Who This Is For (and What You’ll Get)
If you lead a team, manage a brand, or support an executive, this Executive Protection Hygiene playbook is for you.
The goal is simple: a hygiene routine that reduces risk at home and online without adding unnecessary work.
Learn more: Executive Protection: Securing Leaders in the Digital Age.
Who should read this
- CEOs, founders, board members
- Executive assistants and chiefs of staff
- Security, comms, and legal teams that support leadership
- Family members who share devices or accounts with an executive
What you’ll get from this guide
- Baseline setup you can do once: MFA on key accounts, a password manager, login alerts
- Social media hygiene that takes minutes and actually helps
- Posting rules that keep travel, family, and company updates safe
- Data broker removals with a simple step-by-step
- Home and device basics that prevent easy wins for attackers
- Inner circle coverage for assistants and family
- High-risk moment checks for times like earnings, M&A, or major travel
- What to automate so that a platform monitors and removes threats for you
- A quarterly checklist you can print and share
How to use it
- Pick two items to do today (MFA + password manager is a strong start).
- Share the social and data-broker sections with your assistant and family.
- Add the quarterly checklist to your calendar.
Let’s start.
Lock Down Accounts (Baseline Setup)
Do this once and you cut most of the risk. Start with the accounts attackers target first: personal email, work email, Apple/Google ID, mobile carrier, bank, and social.
1) Turn on MFA everywhere
Multi-factor authentication stops most takeovers.
Priority order
- Personal email (Gmail, Outlook, iCloud)
- Work email/SSO
- Apple ID / Google account / Microsoft account
- Mobile carrier account
- Banking and brokerage
- LinkedIn, X, Facebook, Instagram, WhatsApp
How to set it
- Go to Security or Password & Security in the account settings.
- Choose Authenticator app, passkey, or security key. Use SMS only as a fallback.
- Save backup codes and store them offline (wallet or safe).
- Add a secondary email and phone for recovery.
2) Use a password manager + long passphrases
Reused passwords are the easy way in. A manager fixes that.
Set it up
- Pick a reputable manager (1Password, Bitwarden, Dashlane, Keeper, iCloud Keychain).
- Create a long master passphrase (at least 4–5 random words).
- Turn on breach alerts (e.g., Watchtower or similar).
- Generate unique passwords for every account (16+ characters).
- Enable biometric unlock on phone and laptop.
Sharing rule
- Don’t share passwords by text or email.
- Share items or a shared vault with assistants when needed. Keep personal accounts separate.
3) Enable login alerts
You want a ping when something odd happens.
Turn on notifications for:
- New device or location login
- Password change
- Recovery settings change
- Payment or subscription changes
Do this on email, Apple/Google/Microsoft, mobile carrier, bank, and social.
4) Lock in recovery before you need it
Account recovery is where many takeovers succeed.
- Add a backup email and phone you control.
- Generate backup codes and store them offline.
- Add trusted contacts where supported (Apple, Facebook).
- Remove old recovery details you no longer use.
Quick check: try a recovery test on one account now so you know the flow.
5) Clean up old access
Reduce the places your account can be misused.
- Sign out old sessions and devices.
- Remove third-party app access you don’t use (Google/Apple/LinkedIn/X have pages for this).
- Delete duplicate or unused social accounts that look abandoned.
6) Upgrade to passkeys where possible
Many services now support passkeys (Apple, Google, Microsoft, some banks and apps).
- Turn on passkeys in account security settings.
- Keep a hardware key as a backup if you travel often.
7) Set up an assistant workflow
Assistants need access. Give it safely.
- Create a dedicated work email for approvals and vendor sign-ups.
- Use a shared vault for business passwords. Keep personal logins in a private vault.
- Use delegation features (calendar, email) instead of sharing passwords.
Done right, this section takes under an hour for a first pass. Start with personal email, Apple/Google ID, and LinkedIn. Add the rest this week.

Social Media Hygiene (Setup Once, Review Quarterly)
Attackers use what executives post. Lock down what shows, who can reach you, and what old content reveals. Do this once, then review every quarter.
