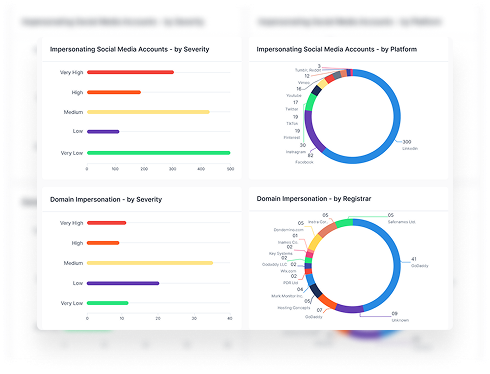
Executive protection once focused primarily on physical threats — securing travel, managing appearances, and reducing physical risks.
But today, things have changed.
As leaders become more visible across digital platforms, a new kind of threat has emerged: online executive impersonation.
Executives are no longer just public figures — they’re digital ones. Their names, voices, and photos are everywhere online.
And with that kind of visibility, plus new tools that make fakes more convincing, the risk of identity-based threats has grown fast.
What is Digital Executive Impersonation?
Digital executive impersonation involves the unauthorized use of an executive’s identity — using their name, title, photo, voice, or presence to deceive or manipulate others.
These impersonations are used to trick people, steal money, spread false information, or damage a company’s reputation. And they’re showing up in more ways than ever:
- Fake social media accounts that copy executive profiles and messaging
- Lookalike websites or spoofed email domains that mimic the company
- False press releases or investor updates that were never actually sent
- AI-generated voice messages or deepfake videos that sound or look like real leaders
Impersonation itself isn’t new. But the tools behind it are now significantly more sophisticated — and accessible to a broader range of actors.
Learn more: How to Spot and Take Down Fake LinkedIn Accounts.
This is how easily a fake image can be created…
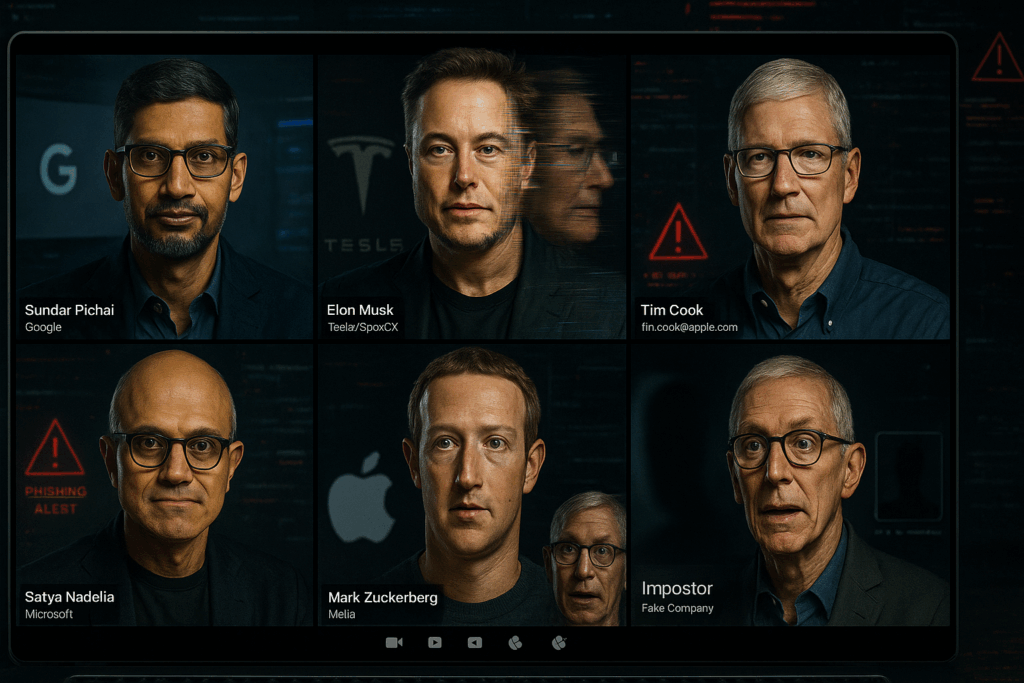
Why Are Executives Prime Targets?
Executives are highly attractive targets for impersonation because of a rare combination: they’re influential, visible, and trusted. These characteristics make impersonations highly believable and potentially damaging.
