Let’s be honest: most “digital risk scores” feel like black boxes. Numbers go up, alerts fly in, and somehow you’re left guessing what to do next.
Well… we want to change that.
We’ll break down what a digital risk score really is, how the Risk Scorecard works, what signals go into it, and how it can actually help you make smarter, faster decisions — without the fluff, fear tactics, or buzzword soup.
Let’s get started.
What’s a Digital Risk Score?
In simple words: A risk score is a number that tells you how exposed you are — and how urgently you should care.
In cybersecurity, security risk scores help you figure out which problems are actually problems. This score is a fundamental part of Digital Risk Protection (DRP).
As you know, not every alert matters. Not every misconfiguration is a meltdown.
Think of it like this:
- Low score? You’re in decent shape.
- High score? You’ve got some work to do.
A digital risk score (security score too) helps you measure threats outside your firewall — things like impersonations, brand abuse, sensitive data exposure, social media takeovers, or third-party issues.
But the idea applies across the board: your risk score tells you where you stand and where to act.
This isn’t about false alerts or fear. It’s more like someone tapping you on the shoulder and saying:
“Hey — this matters. Fix this first.”
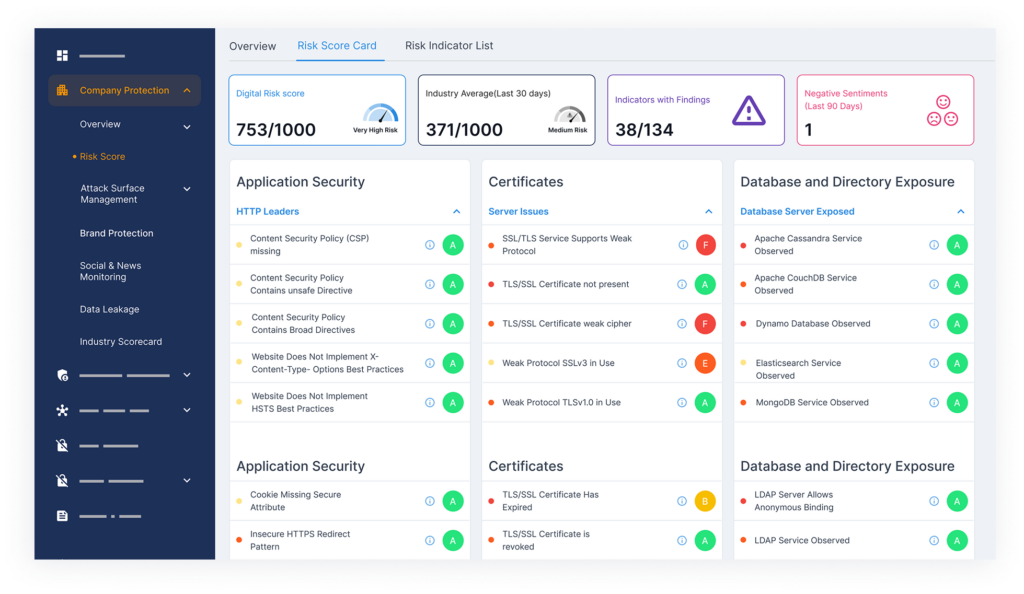
Why is a Risk Security Score Important?
Because knowing where you’re exposed, and what to do about it, is half the battle.
A digital risk score is a way to make smarter decisions, faster, with full visibility into your external risk posture.
Here’s what it helps you do:
1. Get the Full Picture
Your digital footprint is constantly changing. New assets pop up, vendors onboard, campaigns go live. A risk score gives you a clear, real-time snapshot of your exposure — across social media, domains, leaked data, and beyond.
2. Move from Alerts to Action
You’re getting much more than automated alerts. You’re getting a risk score that’s shaped and prioritized by validated findings.
See something that’s not relevant? Mark it as a false positive.
Did you resolve a misconfiguration? Watch your security score improve.
It’s actionable, and you have full control — all part of Digital Risk Protection.
3. Stay Continuously Informed
The world doesn’t run on weekly scans. Continuous monitoring means your score reflects live signals from the surface, deep, and dark web, and updates as your exposure changes.
(By the way, if you want to learn everything about our platform, check out our Styx Platform Overview page.)
Let’s continue.
4. Focus on What Matters
Your security score helps you prioritize based on business impact, likelihood of exploitation, and relevance to your environment. This lets you focus on what matters, ignore the noise, and make better calls under pressure.