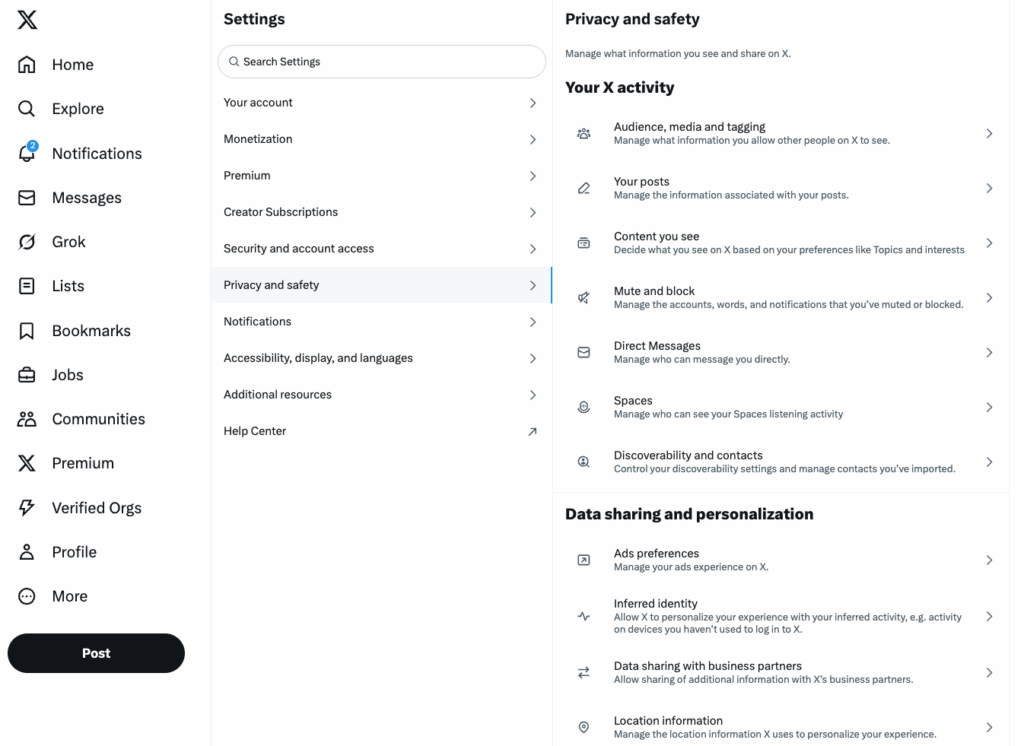
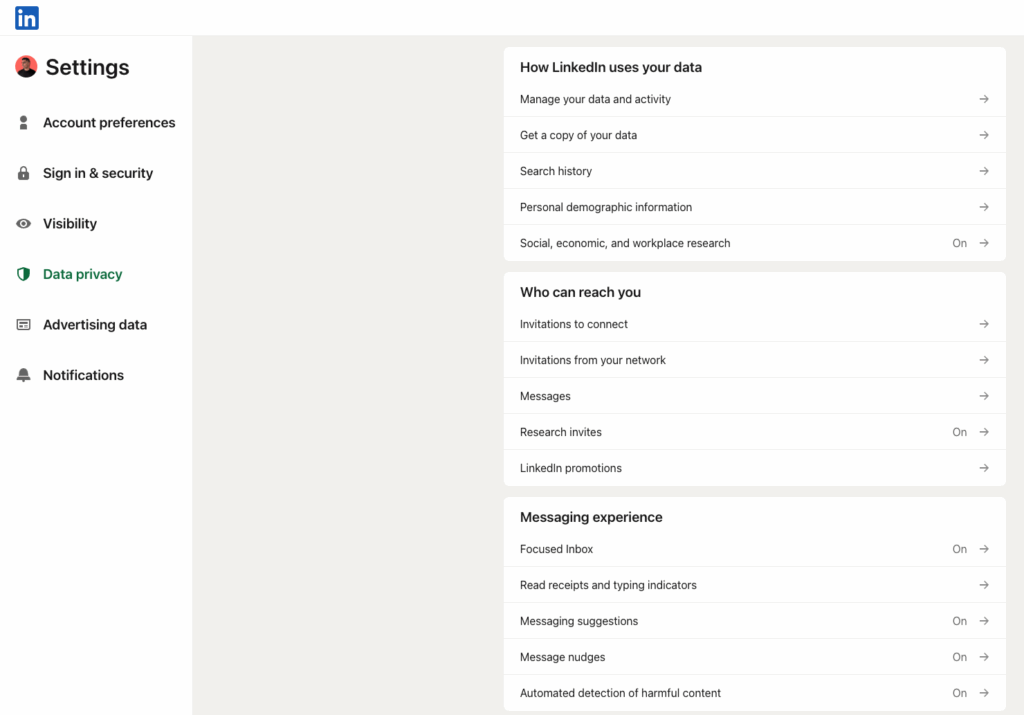
1) Run each platform’s privacy checkup
Every network has a built-in wizard. Use it to set the baseline.
- Set profile visibility to friends/contacts where possible.
- Limit who can message, mention, and tag you.
- Turn off search engine indexing of your profile (LinkedIn has this).
- Hide email, phone, and birthday from public view.
2) Hide your network
Your connections are a target map for scammers.
- Make Friends/Connections list private (Facebook supports this).
- Hide followers where the platform allows it.
- Ask close family to do the same.
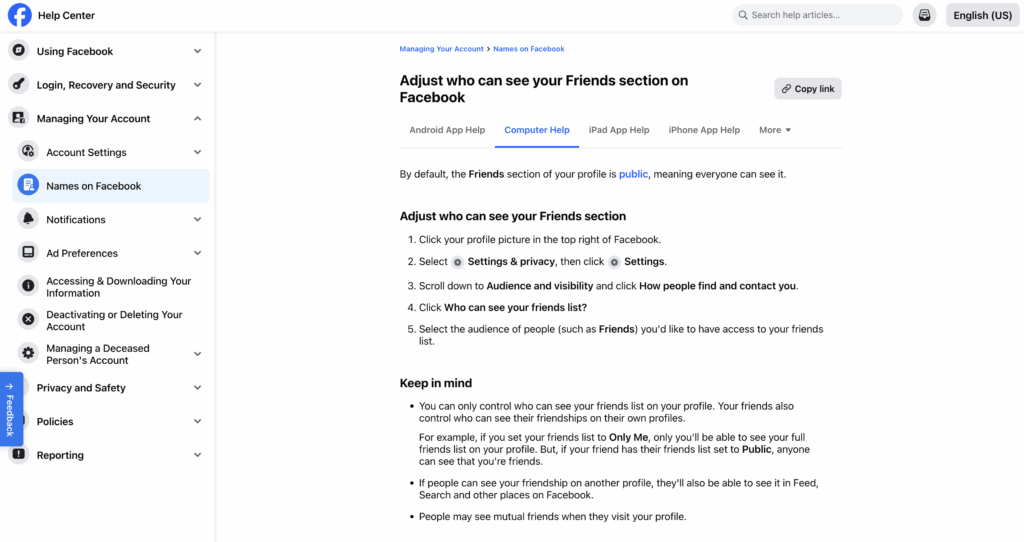
3) Clean up old posts and photos
Old content leaks travel, badges, and routines.
