What Does Doxing Mean?
Doxing (sometimes spelled doxxing) is the deliberate collection and release of someone’s personal information without consent to apply pressure, cause harm, or gain leverage. The harm isn’t just that details are public… It’s that an attacker packages them, adds context, and pushes them to an audience that will act on them.
Doxing in plain English
In practice, doxing means someone assembles a profile of you, including names, numbers, addresses, family links, photos, account clues, and publishes it to intimidate, embarrass, extort, or invite harassment.
It often targets people with visible roles: executives, journalists, creators, activists, and their families.
What gets exposed (and why it’s riskier together)
On their own, many data points feel harmless. Combined, they map your life and give attackers ready-made pretexts.
This is what gest exposed:
- Where you can be reached: Home/work addresses, personal email, and mobile.
- Who is connected to you: Spouse and kids, assistants, close colleagues.
- How to get into accounts: Old usernames, recovery emails, security-question answers pulled from posts and bios.
One post with a boarding pass, an old resume PDF, and a public people-search listing can be enough for targeted harassment, or an account takeover.
Where doxers pull it from
Attackers rarely need fancy tools. They mine what’s already visible, scrape what brokers sell, and add leaked credentials for scale.
- Public sources: Social posts, comments, event agendas, press mentions, property and corporate records.
- Data brokers and people-search sites: Address history, phones, relatives, past jobs—bundled and resold. Learn more about data brokers and how to remove your data here.
- Breach/leak material: Exposed passwords tied to personal or work email that unlock more accounts and inboxes. Take a look at our guide to Data Leakage here.
If domain privacy is off, WHOIS can reveal contact details. PDFs often carry hidden metadata. Photos may include location info if you didn’t strip it.
Why people dox
Motives vary, but the playbook is consistent: gather, publish, pressure.
These are some of the reasons:
- Retaliation or intimidation after a dispute or public stance.
- Leverage for money or access (extortion, social engineering, wire fraud setup).
- Collateral pressure by targeting family members or staff to force a response.
Executives see this most around high-stakes moments such as earnings, layoffs, M&A, public controversies… basically, when emotions run high and attention is focused.
Is doxing a crime?
It depends on the jurisdiction, what was shared, and how it’s used.
Publishing public facts isn’t always illegal; using those facts to threaten, stalk, incite harassment, or facilitate fraud can cross criminal lines.
Platforms generally ban doxing and remove it when reported with clear evidence.
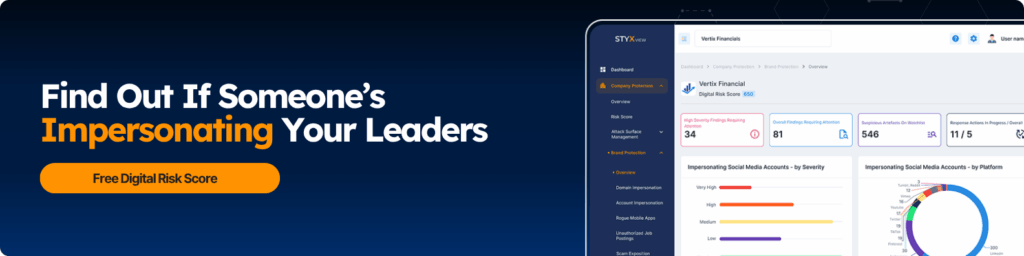
Executive Doxing: Why Leaders and Families Are Prime Targets
Executives carry visibility, authority, and access… three levers doxers can exploit. When your name is on earnings calls, press quotes, or social posts, attackers don’t need to guess where pressure will land.
They collect what’s public, stitch it to what’s leaked, and use that package to force a response from you or your company.
Visibility creates leverage
Public roles attract attention, and attention converts to pressure. Doxers look for moments when your visibility is already high.
- News cycles amplify harm: Earnings, layoffs, deals, or controversy make any leaked detail travel faster and hit harder.
- Titles confer credibility: A “CEO” or “Head of Finance” label makes fake outreach, invoices, or “urgent requests” more believable.
- Search equity cuts both ways: Your official bios, interviews, and talks make it easy to map where you are and who to contact.
Family and staff widen the attack surface
Attackers don’t always go straight at you. They go through people around you who manage calendars, payments, and posts.
Doxers go after:
- Assistants and Chiefs of Staff: Inbox rules, vendor logins, and scheduling tools become entry points for social engineering.