5. Connect Security to Business Outcomes
At the end of the day, it’s not about fixing everything — it’s about fixing the right things.
A good score helps you track progress, justify investments, and align security with business goals. It’s a tool for clarity, not just compliance.
Learn more: The Future of Digital Risk Protection (DRP)
In short: it’s contextual visibility with built-in prioritization — helping you cut through noise and act on what matters.
Behind the Risk Score: What Feeds Your Risk Scorecard
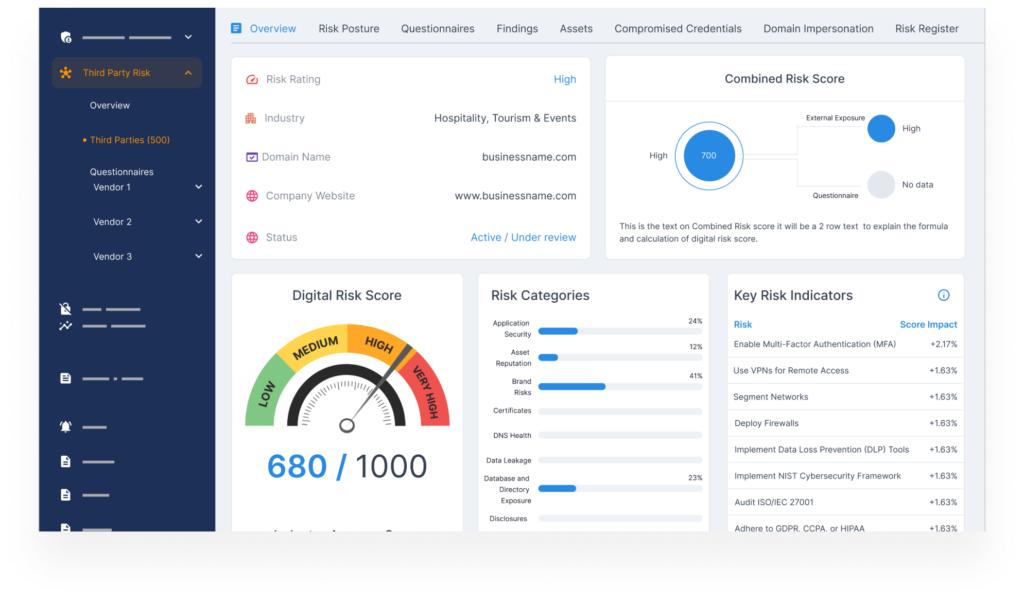
Your Risk Scorecard is built by collecting data across a broad set of real-world signals — also called risk indicators.
These indicators are grouped into categories that reflect different parts of your digital exposure, from infrastructure to social media to the dark web.
Each one tells a story about your organization’s external risks—and together, they shape your overall score.
Let’s go over these categories and indicators:
1) Attack Surface Intelligence
This category focuses on the visible part of your external infrastructure — what attackers can see and potentially exploit. It includes:
-
Websites, subdomains, and DNS configurations: Monitoring for misconfigurations or vulnerabilities that could be exploited.
-
Exposed network services or ports: Identifying services like FTP, SSH, or MongoDB running without proper protection.
-
Unsecured web applications and APIs: Detecting applications lacking essential security measures.
-
TLS/SSL certificate issues: Checking for expired or misconfigured certificates that could compromise secure communications.
-
Public-facing social media and communication channels: Assessing the security of platforms that represent your organization online.
Examples of specific indicators:
-
FTP Service Observed (21): Detection of an FTP service running on port 21, a common target for exploitation.
-
HTTP Service Observed (and site does not enforce HTTPS) (80): HTTP service running on port 80 without HTTPS enforcement, exposing data to interception.
-
TLS/SSL Certificate Expiring Soon: A TLS/SSL certificate approaching expiration, requiring timely renewal to avoid security risks.
2) Brand Intelligence
Your brand is a magnet — for customers and attackers alike. This category monitors for threats that could damage your brand’s reputation.
It includes:
-
Domain impersonations and lookalike websites: Identifying fraudulent domains that mimic your brand.
-
Rogue mobile apps: Detecting unauthorized applications that could deceive users.
-
Fake job postings and phishing recruitment scams: Monitoring for deceptive employment offers that exploit your brand.