- Remove or hide badge photos, boarding passes, event passes, and office layouts.
- Use “Limit Past Posts” (Facebook) or set past posts to Connections only (LinkedIn).
- Delete stale accounts that look abandoned.
4) Reduce impersonation risk
Make it clear which accounts are real.
- Keep one official profile per platform. Close duplicates.
- Add a pinned post that lists your real accounts and the company’s official channels.
- Reserve obvious handle variations to block impostors.
5) Control who can reach you
Cut spam and lures at the source.
- Restrict DMs to people you follow or connections.
- Require approval for tags and photo reviews.
- Limit comments on public posts to followers or connections.
- Filter message requests; block unknown link senders.
6) Review app and ad access
Third-party tools often hold extra permissions.
- Remove apps you don’t use from LinkedIn, Facebook, and X.
- Review advertiser audiences; opt out where possible.
- Disable sharing of contact lists with platforms.
7) Security on social accounts
Yes, this overlaps with account lockdown; it matters here, too.
- Turn on two-factor authentication (authenticator app, passkey, or security key).
- Enable new login alerts and password change alerts.
- Store backup codes offline.
8) Quarterly review (5-minute checklist)
- Re-run each platform’s privacy checkup.
- Re-limit past posts.
- Recheck friends/connection visibility.
- Remove new third-party apps you no longer need.
- Scan profiles for old photos that give away travel or access.
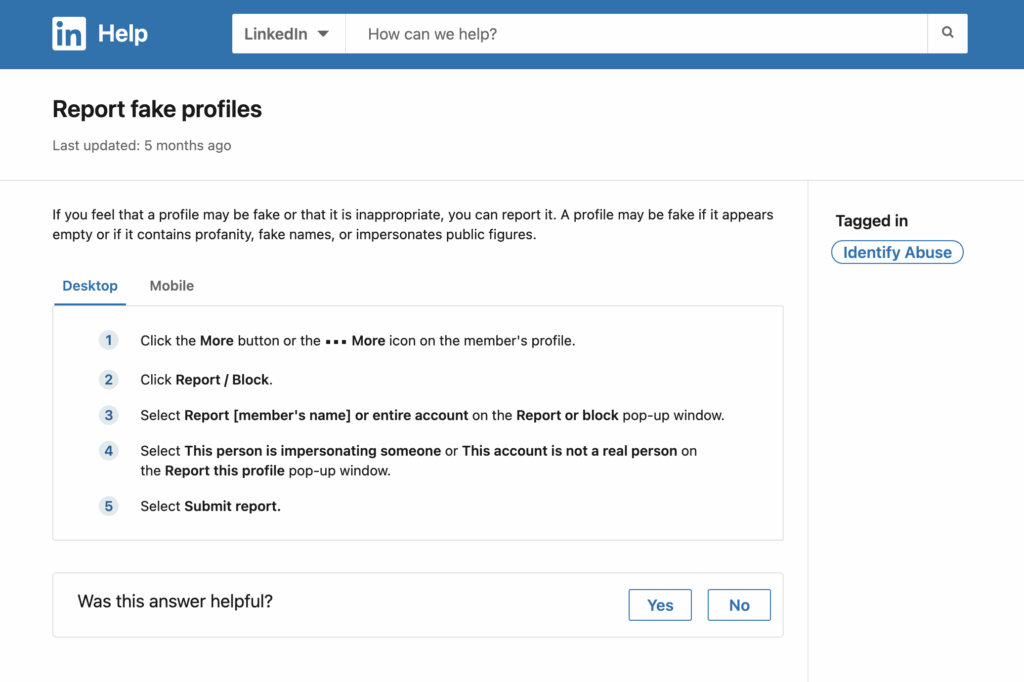
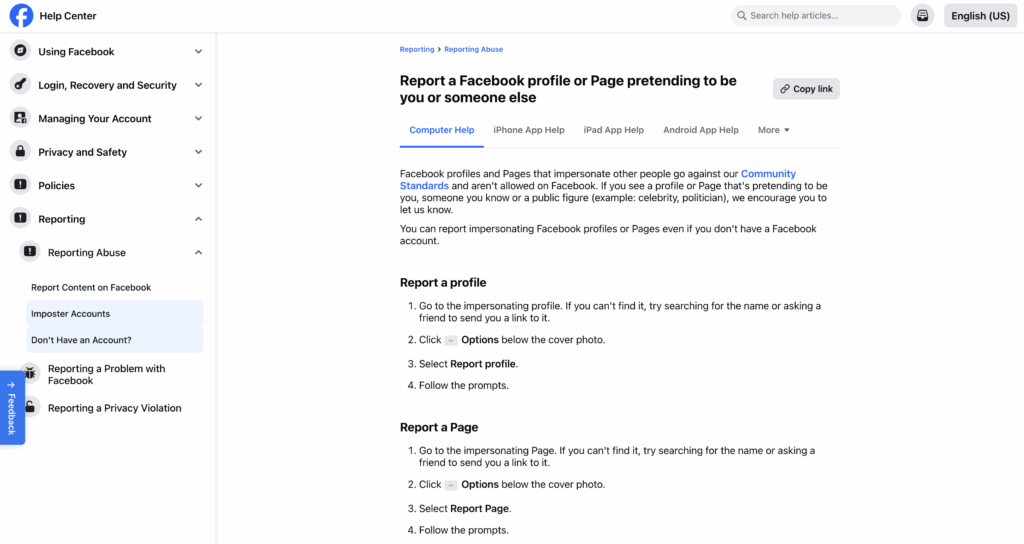
9) If you spot an impersonator
Move fast and keep proof.