- Spouses and older kids: People-search sites list addresses, phones, and schools that fuel harassment or identity fraud.
- Vendors and advisors: PR, recruiters, and wealth managers often appear in public threads—useful pretexts for impostors. Learn more about Third-Party Risk Management here.
(If you support a leader, see Executive Protection Hygiene: The Playbook for baseline setups you can implement in under an hour.)
From online exposure to real-world risk
Doxing blurs digital and physical. Once home addresses, routines, or license plates circulate, threats can move offline.
- Location clues compound: Photos, event badges, and check-ins reveal patterns even if each post looks harmless.
- Collateral pressure: Publishing family details invites harassment meant to force a statement, payment, or policy change.
- Copycat loops: One post spawns mirrors across forums and socials, making takedowns slower and stress higher.
Doxers link it to fraud and social engineering
Doxing is rarely the end goal. It’s a force multiplier for scams that need context and credibility.
- Pretext building: Accurate names, roles, and vendor history make fake invoices and “verification” calls hard to spot. Here you have common social engineering tactics you should know.
- Account recovery abuse: Exposed emails, birthdays, or old addresses help attackers pass weak recovery checks.
- Executive impersonation: Cloned profiles armed with real details convince staff, partners, or media to act on bogus requests.
The pattern is predictable: collect, publish, pressure, then monetize the confusion. Your best move is to reduce the easy data, train the inner circle, and monitor for exposure so you can act before a post becomes a crisis.

How Doxing Affects Executives And Their Families
When someone drops private details about a leader, the impact spills from the boardroom into the home. It changes how families move, how assistants work, and how teams make decisions.
Here’s what it looks like in practice.
- Home Exposure: Addresses, school routes, and routines circulate, increasing unwanted contact and stalker risk.
- Targeted Harassment: Phone numbers and personal emails fuel call floods, message raids, and threats that disrupt sleep and work.
- Account Takeovers: Leaked emails, recovery details, or carrier data enable SIM swaps and resets that lock people out of critical accounts.
- Financial Pressure: Bank, brokerage, or crypto handles become lures for social engineering and wire fraud.
- Operational Disruption: Assistants, IR, and comms shift to crisis mode—vetting calls, filtering DMs, and coordinating takedowns instead of planned work.
- Reputation Damage: Screenshots travel fast; misinformation frames narratives before your team can respond.
- Family Stress: Spouses and older kids see their names, photos, and locations republished; safety practices have to change overnight.
- Follow-On Attacks: Doxed details feed phishing, BEC, and deepfake voice/video that “sound like” the executive to staff or partners.
The Growth of Doxing: What’s Changed (2019–2025)
Doxing didn’t explode by accident. Three trends made it easier, faster, and louder. If you lead security, comms, or an executive office, this context explains why basic hygiene isn’t enough anymore.
1. More personal data in the open
Your team puts more life online than five years ago. Attackers don’t need to hack when search and scrape work.
- Public bios, conference agendas, and investor decks expose roles, emails, and travel.
- People-search sites and data brokers republish addresses, phones, and family links.
- Breach dumps and paste sites add old passwords and recovery details to the mix. Early warnings come from dark web monitoring.
2. Cheaper tooling for attackers
What used to take hours now takes minutes. Low-cost tools turn scattered details into a profile.
- Face and voice cloning kits help impostors “sound” like leadership.
- OSINT scrapers pull names, photos, and posts from multiple platforms at once.
- Automated alerts flag new mentions of an executive faster than manual searches.
3. Faster amplification and coordination
Once data lands online, it travels. A single post can jump platforms and pull in strangers.
- Screenshots move from forums to social media in minutes.
- Comment raids and brigading drive attention and keep content alive.
- Lookalike accounts echo the dox, pushing harassment into DMs and inboxes.
4. Blurred lines: legality and enforcement
Is doxing a crime? It depends on what’s shared, how it was obtained, and where you live. Platforms remove harmful posts, but response times vary.
- Some disclosures may fall under harassment, stalking, or threats; others may not.
- Takedowns work best with clear evidence, multiple reports, and a paper trail.
- Without monitoring, you learn about a dox from a journalist or a family text—too late.
The takeaway: exposure scales now. Plan for early detection, quick evidence capture, and a path to removal, not just stronger passwords.
Ways To Avoid Getting Doxed (Least Effort, Highest Impact)
You don’t need a full-time opsec routine. A few habits cut most risk and still let you live online. Start with what shows in public, then harden the accounts attackers try first.
