A proactive approach is the difference between stopping risk early and cleaning up damage later.
Most security teams still act only after something breaks, but today’s attacks start long before any alert is triggered.
This article explains why reactive security falls short and what changes when teams act earlier.
Reactive Security is Built to Respond After Damage Starts
Most security teams operate in a reactive model, even if they don’t describe it that way.
Reactive security means the team waits for a strong enough signal to justify action, and that signal usually comes from within the organization.
It could be:
- An alert
- A log anomaly
- A detection rule firing
- A user reports something suspicious
Until that moment, the assumption is that nothing urgent is happening.
The problem is that many modern attacks start from outside the perimeter and do not trigger these signals early. Attackers often begin with access that already works.
- They use legit credentials.
- They log into company-owned systems.
- They move through platforms that are already trusted.
From the security team’s point of view, nothing looks wrong yet, because nothing has technically failed.
In a reactive model, this means no response happens at this stage. There is nothing concrete enough to justify action.
However, by the time that confirmation arrives, the attack is already happening.
Proactive Security Focuses on Early Signals
A proactive security approach is not about predicting the future or chasing every possible threat. It is about acting earlier, based on credible signals that something is forming, even if nothing is “broken” yet.
Instead of waiting for an incident to declare itself, proactive teams look for indicators that increase the likelihood of future damage.
These indicators rarely appear inside core systems at first. They show up in places most reactive workflows ignore.
Things like:
- Exposed credentials outside the organization
- Impersonation infrastructure being prepared
- Unusual activity tied to third parties, or
- Public-facing assets being copied or misused.
In a proactive model, these signals are treated as actionable risk.
For example:
- A leaked credential does not mean a breach has occurred. But it does mean access is now possible.
- A fake domain does not mean customers have been harmed yet. But it does mean an attack path is being built.
- A third-party breach does not automatically impact your environment. But it does increase the chance that your data or access will be abused next.
Proactive teams do not wait for these risks to turn into incidents. They intervene earlier by taking down exposure, invalidating access, or disrupting attacker infrastructure before it is used at scale.
This shifts security from “prove something bad happened” to “reduce the chances it happens at all.”
Why Reactive Security Still Dominates Most Organizations
Reactive security is not the result of poor judgment. It is the result of how security teams have been trained, measured, and staffed for years.
Most security programs were built to answer one core question: “Has something bad already happened?”
That mindset shapes everything.
- Tools are selected based on how well they detect confirmed incidents.
- Teams are evaluated on how quickly they respond once an alert fires.
- Processes are designed to avoid false positives and unnecessary disruption.
- Acting too early often feels riskier than acting too late.
Several forces keep teams stuck in this model.
1) Proof is required before action
Security teams are expected to justify every response. Without a clear incident, it is hard to explain why access was revoked, a domain was taken down, or a workflow was interrupted.
2) Ownership is fragmented
Early warning signals often live outside security’s direct scope:
- Exposed credentials appear in external spaces
- Impersonation affects brand and communications
- Third-party issues involve procurement or legal
When no single team owns these signals, they are easy to ignore.
3) Noise fatigue
External data can feel overwhelming. Without prioritization, teams default to ignoring early indicators rather than risk chasing false alarms.
4) Reactive work is familiar
Alerts, incidents, tickets, and postmortems are well understood. Proactive work feels less defined and harder to operationalize.
The result is a security posture that responds well once damage is visible, but struggles to act while damage is still preventable.
This is not a failure of intent. It is a structural limitation.
A proactive approach works differently because it is designed around reducing exposure, not waiting for confirmation.
Why Early Signals Usually Live Outside Your Perimeter
One of the biggest differences between reactive and proactive security is where teams look for risk.
Before attackers touch your internal systems, they usually prepare elsewhere:
- They collect credentials from breaches, malware, or private leaks
- They register domains that look like brands or vendors
- They create fake profiles, support pages, or login flows
- They study public infrastructure and third-party relationships
None of this activity triggers internal alerts. From the inside, everything still looks normal.
Unfortunately, this creates a dangerous blind spot.
By the time an attacker logs in with valid credentials or sends a convincing message from a “trusted” domain, the preparation phase is already complete. Internal tools see a successful login, not the weeks of setup that made it possible.
Proactive teams close this gap by watching the spaces where attackers operate early:
- Public and private breach data
- Credential exposure tied to employees or vendors
- Infrastructure that imitates trusted assets
- Signals that indicate planning, not execution
This external visibility does not replace internal detection. It complements it.
The goal here is to shorten the time between attacker preparation and defensive action.
When you see attacks forming earlier, you do not have to react under pressure later.
What Proactive Security Actually Changes in Day-to-Day Work
Proactive security does not replace incident response. It changes what teams focus on before an incident occurs.
Instead of asking, “What alerts fired today?” the focus shifts to, “What exposure exists right now that could be abused next?”
This changes daily work in a few important ways.
1) Risk is evaluated before impact
Teams act on conditions that increase the likelihood of harm, even if no damage has occurred yet.
That includes things like:
- Credentials exposed outside the organization
- Impersonation assets being prepared
- Third-party systems showing signs of compromise
- Public infrastructure being copied or misused
None of these are incidents by themselves. But each one shortens the distance to an incident.