Here is a list of the reasons why executives are such a good target for cybercriminals.
1. High Authority = High Impact
Executives can authorize payments, grant access, and trigger major decisions. A message that seems to come from them is often acted on quickly — especially in time-sensitive situations.
2. Access to Confidential Information
Leaders are often involved in sensitive topics, such as mergers, layoffs, budgeting, or legal matters. That makes them useful identities for attackers who want to gain access to privileged or internal conversations.
If those conversations are leaked or exposed online, they become even more valuable, which is why Digital Risk Protection (DRP), including data leak detection, plays a key role in protecting your leaders.
3. Public Visibility
Executive names, job titles, photos, and speaking engagements are often available online — sometimes with video or audio clips. All of this can be scraped, copied, or reused to create convincing impersonations or AI-generated content.
4. Busy Schedules, Lower Scrutiny
Executives and their assistants are under pressure. They deal with fast-moving requests all day. Attackers rely on this environment — where urgency can override verification — to slip through undetected.
5. They’re Active on Social Media
They’re active on social media: LinkedIn profiles, Twitter accounts, podcasts, interviews — all of this is free research for attackers. It helps them craft messages that sound authentic.

Plus, there’s one more reason this tactic works so well: people don’t expect it.
Most employees aren’t trained to question a message from their CEO or CMO. Attackers know this. They exploit that trust — and the fear of pushing back on leadership — to get what they want.
What’s Changed: Emerging Executive Impersonation Tactics
Executive impersonation threats have evolved. They’re no longer clumsy or easy to spot. Thanks to new tools, these attacks now feel more real — and harder to detect.
Here’s what’s changed:
1. Voice Cloning
Public audio clips — from a podcast, keynote, or panel — can be used to generate realistic speech that sounds exactly like a specific executive. Attackers use this to leave voicemails, send fake voice notes, or even run live scam calls that sound like the real person.
These aren’t robotic-sounding clips. They’re natural, emotional, and extremely accurate.
2. Deepfake Video
Deepfakes are synthetic videos built from public footage — and they’re getting better fast. It’s now possible to create clips that show an executive saying things they never actually said.
These can be used to fake virtual meeting appearances, deliver fraudulent “internal” updates, or even sway investor sentiment.
The scariest part?
Many of these fakes look so good that you couldn’t tell they are fake.
Did you see this?

3. Expanded Digital Footprints
Executives leave behind a wide trail of online content: interviews, articles, biographies, social posts, and press releases. That digital footprint becomes raw material for impersonators — and the more visible a leader is, the more realistic the impersonation can be.
4. Lowered Detection Barriers
Today’s impersonations are good enough to bypass gut checks. Even trained teams may not spot a fake if the message or content feels “on brand.” These threats don’t rely on hacking — they rely on feeling real.
In short: Executive impersonation has become scalable. What once required a skilled attacker can now be done with off-the-shelf tools — often in minutes. And that means these threats are no longer rare. They’re repeatable.
Learn more: The Future of Digital Risk Protection
How Do Executive Impersonation Attacks Actually Work?
While every case is a little different, most executive impersonation attacks follow a similar path. It’s calculated, not random — and often starts with research.
Here’s how these attacks usually unfold:
1. Choose a target
The attacker picks someone inside the company with access to money, sensitive data, or systems. This is often someone in finance, legal, HR, or IT.
2. Do the homework
They gather public information about the target, such as job role, reporting structure, and vendor relationships. LinkedIn, company websites, press releases, and social media provide everything they need.
3. Pick an executive to impersonate
Next, they select a leader who has authority over the target. They study how that person communicates — tone, timing, phrases — and mimic it.
4. Create a believable channel
Attackers often use spoofed email addresses, fake domains, or even compromised accounts to make their outreach look legitimate.
5. Make the ask
This is where it all comes together. The attacker sends a request that seems routine — a wire transfer, a document, login credentials — but it’s crafted to sound urgent and familiar.
In some cases, attackers gain access to a real executive’s inbox first. They read through old threads, understand context, and pick their moment. This makes the outreach feel personal — and dangerous.
Common Examples of Executive Impersonation Attacks
Executive impersonation isn’t a single tactic. It shows up in a range of scams — all rooted in credibility.