1. Tighten what’s public
Small edits remove the easy wins doxers use.
- Profiles: Hide phone, personal email, birthday, and home city on social profiles.
- Posts: Share travel and family photos after the fact, not in real time.
- Connections: Make friends/connection lists private to block target maps.
- Data Brokers: Remove home addresses and numbers from major people-search sites; recheck quarterly. Your team can follow the steps in our Executive Protection Hygiene playbook.
2. Harden the logins
Most doxing damage starts with an account reset or takeover.
- MFA Everywhere: Use an authenticator app or passkeys; keep backup codes offline.
- Password Manager: Unique, long passwords so one leak doesn’t unlock the rest.
- Recovery Paths: Update backup email/phone; add a carrier PIN to prevent SIM swaps.
- Login Alerts: Turn on new-device and password-change notifications.
3. Shrink the breadcrumbs
Reduce the clues that tie identities and locations together.
- Usernames: Vary handles across forums and social; avoid reusing the same alias.
- Domains: Enable WHOIS privacy on personal domains.
- Documents: Remove personal contact info from resumes, decks, and press bios.
- Apps & Quizzes: Skip third-party quizzes and revoke app permissions you don’t use.
4. Protect the inner circle
Attackers often go through assistants or family first.
- Shared Rules: MFA, password manager, and privacy settings for spouses and older kids.
- Message Limits: Restrict who can DM/tag; review message requests weekly.
- Verify Requests: For money, credentials, or “urgent” asks, confirm on a known number before acting.

If you want a simple, printable routine, hand your team the Executive Protection Hygiene playbook and start with MFA, a password manager, and broker removals. That alone blocks most doxing attempts.
What To Do If You’re Doxed (First 24–48 Hours)
Don’t think of a perfect plan, you just need a calm sequence: protect people, preserve evidence, contain the spread, and lock down accounts. Keep one person driving communications so nothing gets missed.
0–2 hours: safety and signal
Start with physical safety, then pick a single channel for updates.
- Immediate Safety: If threats mention your home, kids, or show weapons, call local law enforcement. Ask for a patrol drive-by and note the incident number. Tell building or neighbourhood security.
- Single Point Of Contact: Route everything through one inbox or Slack channel (assistant, security, or comms). Don’t engage with harassers; capture, don’t reply.
Collect proof, then push for takedowns
You’ll need clean evidence for platforms, search engines, and — if it escalates — police.
- Evidence Pack: Full URL, screenshots of posts and profiles, timestamps, and any DMs. Include handles, post IDs, and where it was shared.
- Platform Reports: Use each site’s impersonation/harassment form. Prioritize posts that expose home address, numbers, kids’ schools, or financial data.
- Search Removal: File “remove personal information” requests with major search engines to limit amplification during the takedown process. Learn more about What’s a Takedown.
- Mirror Hunt: Expect reposts. Search for your name + phone + address variants. Log every URL in a simple tracker. Pair with Social Media Monitoring.
Lock down accounts before they’re abused
Doxing often leads to takeover attempts and SIM swaps. Close the easy paths.
- Password Resets: Email, mobile carrier, Apple/Google/Microsoft, social, bank. Use your password manager to generate long, unique credentials.
- MFA Review: Switch to an authenticator app or passkeys, store backup codes offline, remove old devices.
- Carrier Protections: Add a port-out lock and account PIN.
- Email Hygiene: Check for unknown forwarding rules and app passwords; remove anything you didn’t set.
- Credit Protections: Place a fraud alert or freeze with your local bureaus if financial data leaked. Monitor statements closely.
Contain what’s already out there
Cut the most damaging exposure first so it can’t be reused.
- Phone And Email: If your personal number is posted and harassment spikes, forward to a new number, then migrate slowly. Set voicemail PINs.
- Address Exposure: Remove listings on top data-broker sites; switch public filings (where allowed) to a PO box or office address.
- Profiles And Bios: Strip personal contact details from resumes, press bios, and personal sites until the dust settles.
Tell the right people
Short, factual, and useful beats silence or long statements.
- Inner Circle: Family, EA, security, HR, legal. Share the evidence pack, the official contact path, and what not to do (don’t reply, don’t amplify).
- Public Note (If Needed): One post from your verified account or company page: you’re aware, do not engage with unsolicited messages, and official contact paths are X and Y. No screenshots of the dox itself.