2) Response happens earlier and is lighter
Taking down a lookalike domain before it gains traffic is easier than managing customer fallout later, or resetting credentials before access is abused, which avoids deeper investigation and recovery work.
Earlier action usually means less disruption, not more.
3) Work becomes preventive instead of corrective
Proactive teams spend more time acting on potential threats and less time cleaning up consequences.
This leads to:
- Fewer emergency escalations
- Shorter investigations
- Less pressure on response teams
- Fewer cross-team fire drills
4) Security gains leverage.
When teams can show how early actions reduced risk or prevented incidents, security shifts from being seen as a reactive cost to proactive protection.
Proactive security is not about doing more work. It is about doing the right work sooner, when it is still manageable.
That timing difference changes everything.
How Teams Adopt a Proactive Model Without Breaking Everything
Most security teams agree with the idea of being proactive. The hesitation comes from a practical concern:
“How do we do this without overwhelming the team or creating chaos?”
A proactive model does not mean chasing every signal or reacting to every external mention. It means introducing structure earlier in the attack timeline, not adding noise.
Teams that adopt this approach usually start with three shifts.
1) They define what “early” actually means
Proactive security fails when teams act on vague intuition. It works when teams agree on clear, early indicators that justify action.
Examples of early indicators include:
- Credentials exposed outside the organization
- Infrastructure that imitates trusted assets
- Repeated signals tied to the same brand, vendor, or user
- An activity that lowers the cost of an attack, even if no abuse has occurred
These signals do not confirm an incident. They confirm increased likelihood.
Once teams align on that distinction, early action becomes easier to justify.
2) They add prioritization before response
Not every signal deserves the same attention. Proactive teams introduce lightweight triage so effort stays focused.
That usually means asking:
- Does this enable access?
- Does this create trust with users or employees?
- Does this connect to systems we rely on?
If the answer is yes, it moves forward. If not, it waits.
This prevents proactive work from turning into constant interruption.
3) They integrate early action into existing workflows
Proactive security does not require a new team or process. It plugs into what already exists.
Early signals feed into:
- Credential resets
- Infrastructure removal
- Vendor reviews
- Short investigations
The difference is timing, not ownership.
When teams treat early exposure as something to reduce, not something to debate, proactive security becomes sustainable.
It stops being an idea and starts becoming routine.

What a Proactive Security Model Looks Like in Practice Today
In practice, proactive security is built around a simple loop: See earlier, decide faster, act before any damage occurs.
Below is what that actually looks like when implemented correctly.
1. Continuous visibility across the external attack surface
Proactive teams maintain 24/7 visibility into the entire attack surface, especially all the environments attackers use first.
This includes:
- Public-facing domains and infrastructure
- Lookalike domains and impersonation assets
- Social media and web-based impersonation attempts
- Credential exposure tied to employees, executives, or vendors
- Third-party platforms that store or integrate with internal data
The key difference is coverage across surface, deep, and dark web sources, not just internal systems.
This visibility creates context before an alert ever fires.
2. Early signal detection
Instead of waiting for proof of abuse, proactive teams look for signals that lower the barrier to attack, such as:
- Valid credentials appearing outside the organization
- Infrastructure being prepared to impersonate trusted entities
- Vendor-related exposure that could be reused against internal systems
- Brand impersonation attempts on Social media
- Executive impersonation attempts on Social media
These are treated as time-sensitive potential risks.
Early detection creates decision space.
3. Risk scoring and prioritization before response
Volume is inevitable, but prioritization is key here.
A proactive model relies on real-time risk scoring that reflects actual external exposure, not static checklists or one-size-fits-all ratings.
This approach focuses on:
- Live risk scoring that updates as new external signals appear
- Context-aware prioritization, not just alert volume
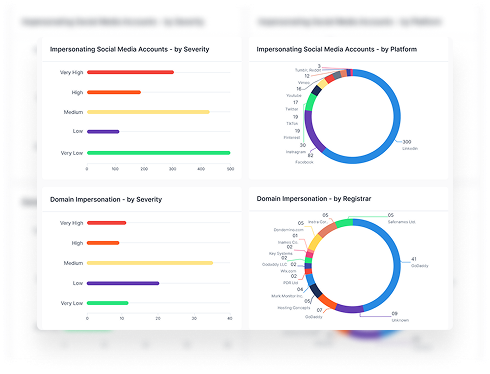
- Clear severity grouping, so teams know what requires immediate action
By mapping risks back to domains, assets, and connected third parties, teams gain a consolidated view of where exposure is building and where action will have the most impact.
4. Integrated disruption
When early signals cross a defined threshold, action is immediate.
That includes:
- Resetting or restricting exposed access
- Taking down impersonations
- Disrupting fraudulent domains, pages, or profiles
- Coordinating takedowns across providers and platforms
These actions are integrated into response workflows, not treated as separate services.
5. Continuous feedback and improvement
Every action feeds back into the model:
- Which signals led to incidents
- Which disruptions prevented escalation
- Where coverage needs to expand
That is what proactive security looks like in practice today.
In summary:
A proactive model works when you can see external risk early, prioritize it, and take action before it turns into an incident.
Book a demo to see how Styx brings brand protection, credential leak detection, third-party risk, and takedowns into one consolidated platform.