What Is Social Engineering?
Social engineering is when attackers manipulate people into giving up sensitive information, clicking dangerous links, or taking actions that put systems at risk.
These attacks often look normal:
- An email from IT
- A message from your boss
- A fake login page
- A voice call that sounds legit
But behind them is someone trying to trick their way in.
Social engineering tactics are behind many of today’s biggest data breaches and financial scams. And they work… because people trust what looks familiar.
What Makes Social Engineering So Effective?
Social engineering tactics are highly effective because they target people, not systems. Attackers use basic tools, fake identities, and believable stories to get what they want. And most of the time, it works.
Here are some reasons why social engineering is so effective:
- It exploits the human element: Social engineering tactics work because they take advantage of how people naturally respond to urgency, authority, or curiosity.
- It has a low barrier of entry: A scammer just needs a fake email, a spoofed profile, or a convincing message. Anyone can do it, which makes it easy to launch at scale.
- It works across channels: Attackers don’t care how they reach you — email, text, social media, phone calls, even fake apps.
- It pays: People being manipulated send money, give up passwords, or click links that steal sensitive info. And the people behind it often walk away without getting caught.
- It leads to bigger scams: A social engineering attack can unlock everything, including credentials, access, and sensitive data. Once inside, attackers can escalate to ransomware, fraud, or system takeovers.
- It evades traditional security: These attacks don’t always involve malware or shady links. They often use real platforms, clean messages, and personal language that slips past security tools and filters.
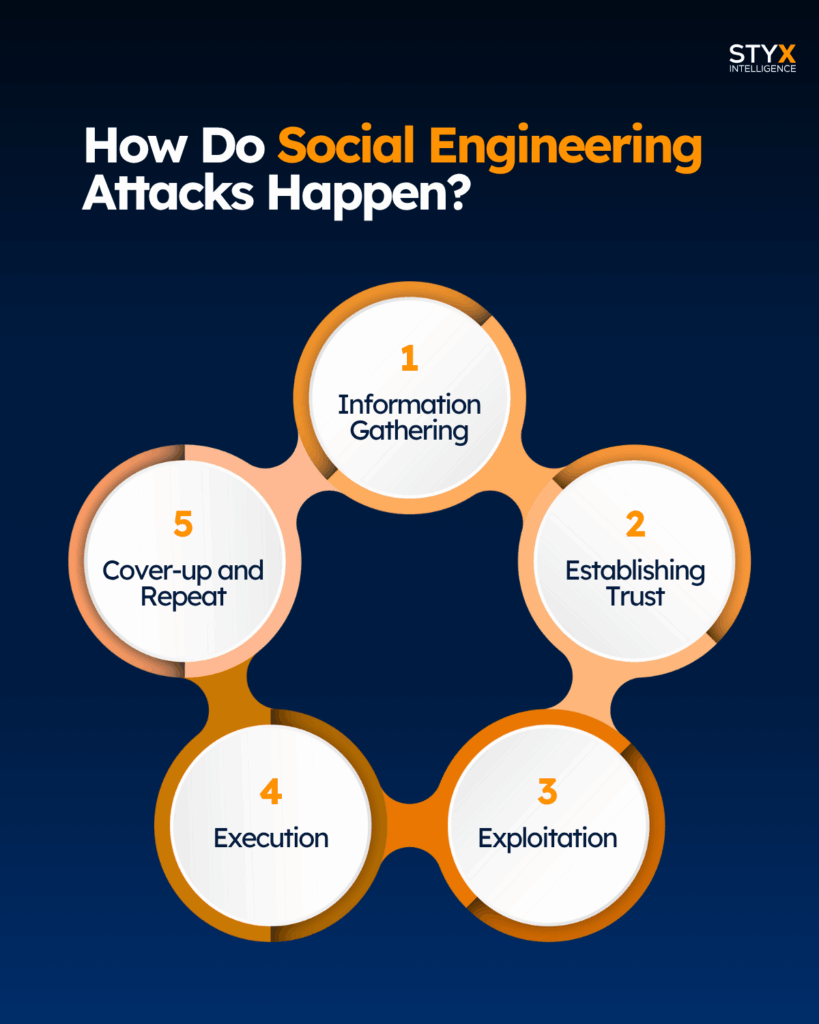
How Do Social Engineering Attacks Happen?
