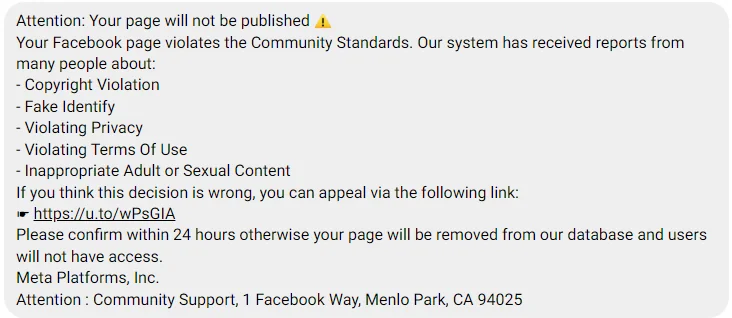
5. Deepfake-driven impersonation
A newer and growing threat: attackers use AI to clone voices or faces of your executives, then post videos or audio clips pretending to make announcements, issue warnings, or promote scams.
These are still rare — but they’re real, and they’re spreading.

6. Hijacked or compromised real accounts
Sometimes, attackers don’t create a new account — they take over a real one. That could be a customer service rep, marketing employee, or even an executive who reused a weak password.
What happens:
- The account is used to spread malicious links or scams
- Attackers target your followers or internal teams from a trusted source
- Detection is delayed because the account seems legit
Learn more: 7 Costly Ways Brand Impersonations Are Hurting Your Business
Real-World Examples of Social Media Impersonation
Do you still think these are hypotheticals?
No.. they’re real attacks using fake social media accounts to mislead, steal, and scam, often using trusted brands as bait.
1. Fake EQ Bank Ads on Instagram
Attackers launched sponsored Instagram ads that closely mimicked EQ Bank’s branding, right down to colours, tone, and style. But instead of linking to EQ Bank, the ad sent users to a phishing site using the domain RBCpromos1[.]cfd.
The fake site prompted users to log in, stealing credentials in the process. These attackers clearly understood the power of brand trust and the visibility paid ads offer.
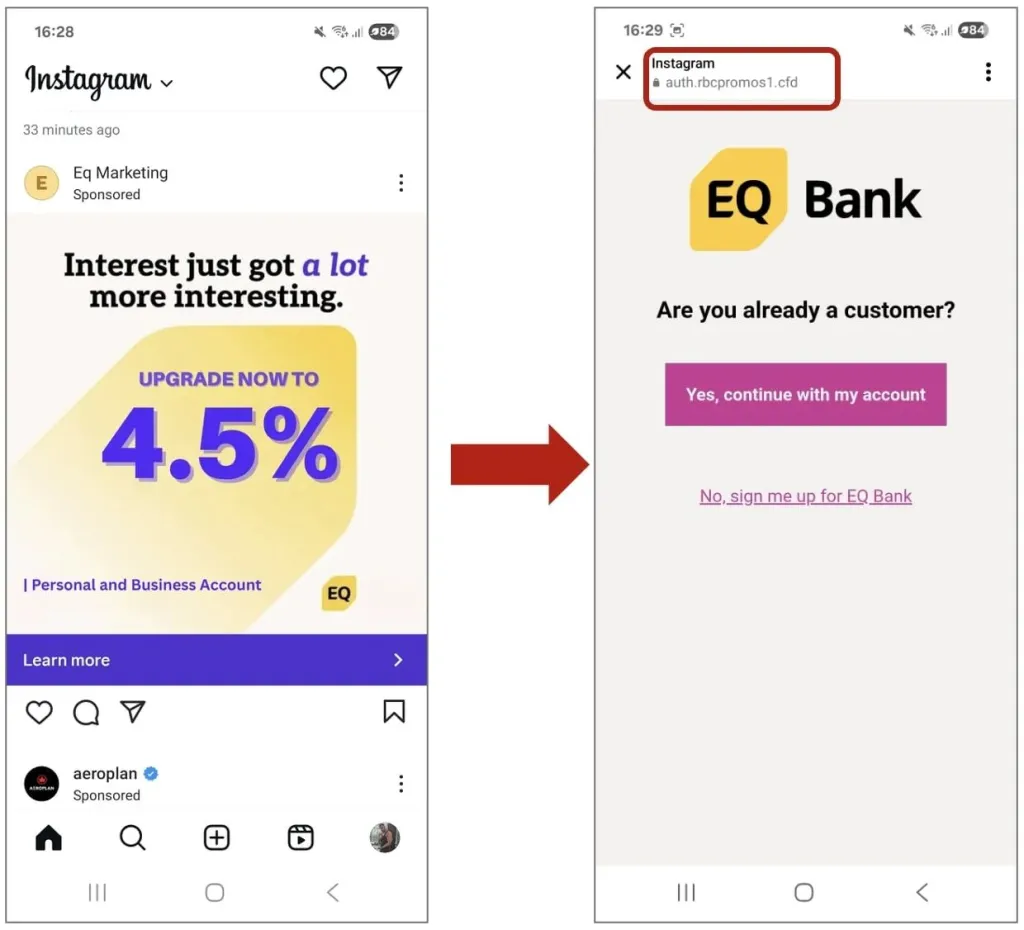
Why it matters: Even well-run institutions are vulnerable. And if you’re not monitoring social ads, you may not see these until it’s too late.