Here are some of the most common examples:
1. Executive Impersonation or CEO Fraud
An attacker poses as the CEO and emails someone in finance with a request for an urgent wire transfer. It’s short, direct, and often tied to a fake “confidential” project or deal.

2. Business Email Compromise (BEC)
This happens when attackers send emails that look like they come from executives — asking for sensitive information, document access, or financial action. BEC often involves spoofed domains or hijacked inboxes.
3. Account Takeover
The attacker gains access to a real email or messaging account and sends messages to employees, partners, or vendors. Because it’s a real account, trust is high — and suspicion is low.
4. Supply Chain Fraud
Attackers impersonate an executive from a trusted vendor. They use real purchase history, invoice formats, or past conversations to request payment or data.
5. Spoofing
Attackers fake the sender’s identity to make emails look like they come from a trusted executive. This can include faking names, email addresses, and even copying existing threads to slip past filters and fool recipients.
Why these work:
All of these attacks rely on the same thing — believability.
If the request sounds right, looks right, and comes from the “right” person, it often gets through. And the more visible your executive is online, the more convincing these impersonations can become.
Takedowns are often the fastest way to shut these profiles down. Here’s how.
Potential Impacts of Executive Impersonation
Executive impersonation can create real problems for organizations, from minor confusion to large-scale disruption, especially when it goes unnoticed.
Here’s what’s at risk:
- Financial exposure: Impersonated emails or messages can lead to unauthorized payments, access to internal systems, or stolen credentials.
- Miscommunication across teams: When employees receive convincing messages that appear to come from leadership, they may act on them without question — especially in fast-paced environments.
- Damage to brand and reputation: False announcements or public-facing impersonation attacks can undermine confidence in the company’s brand and create confusion with investors, partners, and customers. By the way, check out this article to learn more about brand protection.
- Loss of trust from stakeholders: Leadership trust is built on clarity and authenticity. If attackers start mimicking executive voices or profiles, it raises questions about what’s real — and what isn’t.
- Operational risk during key moments: Major events like M&A activity, restructuring, or earnings calls leave little room for error. Impersonation attacks during these times can derail communication and introduce unnecessary risk.

Even a single impersonation attempt — successful or not — can cause internal friction, delay decisions, or raise doubts across the organization. Over time, that adds up.
How Organizations Can Respond
Executive impersonation affects more than just security teams. It touches communication, reputation, and customer trust. That’s why response plans need to be cross-functional — not siloed.
Here are a few steps that make a real difference:
1. Audit What’s Public
Start with visibility. Review what’s publicly available about your executives — their bios, videos, interviews, social media, and mentions across the web. Know what attackers can see and use. You can think of attack surface management tools to help you with this.
2. Limit Overexposure
Avoid sharing sensitive personal or professional details unnecessarily (this can be used for doxing). Update bios and press kits with care. The less attackers can grab, the harder it is to build a convincing fake.
3. Train Internal Teams
Help teams — especially those in finance, HR, and IT — recognize the signs of impersonation. Teach them to pause and verify requests, even if they appear to come from leadership.
4. Add Verification Steps
Set clear rules for how high-risk or sensitive requests get approved. Simple practices like multi-channel confirmation or call-backs can stop a bad request in its tracks.
5. Build an Escalation Path
Make sure people know what to do if they spot something off. Include security, legal, comms, and leadership in a defined response plan for impersonation threats.
6. Monitor and Act
Use monitoring tools to track executive mentions, fake profiles, lookalike domains, or leaked content. And if you find something, take action quickly with an integrated takedown process.
This kind of real-time visibility and response is central to a complete Digital Risk Protection strategy.
Final Thoughts
The lines between real and fake communication are increasingly blurred—especially for executives in the public eye. Impersonation attacks are no longer clumsy or obvious. In many cases, they are subtle, well-researched, and alarmingly convincing.
Protecting executives now means protecting their digital identity — not just their physical presence. That includes their voice, image, and how they’re seen or heard online.
A strong response doesn’t start after something goes wrong. It starts with awareness, a plan, and the right tools to detect and act early.
One question every company should be asking:
If someone tried to impersonate your CEO today, would you know?
Book a demo to see how Styx helps protect your executives from impersonation, data leaks, and digital threats — all in one platform.