Social engineering attacks follow a simple, repeatable process. The tools may change, but the core steps stay the same.
1. Information Gathering
Attackers start by learning everything they can about the target. That includes employee names, job titles, emails, vendors, recent news, and any technical or organizational gaps.
Sources they use:
- LinkedIn and company bios
- Press releases and blog posts
- Social media posts from employees
- Breach data or leaked credentials
- Job descriptions that hint at software or tools
Learn more: How to Spot and Take Down Fake LinkedIn Accounts.
2. Establishing Trust
With context in hand, attackers build a believable setup. That could mean spoofing an executive, pretending to be a vendor, or posing as IT support. The goal is to make the message or request feel normal. Learn about executive protection here.
Examples:
- “Hi, I’m following up on your invoice request.”
- “This is IT, we’ve noticed login issues on your account.”
- “Can you help me verify a payment going out today?”
3. Exploitation
The attacker uses urgency, authority, or fear to push the victim to act. This could be clicking a link, sharing credentials, downloading a file, or transferring funds.
Typical actions:
- Entering passwords into a fake login page
- Sending a wire transfer to a fake vendor
- Approving a login prompt that isn’t real
4. Execution
Once the attacker gets what they need, the real damage begins. They might steal data, access systems, send more attacks from the compromised account, or sell what they’ve stolen.
Some attackers walk away. Others dig in and repeat the cycle using new pretexts, new targets, and deeper access.
5. Cover-up and Repeat
The attacker deletes traces or changes the method. Sometimes they use the stolen info to target others in the same company.
Most common entry points:
- Public company bios and org charts
- Social media accounts (especially LinkedIn)
- Spoofed vendor or executive messages
- HR, helpdesk, or finance inboxes
- Fake websites, login portals, or doc requests
- App stores, forums, and public links
- Deepfake audio or video used in real-time impersonation
Learn more: The Future of Digital Risk Protection (DRP)
Common Social Engineering Tactics
These are the most used social engineering tactics, from common phishing emails to advanced, targeted impersonations. Learn more about social media impersonations here.
They work because it’s much easier to trick people than technology… unfortunately.
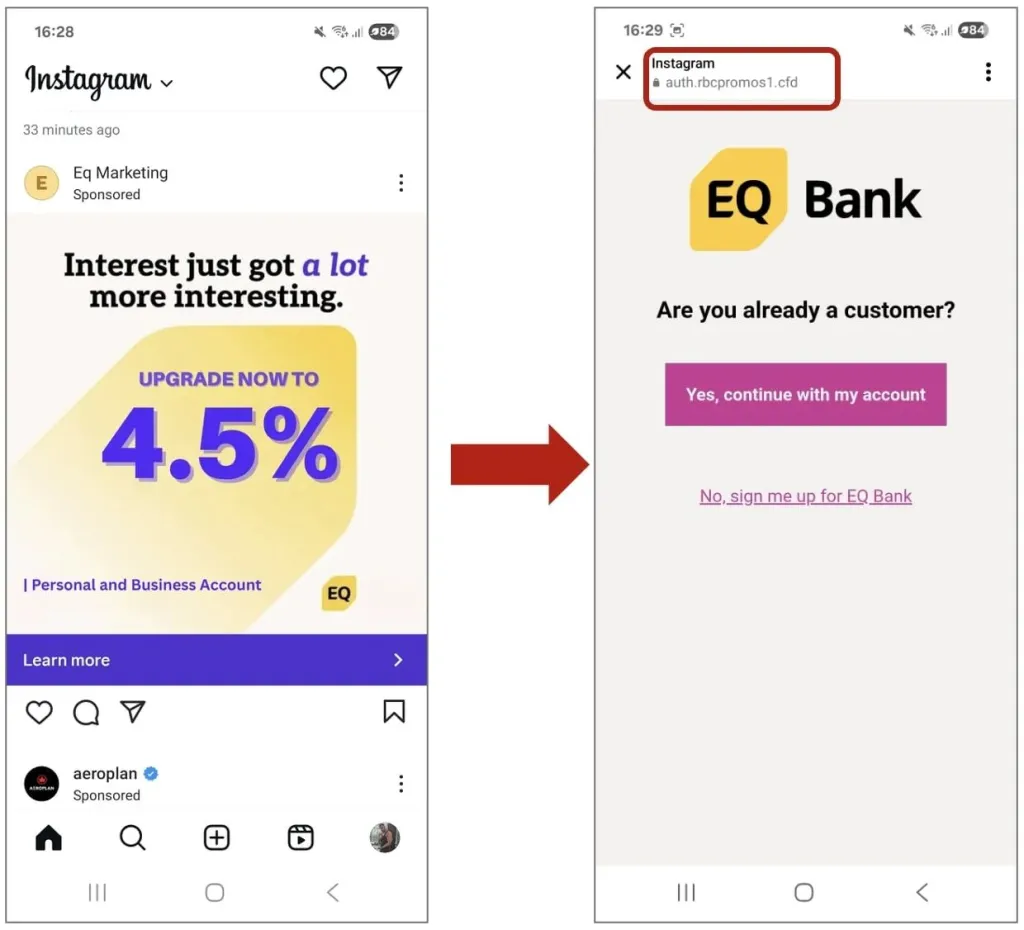
1. Phishing
The most widespread tactic. A fake email or message urges the recipient to click a link, download a file, or enter login details. It’s made to look real, using your brand, a vendor’s logo, or a service the victim uses. The goal is to steal credentials, spread malware, or collect sensitive data. Here you have some examples of phishing attacks.