- Capture URL and screenshots.
- Report on the platform (impersonation/fake account).
- Warn your network with a short post (no links to the fake).
- File a takedown through your security/comms team or platform tools.
Keep this simple. Privacy checkups, hidden networks, clean history, tight contact settings, and basic security stop most social scams before they start.
Posting Rules (Everyday Habits)
Attackers build scams from small details. Good habits cut that off. Share these rules with assistants and family; they use the same apps and get targeted too.
What to post — and when
- Post travel after you leave
- Why: live location makes stalking and social engineering easier.
- Keep personal and company updates separate
- Why: mixed posts blur what’s official and give scammers more to copy.
- Avoid real-time photos from home, school, or routine spots
- Why: backgrounds reveal addresses, schedules, and family patterns.
Photos to avoid (or edit first)
- Badges, boarding passes, event passes
- Crop or blur. Barcodes and names get abused.
- Screens with emails, dashboards, or call logs
- Even a small reflection can leak names and projects.
- New gear, cars, or high-value items at home
- It signals what to steal and where.
Limit who can contact you
- Close DMs to contacts only
- Why: open DMs invite lures and fake “support” accounts.
- Require tag and mention approval
- Why: stops impostors from tagging you into scams.
- Filter comments
- Allow followers or connections only on public posts.
Links and messages
- Hover on links; avoid random shorteners and QR codes
- If you must share, use the full URL.
- Treat “urgent” or “confidential” requests as suspicious
- Verify on a known channel before you act — especially money, documents, or access.
- Don’t move chats to WhatsApp/Telegram on a stranger’s ask
- That’s a common handoff for scams.
Keep work clear and official
- Pin a post with your real accounts and approved contact paths
- Helps others spot fakes.
- Use company pages for offers, hiring, and support
- Don’t announce these from personal profiles.
- If media or investors reach out by DM, switch to official email
- Reduces spoofing.
Cleanups to do weekly (2 minutes)
- Remove new third-party app permissions you don’t use.
- Clear unknown message requests.
- Unfollow/block impostors and report them.
If you slip and post something sensitive
- Delete the post.
- Screenshot it for your security team.
- Warn likely targets (assistant, comms, IT).
- Watch for spoofed messages that reuse the details you exposed.
Keep these habits tight and simple. You’ll share what you want, without handing scammers the rest.
Remove Your Info from Data Brokers (Step-by-Step)
Data broker sites publish home addresses, personal emails, phone numbers, family links, and old jobs. Attackers use this to build scams, guess logins, and target families through doxing. Clean it up once, then keep it tidy.
What to remove first
- Home address(es) and phone numbers
- Personal emails (and old work emails)
- Family names and relationships
- Photos tied to your name
- Old jobs and education that help with impersonation
Step 1: Find your profiles
Search the obvious first. Do this for the executive and close family.