2. Deepfake Videos of BMO’s Chief Strategist
Scammers ran Instagram story ads showing a deepfake video of BMO’s Chief Investment Strategist, Brian Belski. The video led viewers to a fake investment opportunity through a WhatsApp group, promising quick returns.
The video looked convincing enough to trick users into thinking they were hearing from a real executive with authority.
Why it matters: This wasn’t just a fake profile. It used AI to replicate someone’s face and voice, turning a real person’s identity into a weapon.
3. Support Impersonation in Comments
Fake “support teams” pop up in the comments of frustrated users. These impersonators reply to real customer complaints on posts, pretending to help. They offer links, “secure forms,” or DM instructions — all meant to steal login info or install malware.
This tactic has hit banks, airlines, e-commerce brands, and yes, credit unions, too.
Why it matters: These accounts slip into real conversations. Even if your brand didn’t post the scam, your name is still on it, and you take the hit.
4. Lookalike Domains in Fake Ads and Profiles
Scammers often pair fake social media accounts with lookalike domains, websites designed to mimic a real brand’s login page, promo offer, or support portal.
Sometimes it’s obvious (placeboook.com). Other times it’s subtle — a small typo, swapped letter, or foreign character. In more advanced cases, attackers hide the real domain by using subdomains like login.yourbank.secure-support[.]com.
These sites are often linked directly from Instagram or Facebook ads, fake profiles, or support comments. And because many users now browse from phones, they don’t always check the full URL.
Why it matters: One click can lead to stolen credentials, malware, or worse, and once attackers get that trust, they reuse it across platforms and campaigns.
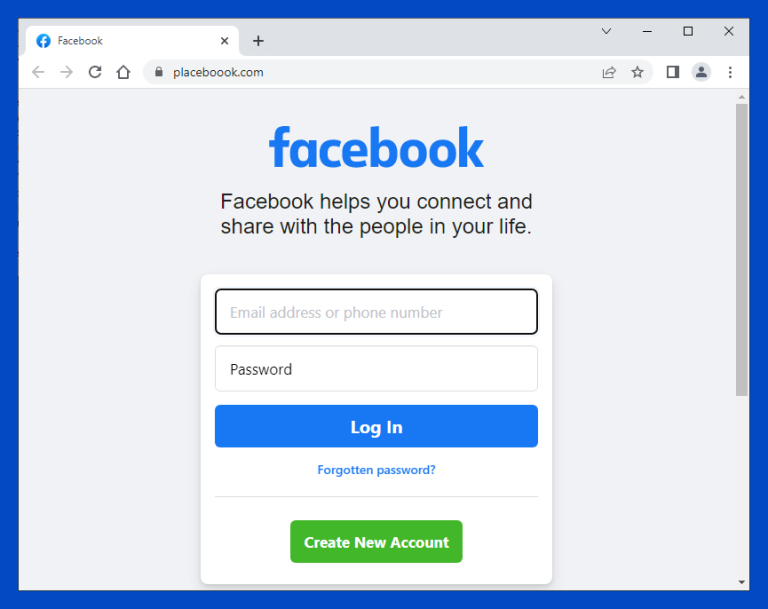
And…
You can find posts like this with one simple search:
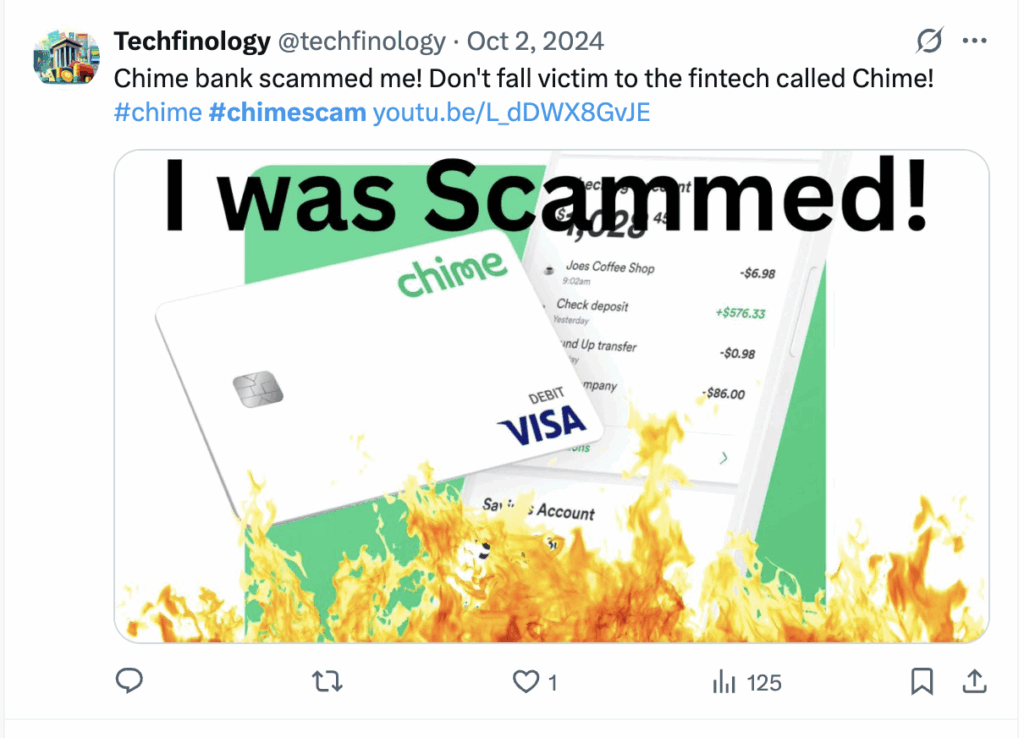
Remember, most impersonations aren’t as simple to detect as the following:
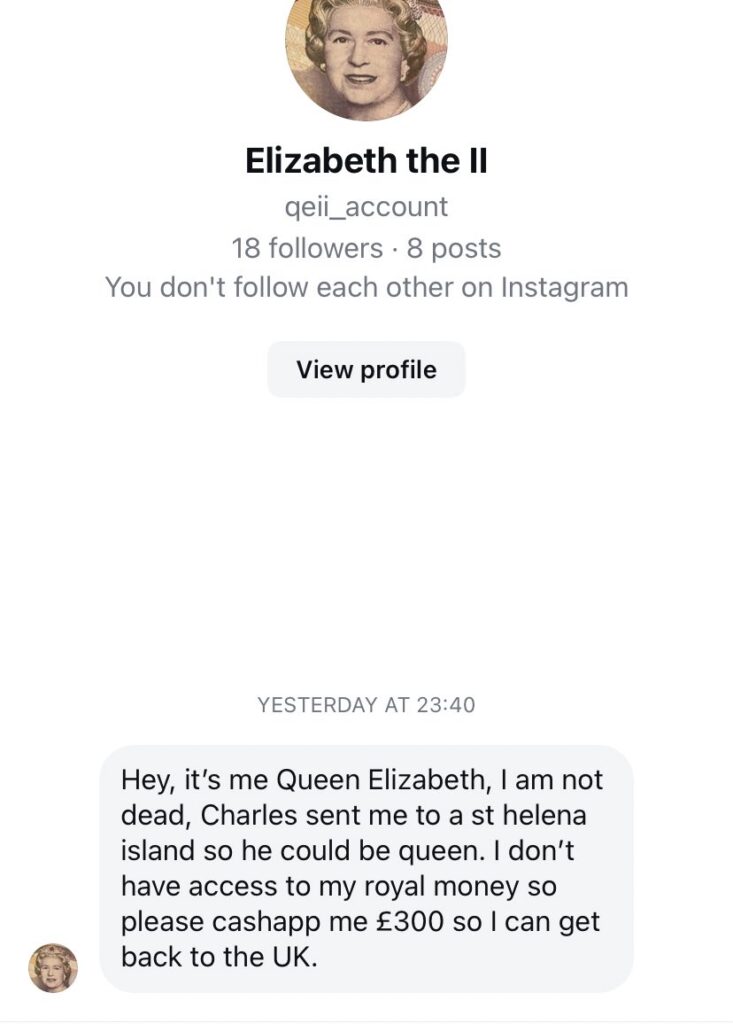
Conclusion:
All these aren’t rare cases. They happen every day and often go unnoticed until someone clicks the wrong link.