-
Social media impersonations: Finding fake profiles that could mislead your audience.
-
Marketplace and forum misuse of your brand identity: Spotting unauthorized use of your brand in various online platforms.
Examples of specific indicators:
-
Lookalike Domain: A domain name that closely resembles your own, often used in phishing attacks.
-
Rogue Mobile App: A mobile app identified as being potentially harmful or unauthorized.
-
Social Media Impersonation: Instances of social media accounts impersonating your organization.
Check out this article to learn more about brand protection and brand protection strategies.
3) Social & News Monitoring
First of all, you must protect your brand across social media & news because public perception can significantly impact your organization.
This category monitors for:
-
Sudden sentiment shifts across social platforms: Detecting changes in how your brand is perceived online.
-
False narratives or emerging misinformation: Identifying and addressing misleading information that could harm your reputation.
-
Trending risks involving your brand, executives, or industry: Staying ahead of potential crises by monitoring relevant discussions.
Examples of specific indicators:
-
Negative News Sentiment: A KPI measuring negative sentiment from news sources.
-
Negative Social Sentiment: A KPI measuring negative sentiment from social media sources.
4) Data Leakage & Credential Exposure
This category tracks exposed, leaked data that could be used against your organization. It includes:
-
Leaked credentials tied to your domains or employees: Monitoring for compromised usernames and passwords.
-
Sensitive corporate data found in breach dumps or forums: Identifying confidential information that has been exposed.
-
Personally identifiable information (PII) shared or sold: Detecting unauthorized distribution of personal data.
-
Mentions of your organization on the dark web or Telegram: Keeping tabs on discussions that could indicate targeted threats.
Examples of specific indicators:
-
Compromised Account with Password: Accounts compromised through the exposure or theft of passwords.
-
Exposed Documents: Documents exposed online containing sensitive or confidential information.
-
Dark Web Mention: Mentions of your organization found on the Dark Web, indicating potential exposure.
What Do We Actually Analyze?
To paint a full picture of your digital risk, we continuously analyze:
- Your external digital footprint (assets, infrastructure, domains)
- We also analyze your vendors — from their exposed assets and misconfigurations to breach history and impersonations — helping you understand how risky they really are. That way, you can make smarter decisions when choosing, onboarding, or reviewing your vendors.
- Brand signals across domains, apps, marketplaces, and forums
- Public narratives on social media and in the news
- Leaks of sensitive information across the surface, deep, and dark web
Together, these indicators give you a clear signal: what’s exposed, what’s at risk, and what to do next.
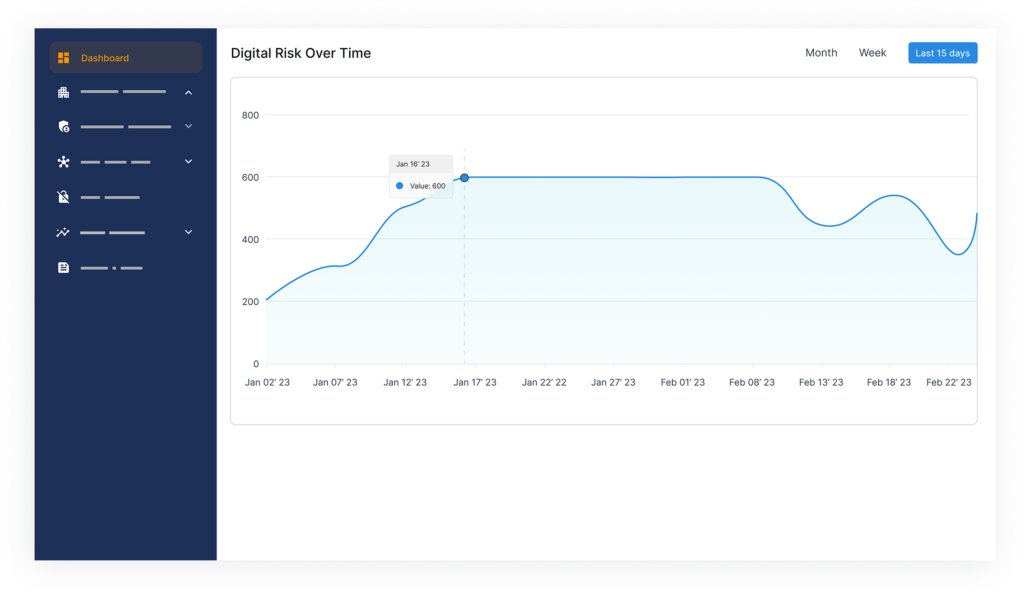
Next up: let’s talk about how all these signals come together to create a real-time digital risk score.