- Google:
Full Name+ city,Full Name+ “address”, phone number, personal email - Common sites: Whitepages, Spokeo, BeenVerified, TruthFinder, Radaris, PeopleFinder, Intelius, RocketReach, ZoomInfo
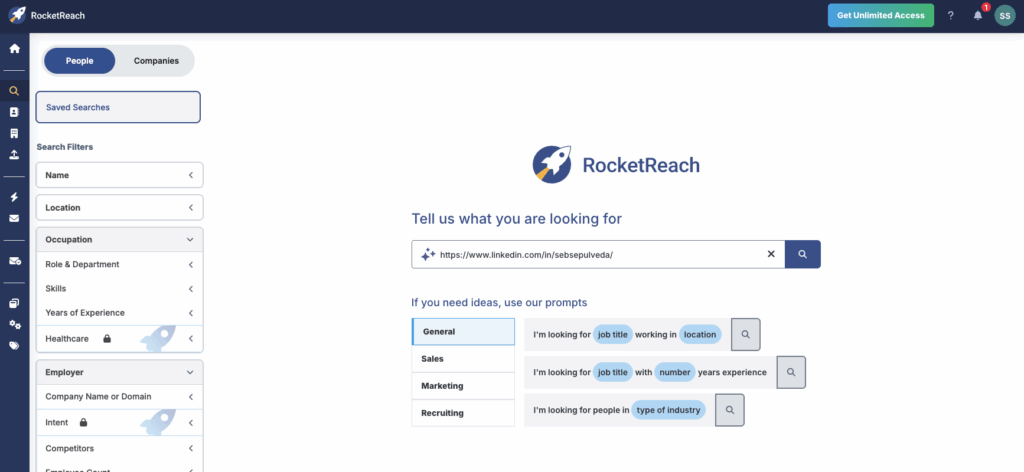
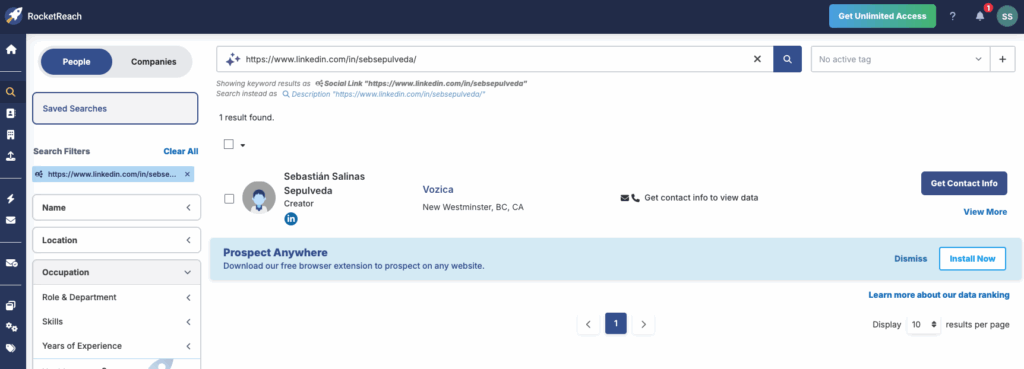
Step 2: Open the profile and copy the URL
You’ll need the exact page link for the opt-out form.
- Save each profile URL in a simple tracker (Sheet/Notes). Columns: Site, Profile URL, Opt-out URL, Requested date, Status, Follow-up date
Tip: I can give you a sheet template if you want one.
Step 3: Use each site’s opt-out (don’t email random support)
Almost every broker has a removal form. Use it.
- Find “Opt-Out,” “Remove Listing,” or “Do Not Sell My Info” (bottom/footer).
- Paste the profile URL.
- Confirm by email (they’ll send a link).
- Set a 7-day reminder to check that it’s gone.
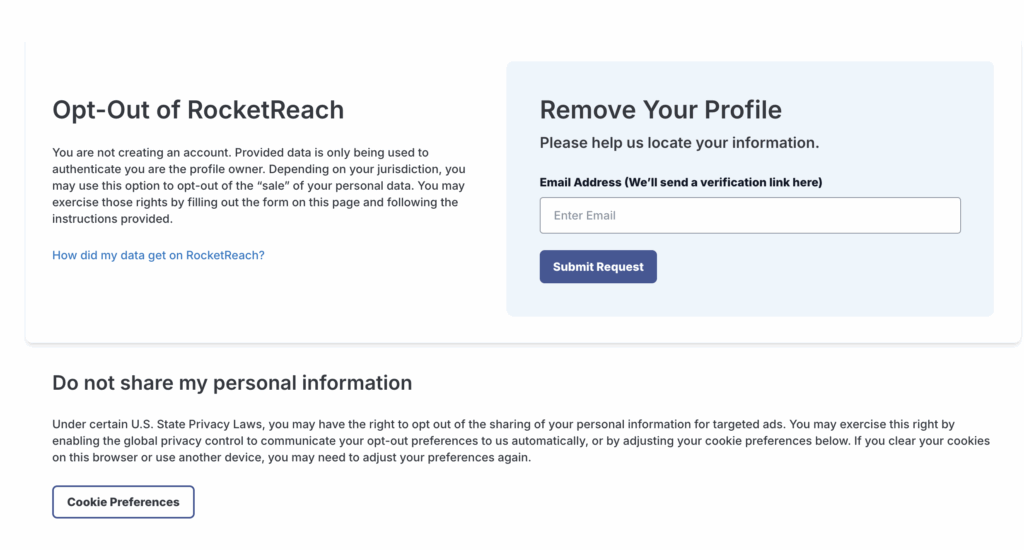
Step 4: Verify identity safely (some sites ask for it)
A few brokers ask for ID to prove it’s you.
- If you must upload ID, cover the photo and ID number, leave name and address visible.
- Never send a full SSN.
- Use a dedicated email for removals (not your primary address).
Step 5: Recheck and escalate
Seven days later:
- Search the site again. If the page still exists, submit a second request.
- If they refuse or stall, cite local privacy laws (“Please remove my personal information under applicable privacy regulations”) and re-submit.
Step 6: Automate the long tail
Manual removal for the top 10–15 sites is worth it. For the rest, use a trusted removal service (e.g., DeleteMe, Kanary, Optery, Incogni). Still spot-check monthly at first.