Law, policy, and when to escalate
Laws vary by country and state. Some doxing behaviour becomes criminal when it crosses into threats, stalking, or identity theft.
- When To Involve Authorities: Credible threats, swatting risks, child data, or financial fraud. Provide your evidence pack and platform case IDs.
- Counsel: Ask legal to file preservation requests with platforms so content and logs aren’t lost during review.
After 24–48 hours: stabilize and watch
- Recheck Takedowns: Close out open reports, chase mirrors, and add new search terms to your tracker.
- Tighten Privacy: Revisit social privacy settings and connection visibility.
- Short Postmortem: What leaked, where it came from, which controls change now. Assign owners.
- Lightweight Monitoring: Set alerts for your name, address, and numbers, and enable leaked-credential monitoring on your primary emails. If you support an executive, fold this into the Executive Protection Hygiene routine.
6) What Is Doxing Monitoring?
Doxing monitoring is continuous tracking of places where your personal data can surface, not just social media, but people-search sites, public records, breach forums, paste sites, and invite-only channels.
The goal is simple: spot exposure tied to a person (or executive and their household), deliver proof you can act on, and help you contain it before it spreads.
What it watches
- Surface Web: Public profiles, posts, replies, comments, news, forums, cached pages, and screenshot archives.
- Data Brokers & Records: People-search sites, property records, corporate filings, WHOIS, court and licensing databases.
- Deep/Dark Web: Breach dumps, credential lists, marketplaces, forums, Telegram/Discord channels, paste sites.
- Assets You Control: Company sites, PDFs, code repos, job posts, and marketing files that may leak personal details.
- Signals Around You: Lookalike domains, scam ads, and impersonation patterns that reuse doxed data. Learn more about Brand Impersonation Takedowns here.
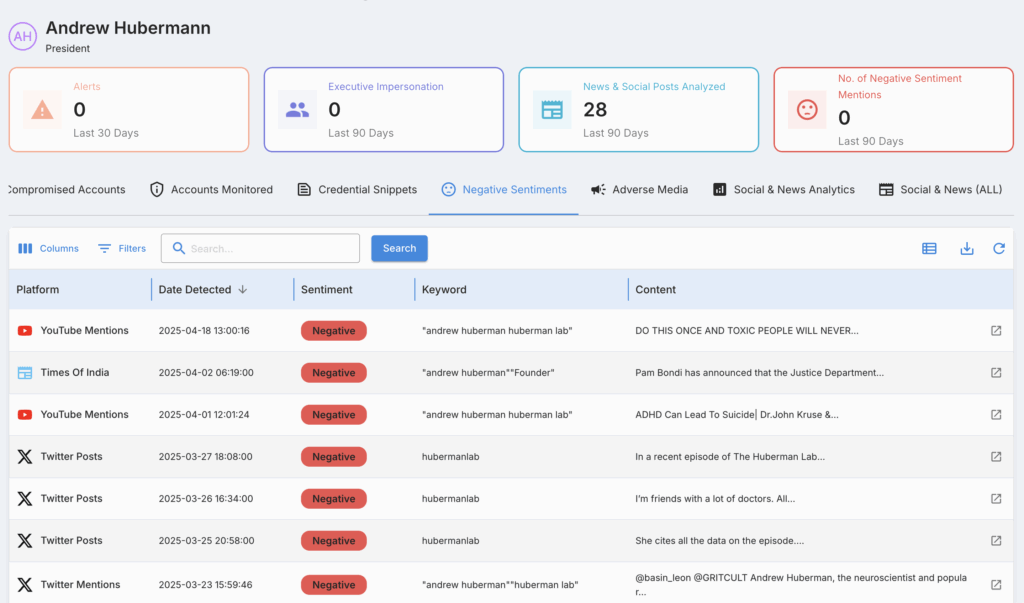
How it works
Platforms run targeted queries for names, known aliases, emails, phone numbers, addresses, handles, and images, plus variations and misspellings.
Good systems add transliterations, homoglyphs, and fuzzy matches; correlate hits across sources; then score severity based on sensitivity (home address vs. public work bio), reach, and signs of harm.
Each alert should come with evidence (URL, screenshots, timestamps) and a next action (report, remove, notify, lock down).
What it isn’t
- Not social listening: Brand mentions are useful; doxing monitoring tracks exposed PII and impersonation, which is different.
- Not credit monitoring: Credit alerts cover financial misuse; doxing monitoring surfaces the raw data that fuels it.