How to Spot Social Media Impersonation
Most companies don’t catch impersonation right away. They find out when a customer forwards a weird message, an employee gets phished, or a fake account gains traction.
Here’s what to look for and what to do when it shows up.
1. Look for lookalikes
Fake pages often copy your logo, tone, and posts. The handle might be off by one character, or the name might use punctuation or extra words (like “YourBrand Support” or “YourBrand_Official”).
Check for:
- Recently created pages that mirror your brand
- Slight changes in usernames, display names, or profile images
- Low follower count but high activity
2. Watch for strange engagement
Fake support accounts often reply to your real posts. They jump into comment threads or message followers directly.
Red flags include:
- Replies linking to “secure” forms
- Comments offering account help out of context
- DMs asking for credentials, payment, or “verification”
3. Listen to your customers
One of the first signs something’s off is a customer asking:
“Hey, is this really you?”
If they send a weird link, screenshot, or question, don’t ignore it. That may be the first signal you’re being impersonated.
4. Train your team
Internal staff should know how to flag impersonation, too. Executives are common targets. So are recruiters, customer service reps, and anyone with a public-facing role.
If an employee gets a DM from “your CEO” asking for urgent help, it’s probably not your CEO.
5. Don’t wait for reports
By the time someone asks, “Is this you?” — damage may already be done. Real monitoring means catching impersonation before the scams spread. That means:
- Watching social platforms for fake accounts and pages
- Scanning mentions, comments, and DMs for suspicious activity
- Using takedown tools when needed (we’ll get to that next)
What to Do if You’re Being Impersonated
There are two ways to respond: manually, or with dedicated tools built to handle it.
I) Manually:
If you’re not using a dedicated platform, here’s how to respond manually:
1. Search your brand and people regularly
Start with your company name. Then check for:
- Variations of your brand (misspellings, added words, odd punctuation)
- Fake support or giveaway accounts
- Clones of executive or employee profiles
Look across Instagram, Facebook, X, LinkedIn, TikTok — especially the ones your customers use.
2. Use reverse image searches
Fake accounts often steal profile photos or brand images. Tools like Google Images or TinEye can help you track where your logo or executive headshots are being used.
3. Document everything
Take screenshots. Save URLs. Log timestamps. The more evidence you have, the more likely platforms will respond quickly. And if legal or regulatory action is needed, you’ll already have the record.
4. Report directly to the platforms
Each platform has its own process for reporting impersonation, and they’re not all fast or easy.
Links to start with:
- Meta Reporting (Facebook & Instagram)
- X (Twitter) Impersonation Policy
- LinkedIn Fake Profile Reporting
Note: Some require proof of identity or trademarks. Others ask for notarized forms or legal emails.
5. Warn your audience
If the fake account is posting or messaging your customers, get ahead of it:
- Post on your real channels that a fake is circulating
- Share screenshots of the scam account (don’t link to it)
- Pin a post with tips to spot real communication from you
- Encourage followers to report the impersonator, too
6. Stay on it
Platforms may take hours or days to remove fake accounts. Some don’t act at all unless the scam goes viral. You may need to follow up more than once.