Prioritize these first (they republish often)
- Whitepages
- Spokeo
- BeenVerified
- TruthFinder
- Intelius
- Radaris
- PeopleFinders
- US Search
- RocketReach
- ZoomInfo (for B2B profiles)
Extra credit that pays off
- Hide WHOIS data for any personal domains (use registrar privacy).
- Remove home location tags from recent posts.
- Update old resumes/press bios that list personal contact info.
- Switch to a PO box or office address for public filings where allowed.
Quarterly quick check (10 minutes)
- Re-search your name and phone.
- Re-submit any new listings.
- Re-run removal on sites that republish.
Bottom line: Less exposed data means fewer lures, fewer targeted scams, and fewer paths into your accounts or home life. Clean it once, then keep it light with a quick quarterly sweep.
Home and Devices (Simple but Important)
Most executive attacks start from a weak device or home network. Fix the basics once, and you remove easy wins for scammers.
1) Keep everything up to date
- Turn on auto-updates for your phone, laptop, and apps.
- Update your browser, too.
- Delete apps you don’t use.
2) Secure your Wi-Fi
- Change the router admin password from the default.
- Use WPA3 (or WPA2) and a strong Wi-Fi password.
- Turn off WPS and remote management if you don’t need them.
- Create a guest network. Put visitors and smart devices (TVs, speakers, cameras) on it.
- Name your Wi-Fi something neutral. Don’t use your last name or address.
3) Turn on device protection
- Encryption: FileVault (Mac) / BitLocker (Windows) is a must. Phones encrypt by default.
- Auto-lock: 1–2 minutes.
- Screen lock: Face ID/Touch ID + a long passcode.
- Find My / Find My Device: on, with remote wipe enabled.
- Lock screen previews: hide message previews on the lock screen.
4) Block easy account takeovers
- Set a carrier PIN/port-out lock on your mobile account. This helps stop SIM-swap fraud.
- Add a voicemail PIN if your carrier still allows access without one.
- Use an authenticator app or passkeys instead of SMS codes where possible.
5) Back up automatically
- Phones: iCloud or Google One backups on.
- Laptops: Time Machine (Mac) or Windows Backup.
- Do a quick test restore once, so you know it works.
6) Trim browser risk
- Update Chrome/Safari/Edge.
- Keep extensions to a minimum. Remove anything you don’t use.
- Block third-party cookies and pop-ups.
- In email, disable remote images to reduce tracking and lures.
7) Tighten sharing and Bluetooth
- AirDrop/Quick Share: Set to Contacts Only or Receiving Off.
- Location sharing: Review who can see you. Keep it to family only.
- Unknown trackers: On iPhone/Android, keep tracker alerts enabled.
8) Smart speakers and cameras
- Change default passwords.
- Turn off purchases by voice.
- Review cloud video retention; keep it short.
- Place cameras so they don’t capture screens, whiteboards, or documents.
9) Keep work and personal separate
- Use separate profiles or browsers for work and personal.
- Don’t sign into company tools from shared home computers.
- Avoid sharing passwords with assistants; use a shared vault instead.
10) Monthly five-minute check
- Reboot phone and laptop (clears temp access tokens).
- Check for OS/app updates.
- Scan your router for firmware updates.
- Review new devices on your Wi-Fi; remove anything you don’t recognize.
Bottom line: updates, strong Wi-Fi, encryption, backups, and short lock times stop most home-based risks. Do this once, then a quick monthly check keeps it tight.
Email and Messaging Hygiene
Most scams start in your inbox or DMs. Set a few rules and stop the easy ones.
1) Use separate addresses
- Public: for press, events, and general contact. Expect spam.
- Private: for real work and sensitive contacts. Don’t post it anywhere.
- Throwaway: for sign-ups, trials, and downloads.
Keep your private address out of public bios, filings, and slides.
2) Turn on strong protections
- MFA on email and chat apps.
- Login alerts for new devices and locations.
- Attachment scanning is on by default (most providers support this).
- Remote images off in email to reduce tracking and lures.
3) Kill risky forwarding and filters
- Review forwarding rules and filters in your email settings.
- Remove any you don’t recognize. Attackers use silent forwards to watch mail.
4) Treat “urgent” as a red flag
If a message asks for money, data, or access, verify on a known channel:
- Call a saved number.
- Reply in a new thread to a known address.
- Ask your assistant to confirm on calendar or chat.
Never approve wires, payroll changes, or gift card buys from email or DM alone.
5) Handle links and files safely
- Hover on links. If the domain looks off, don’t click.
- Avoid random short links and QR codes.
- Open unknown files in web view first (Google Drive, Office online) instead of downloading.
- For sensitive files, use your company’s approved storage, not personal drives.
6) Lock down messaging apps
- WhatsApp/Signal/Telegram: Hide profile photo from non-contacts, limit group adds, and set disappearing messages for sensitive chats.
- iMessage: Filter unknown senders; turn on Silence Junk.
- Slack/Teams: Keep external access to approved partners only.
7) Disable “login by email link” on personal accounts
Attackers abuse magic links sent to inboxes they control. Prefer authenticator codes or passkeys.
8) Shared mailboxes and assistants
- Use delegation for inboxes and calendars; don’t share passwords.
- Give assistants a shared vault for vendor logins.
- Keep a simple rule: assistants verify money and access requests with a call-back.