- Not endpoint security: It won’t patch a laptop. It reduces the public breadcrumbs attackers use.
What good output looks like
- Clear Evidence: Full URL, captures, first-seen/last-seen.
- Precise Attribution: Which person (and family member) is affected; what data is exposed.
- Actionable Next Steps: Takedown links, reporting paths, and a short playbook for containment.
- Risk Context: Sensitivity, likely misuse, and priority.
- Tracking: Case IDs, status, and time-to-removal so you can measure progress.
For leaders and public-facing teams, pair monitoring with the routines in your Executive Protection Hygiene playbook — MFA, broker opt-outs, social privacy, and a simple escalation path — so alerts turn into fast fixes.
7) Benefits of Doxing Monitoring
Doxing monitoring turns unknown exposure into a short list of actions. Instead of hunting the open web, data brokers, and private channels by hand, you get signal, proof, and a plan you can execute.
- Faster Detection: See new exposures soon after they appear across social, search, broker sites, and dark-web sources.
- Actionable Evidence: Get the URL, screenshots, timestamps, and the exact fields exposed, so you can report, remove, or lock down without guesswork.
- Risk-Based Prioritization: Alerts rank by sensitivity and reach — a home address with thousands of views beats an old cached bio — so your team works the highest-impact items first.
- Quicker Takedowns: Evidence packs and prefilled report paths help you file clean impersonation or privacy reports and track status to closure.
- Coverage For Family And Staff: Include spouses, assistants, and household info in the watchlist to cut the most common side doors into an executive.
- Less Noise, More Fixes: Integrations to Slack/Teams and ticketing route the right alert to the right owner and close the loop without extra back-and-forth.
- Measurable Results: Track time to detect, time to removal, repeat offenders, and hours saved — numbers you can share with leadership.
Pair monitoring with basic hygiene — MFA, strong passwords, broker opt-outs, and the escalation rules from your Executive Protection Hygiene: The Playbook — and you reduce the window between exposure and action.
8) How a Platform Simplifies Executive Doxing Monitoring
Manual hunting doesn’t scale. A purpose-built platform watches the places that matter, turns findings into clear actions, and closes the loop with proof and metrics. You keep focus; the system does the watching and the heavy lifting.
What It watches
- Public Web: News, blogs, social profiles, posts, and comments that expose personal details.
- Data Brokers: People-search sites that list home addresses, phones, emails, and family links.
- Dark/Web Forums: Paste sites, marketplaces, and invite-only channels where attackers trade data.
- Search Artifacts: Cached pages, mirrors, and screenshots that keep leaks alive after deletion.
How It works day-to-day
- Ingest Your Watchlist: Add executive names, common variants, family members, addresses, emails, and headshots.
- Scan Continuously: Crawl sources 24/7 with rules that match names, images, and context.
- De-Duplicate And Correlate: Merge repeats, tie items to the right person, and suppress old noise.
- Score Risk: Rank by sensitivity (home vs. work), reach, recency, and linked threats (e.g., credentials).
- Send Evidence: Deliver the URL, screenshots, timestamps, and exposed fields to the right owner.
- Track Closure: Log removals, escalations, and reversals, and watch for re-posts.
Takedown and mitigation built in
- Evidence Packs: Pre-assembled bundles with URLs, captures, and a short narrative to speed reviews.
- One-Click Reports: Prefilled forms for impersonation, privacy, and abuse on major platforms.
- Broker Opt-Outs: Autofill removal requests, verify by email, and recheck for republishing.
- Credential Actions: Flag exposed logins, push resets, and notify affected users with templates.
- Blocklists: Export lookalike domains, sender addresses, and URLs to email/web filters.
Privacy and safety controls
- Least Data Needed: Store only the identifiers required for matching; avoid full dossiers.
- Scoped Access: Limit who can see home addresses and family details; log every view.
- Consent And Audits: Capture approvals for monitoring targets and export audit trails on demand.
What to measure
- Time To Detect: Minutes/hours from exposure to alert.
- Time To Remove: Hours/days from alert to confirmed takedown.
- Repeat Rate: Percentage of sources that republish after removal.
- Coverage: Share of priority sources monitored for each executive.
- Work Saved: Manual hours replaced by automated discovery and reporting.
A good platform gives you fewer, clearer alerts with proof, faster removals, and numbers you can show leadership. You see the exposure, act on it, and move on.