Bottom line:
Manual response is possible, but it’s slow, reactive, and high-effort. Every hour the fake account stays live, it can do real harm. That’s why many teams look for automated ways to detect and respond sooner.
II) Dedicated AI-powered tool:
Modern cybersecurity platforms, like Styx Intelligence, now include AI-powered capabilities to monitor and protect your digital presence, especially on social media.
Here’s what that means:
1. Monitor your digital footprint automatically
These tools scan the internet, including social media, forums, marketplaces, and the dark web, to find fake accounts, impersonation attempts, and unusual mentions tied to your brand or execs.
They don’t wait for someone to report a fake. They flag it as soon as it appears.
Learn more: External Attack Surface Management
2. Cover everything that matters
Effective platforms track:
- Brand names, logos, and lookalike accounts
- Executive names and images (even across fake profiles)
- Employee impersonation attempts
- Social media ads, comments, and support replies
- Lookalike domains and phishing links tied to impersonation (these can really damage businesses)
Some tools are even smart enough to catch impersonation campaigns using deepfakes, fake giveaways, or cloned promo pages.
3. Watch sentiment shifts and reputation risks
Your brand’s reputation can take a hit before you even know what happened.
These tools track:
- Changes in sentiment across posts, news, blogs, and comments
- Negative trends that could signal impersonation or fraud
- Spikes in engagement tied to harmful narratives or fake content
This lets you act before the story spins out of control, not after.
4. Surface real threats, not noise
The best platforms score and prioritize threats so small teams can focus on what matters:
- Which fake accounts are gaining traction
- Which impersonations link to phishing or malware
- Which accounts target customers, partners, or employees

5. Get alerts for takeovers and identity misuse
You’ll get notified the moment something suspicious happens:
- A fake account using your logo goes live
- Your executive profile posts something off
- A takeover attempt hits your corporate page
No waiting for someone to flag it. No digging through mentions. Just actionable alerts, fast.
6. Detect and shut down fake accounts
The best platforms let you:
- Instantly flag fake profiles
- Track resolution progress and takedown status
- Monitor results and spot repeat abuse
- Bundle evidence to speed up takedown requests
This isn’t just helpful — it saves hours of back-and-forth with platforms that often move slowly.
Learn more: What’s a Takedown?
7. Act before customers ask
When impersonation happens, speed matters. These tools help you find fake accounts before they go viral, before someone clicks the link, and before your customers send that message: “Is this really you?”
Best Practices & Priorities to Reduce Risk
Social media impersonation can’t be fully prevented, but it can be managed. The faster you detect, act, and respond, the less damage it causes.
Here’s where to focus:
1. Monitor 24/7 — not just when there’s a problem
Impersonation often starts quietly. A new profile goes live. A fake ad runs. A deepfake gets posted.
If you’re only reacting when someone flags it, you’re already late.
Monitor your brand, execs, and public-facing teams across social media, news, forums, and marketplaces. Look for fake pages, odd mentions, weird URLs, and fast-moving posts.
2. Build clear internal reporting
Make it easy for employees to report suspicious content, especially if it uses their name or likeness.
Flag impersonation attempts. Collect evidence. Have a point person or team that can escalate fast.
3. Train your team and talk to your audience
People can’t avoid what they don’t see coming.
Educate employees on how to spot impersonation and what to do if it happens.
Let your audience know how you communicate and what to look for in fakes.
4. Know your exposure
You can’t defend what you can’t see.
Understand where your brand shows up. What assets are live? What profiles exist? Where your execs appear. That’s your digital footprint — and it’s the surface attackers use.
You can start with a quick audit or take advantage of tools like a Digital Risk Score to see what’s exposed.

5. Have a plan
When impersonation happens, you don’t want to figure it out on the fly.
Have a clear plan for:
- Who responds
- How to alert platforms
- What to say publicly
- What evidence to gather
- How to handle media or customer questions
Make it simple. Make it fast.
6. Use tools that fit your team
If you’re small, you need tools that reduce noise and surface only what matters. If you’re growing, you need visibility that scales. Either way, modern protection should save time, not add work.
Need help protecting your brand and executives on social media?
Try Styx Intelligence FOR FREE (no credit card required) and see your exposure live.
