9) Clean your contact list
- Remove old vendors and personal emails you don’t use.
- Label VIPs so their messages stand out and are easier to verify.
10) Monthly two-minute check
- Review forwarding rules and filters.
- Check recent logins.
- Clear spam and unsubscribe from junk.
Bottom line: separate addresses, strong login protection, safe file handling, and a verify-before-you-act rule will stop most inbox and DM attacks aimed at executives.
Protect the Inner Circle (Assistants and Family)
Attackers go through the people around an executive because it’s easier. Fix the basics for assistants and family, and you cut most of that risk.
Start with the same baseline
Give them the same protection you set up in the earlier sections.
- MFA on every account (email, Apple/Google, mobile carrier, social).
- Password manager with a long passphrase.
- Login alerts for new devices and password changes.
- Backup codes saved offline.
Keep access clean and separate
Assistants need access. Do it safely.
- Use delegation for email and calendars. Don’t share passwords.
- Create a shared password vault for work logins; keep personal logins private.
- Use separate email addresses for public inquiries vs. real business.
- Limit who can post on behalf of the executive. Keep a short, approved list.
Set a verify-before-you-act rule
This one stops most scams.
- Treat urgent requests for money, credentials, or documents as suspicious.
- Call back on a saved number or use a known internal chat to verify.
- For voice notes or calls that “sound like” the exec, confirm on a second channel (calendar invite, text to a known number).
- Never change payroll, vendor bank details, or gift card buys without two-person approval.
Tighten social and privacy for the family
Small changes here go a long way.
- Make friends/connection lists private.
- Turn off location sharing with anyone outside the family.
- Post travel after the trip, not during.
- Hide or remove home photos that show addresses, schools, or routines.
- Limit who can DM and tag them on social.
Remove their data from broker sites
Attackers use family profiles for doxxing and scams.
- Search and remove listings for spouses and older kids on the top broker sites (Whitepages, Spokeo, BeenVerified, etc.).
- Use a removal service for the long tail.
- Recheck quarterly.
Lock down phones and carriers
SIM swaps and voicemail tricks hit family first.
- Add a carrier PIN/port-out lock to each line.
- Set a voicemail PIN.
- Keep Find My/Find My Device on with remote wipe.
- Use Contacts Only for AirDrop/Quick Share.
Home help and vendors
Anyone with access to the home is part of the circle.
- Give guest Wi-Fi only.
- Avoid sharing passwords; use a shared vault if needed.
- Remove access when projects end.
- Keep invoices and schedules off public channels.
Simple training for assistants (30 minutes)
- How to spot impostor accounts and fake domains.
- How to verify high-risk requests.
- How to handle attachments and links safely.
- When and how to escalate to security/comms/legal.
- Where to log evidence (screenshots, URLs, timestamps).
What “good” looks like
- No shared passwords over text or email.
- Two-person approval on money and access changes.
- Family profiles are private; location is off.
- Broker listings removed and rechecked.
- Carrier protections in place for everyone.
- Fast escalation path when something feels off.
Keep this simple and repeatable. Set it up once, share the rules, and review every quarter. That’s how you protect the people attackers target first.
High-Risk Moments Playbook
Some moments draw attackers in: big news, fast decisions, lots of eyes. Use this playbook any time risk spikes.
When risk spikes
- M&A, fundraising, layoffs, earnings, product launches
- Major travel, conferences, keynotes, media tours
- Incidents or outages, legal disputes, regulatory news
One week before: prep
- Name the channels: List the only places you’ll make official updates (site, press email, investor portal, social handles). Share this list with staff and partners.
- Assign owners: Who approves wires and access changes? Who files takedowns? Who talks to media? Write names, not teams.
- Turn on extra monitoring: Watch for fake profiles, lookalike domains, scam ads, and leaked credentials tied to the execs involved.
- Tighten social: Lock comments to followers where possible. Pin a post with your official handles and contact paths.
- Brief assistants and family: Expect impostors. Remind them to verify anything “urgent” on a known number.
- Set verification rules: Use the rules below and make sure everyone knows them.
Verification rules (use these every time)
- Money: Two-person approval. Confirm by calling a saved number. Never change bank details by email or DM.
- Access & data: No credentials or files shared by DM. Use approved company channels only.
- Voice/video: If you get a surprising call or voice note “from” the exec, confirm on a second channel (calendar invite + known number).
- Vendors: Confirm any request to change invoices or payment details with your known contact.
Day of: controls live
- Publish once, then point to it: Put the primary update on your site or press page. Link to it from social. This makes fakes easier to spot.
- Use known templates: Keep language and layout consistent so oddities stand out.
- Route finds fast: Staff and partners send suspicious links to a single inbox or Slack channel. Security/comms file takedowns from there.
- Pause risky features: Limit who can post from exec accounts. Tighten DM settings. Reduce who can comment if abuse spikes.
If you see an impersonation or fake
- Capture proof: URL, screenshots, timestamp.
- Report and remove: Use the platform’s impersonation form and your takedown workflow.
- Warn your audience: Short post from official channels: “A fake account is circulating. Official updates are here: [link].” Don’t link to the fake.
- Harden controls: Block lookalike domains at your web firewall. Limit comments/DMs if needed.
- Escalate when needed: If there’s a threat or doxxing, involve legal and law enforcement.