How Your Risk Scorecard Gets Built: From Signals to Security Score
Some platforms throw a score at you without telling you where it came from. Others flag every issue as high priority, whether it’s a broken SPF record or a leaked database.
That’s definitely not the best way to do things.
For example, at Styx, your risk scorecard is built on real, validated data — tied to specific assets, prioritized by impact, and constantly updated as things change.
No assumptions, no inflated alerts, and no mystery math. Just clear, contextual, and fair scoring that reflects what actually matters.
Here’s how it works:
1. Collect the Right Data
First, we go wide. Risk indicators are gathered from hundreds of sources — public and proprietary — like:
- Vulnerability databases
- Domain registries
- Threat intel feeds
- Certificate transparency logs
- Dark web forums
- OSINT (open-source intelligence)
This gives us a complete outside-in view of your digital footprint and any cracks in the surface.
2. Map Every Finding to What It Affects
Each signal gets tied to what it actually impacts: your domain, an IP, a certificate, a server — whatever the vulnerable or exposed asset is. This way, your score isn’t just abstract math — it reflects what’s actually at risk.
3. Weigh the Risk (Because Not All Findings Are Equal)
Some problems are bigger than others — a missing SPF record isn’t the same as leaked employee credentials. That’s why every indicator has a weight, and each finding gets a severity level.
Each finding’s severity determines its contribution to the score:
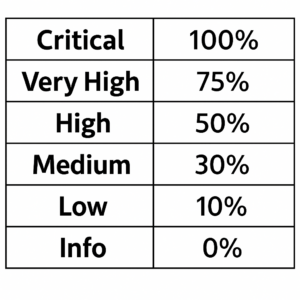
4. Adjust for Company Size
A 10-person startup and a 10,000-person enterprise face different risks. So we adjust the grading model based on your digital footprint and team size.
The larger and more complex you are, the more we expect — and we grade accordingly, using models (Alpha, Beta, Delta, etc.) to keep it fair.
5. Dynamic Scoring
Your score isn’t static — it changes as your environment changes.
New breach? Score goes up.
Fix an exposed repo? Score goes down.
The idea is to reflect your real-world risk, not yesterday’s snapshot.
6. Final Risk Score Aggregation
Finally, all of those individual, weighted scores come together to form your final risk score — a single, unified number that reflects your overall digital exposure.
It’s your guide for what to fix, where to focus, and how your security posture is trending.
That’s it!
Now, what does this score mean?
What Your Risk Scorecard Grade Actually Means
Your Digital Risk Score is a reflection of how exposed your organization is from the outside. It’s based on verified issues like data leaks, misconfigurations, expired certificates, exposed assets, and more.
The score looks at two key things:
- How many issues we found
- How severe those issues are
The more severe or widespread the findings, the higher your score — which means higher risk.
In plain terms:
- High Score = More problems, more urgency
- Low Score = Fewer risks, tighter security
To make it easy to understand at a glance, we translate your score into a simple A–F grade:
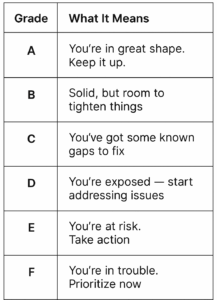
This grade isn’t meant to scare you. It’s here to give you clarity — and to help teams, boards, and partners get on the same page, fast.
Visual Dashboards That Actually Make Sense
Let see how we do it at Styx.
Inside Styxview, you get clean, visual dashboards that show you exactly:
- Where your biggest risks are
- How your digital risk score is trending over time
- What’s improved — and what still needs attention
You can slice data by domain, asset, category, or severity — whatever makes the most sense for your workflow. It’s perfect for internal reviews, executive updates, or proving security wins to your board.
What you can do with it:
- Spot high-risk assets instantly
- Show risk posture improvements over time
- Turn insights into action, fast

Want to know where you stand?
Get your free Digital Risk Scorecard — along with tailored insights from one of our amazing team members.
You’ll get a full breakdown of your external risks, what they mean for your brand, and practical steps to fix them.

