After: quick sweep (within 24–48 hours)
- Search for stragglers: New fakes often pop up after the first takedown.
- Reset what changed: Temporary access or extra permissions? Roll them back.
- Close the loop: Record what worked, what was noisy, and who responded. Update owners and templates.
What to Monitor Automatically
You shouldn’t hunt this by hand. A good platform watches everywhere, sends clean alerts with proof, and helps you remove the problem fast.
What it should cover
- Fake profiles and pages: Look for clones of executive accounts on LinkedIn, X, Facebook, Instagram, and YouTube. Why it matters: these drive scams and false announcements.
- Scam ads and sponsored posts: Detect ads that use executive names, photos, or the company brand. Why it matters: paid reach spreads faster than organic posts.
- Lookalike domains and sites: Spot domains that use executive or brand names with small tweaks. Track live phishing pages and login forms. Why it matters: these fool customers, vendors, and staff.
- Leaked credentials: Monitor forums, paste sites, and markets for emails and passwords tied to executives and assistants. Why it matters: one reused password leads to account takeover.
- Personal data exposure: Watch data broker sites for home addresses, phones, family links, and personal emails. Why it matters: attackers use this for doxxing and social engineering.
- Dark web mentions: Track chatter about named executives, their emails, or access for sale. Why it matters: early warning before an attack moves to the open web.
- Third-party risk: Monitor key vendors for breaches and brand abuse that name your executives. Why it matters: attackers often go through partners first.
- Active exploitation: Flag CVEs being used in the wild that match your tech stack. Why it matters: helps you patch what attackers actually target.
What a good alert includes
- The evidence: Screenshot, full URL/handle, first seen / last seen
- The target: Which executive, account, or domain it hits
- The risk: Clear severity and why it matters
- The action: Takedown, reset, block, notify — with one-click options
- The owner: Who needs to act (security, comms, legal, help desk)
What should happen next
- One-click takedowns for fake profiles, rogue apps, and phishing pages
- Credential workflows to force resets and notify users
- Blocks pushed to the right tools (email, web, endpoint)
- Case tracking so you can see status, timestamps, and results
- Integrations to email, Slack/Teams, Jira/ServiceNow, SIEM/EDR
How do you know it’s working?
- Less noise. More real issues with proof attached.
- Faster takedowns and resets (measured in hours, not days).
- Clear monthly view: time to detect, time to fix, items removed, hours saved.
Use your platform for the watching and the heavy lifting. Keep your time for decisions and the few actions that need a human.

Quarterly Hygiene Checklist (Printable)
Run this once every quarter. It keeps small issues from turning into big ones. Share it with your assistant and the security lead.
1) Accounts
- Reconfirm MFA on email, Apple/Google/Microsoft, social, bank, and carrier.
- Regenerate backup codes if you used any; store them offline.
- Review login alerts and recent sign-ins; sign out old devices.
- Remove third-party app access you don’t use (Google/Apple/LinkedIn/X).
- Rotate passwords for high-value accounts (email, bank, carrier, cloud).
2) Social Media
- Re-run each platform’s privacy checkup.
- Make friends/connections lists private.
- Limit DMs, tags, and comments to contacts/followers.
- Remove old photos that show badges, boarding passes, or home details.
- Check for impersonators; capture URLs and report any fakes.
3) Data Brokers
- Search your name, phone, and personal email.
- Re-submit opt-outs on sites that republish (Whitepages, Spokeo, BeenVerified, etc.).
- Spot-check any removal service you use; confirm listings are gone.
4) Home and Devices
- Apply OS and app updates on phone and laptop.
- Check the router for firmware updates; reboot the router and the modem.
- Review Wi-Fi devices; remove anything you don’t recognize.
- Confirm encryption (FileVault/BitLocker) and auto-lock are on.
- Verify Find My/Find My Device and remote wipe are enabled.
5) Email and messaging
- Review forwarding rules and filters; remove anything odd.
- Turn off remote images in email if it was re-enabled.
- Clean contact list; label VIPs for easy verification.
- Verify voicemail PIN and carrier port-out lock.
6) Inner circle (assistants and family)
- Confirm MFA and password manager use.
- Re-share the verify-before-you-act rule for money, access, and files.
- Check their privacy settings and location sharing.
- Run broker opt-outs for spouse/older kids if new listings appear.
7) High-risk Moments Prep
- Update the list of official channels (site, press email, social handles).
- Refresh owners for takedowns, media responses, and approvals.
- Keep a short statement template ready for impersonation alerts.
8) Platform & Monitoring
- Review alerts with evidence closed this quarter (takedowns, resets).
- Check time to detect and time to fix; note blockers.
- Add new brands, domains, and exec handles to watchlists if anything changed.
- Remove duplicates and tune false positives.
Tip: Put this checklist on a recurring calendar invite. 30–45 minutes each quarter keeps your risk low with very little effort.
Wrap Up
Executive protection hygiene isn’t complex. Do the basics once, keep simple habits, and let a platform watch the rest. That blend stops most scams before they reach the inbox, the family, or the brand.
See your leadership exposure across social media, data brokers, and the dark web, and take action before it impacts them or their families. Book a demo of Styx Intelligence.
