Learn more: How lookalike domains damage businesses.
2. Spear Phishing
A more targeted version of phishing. Instead of a mass message, it’s aimed at one person or role (like a CFO or IT admin). It often uses personal info from LinkedIn or public bios to make the message feel real, like using the person’s name, job title, or a known business event.
3. Smishing
Phishing over SMS. These short texts claim urgent action is needed, like confirming a delivery, clicking to reset a password, or reviewing a bank charge. The links often lead to fake login pages that capture credentials.
4. Vishing
Phishing by voice call. Attackers call the target pretending to be IT support, a bank, or even the CEO. They may ask for login info, MFA codes, or request a wire transfer. Deepfake audio is making these attacks even harder to detect.
5. Pretexting
The attacker creates a fake identity and story to get someone to hand over information or access. They may pretend to be a vendor, partner, or internal employee. The key is creating a scenario that feels routine, a contract renewal, a system upgrade, or an onboarding step.
Learn more: What is Doxing and Why it’s Growing?
6. Baiting
This plays on curiosity or greed. The attacker offers something tempting, like a free tool, prize, or download. It could be a fake USB drive left in a parking lot or a link to “free” software. Once clicked or plugged in, malware installs quietly in the background.
7. Scareware
Fake pop-ups or alerts tell the user their device is infected or at risk. To fix it, they’re prompted to download software, which is actually malware. These show up on shady websites, fake tech support pages, or via pop-up ads.
8. Quid Pro Quo
An attacker offers help or something of value in exchange for access. They might pose as IT support, offering to “fix” a problem, and in return, the target hands over login details. Sometimes, it’s framed as a survey, a free gift, or account credit.
9. Tailgating
A physical attack. The attacker waits near a secured office or building and follows an employee through a door or gate without swiping a badge. Once inside, they might access hardware, plug in devices, or observe processes.
10. Watering Hole Attacks
The attacker identifies a site that their target visits often, like a vendor portal, news site, or association page, and infects it with malware. When the victim visits the site, they unknowingly download malware or are redirected to a fake version.
11. Honey Trap
The attacker builds a fake relationship with the victim, often through social media or dating platforms, to create emotional trust. They then exploit that trust to get money, data, or access to systems.
12. Business Email Compromise (BEC)
One of the most expensive attacks. The attacker either spoofs or hacks into a business email account and uses it to request payments, redirect invoices, or ask for sensitive data. Often targets finance or HR teams. These emails appear genuine and are timed to maximize believability.
13. Spoofing
This is when attackers fake an email address, phone number, domain, or identity to appear trusted. It’s used to launch other attacks (phishing, BEC, etc.). Spoofed emails might look like they’re from your CEO. Spoofed domains might be one character off from the real one.
Social Engineering Real-World Scenarios & Examples
These are real-life examples of how social engineering tactics are employed within companies and homes.
1. Phishing Campaign Leading to Malware
An employee receives an email from what looks like their cloud provider. The subject line urges them to “Review Urgent Billing Notice.” The link takes them to a fake login page. After submitting their credentials, malware is installed in the background, giving attackers access to internal systems. Weeks pass before the breach is found. Learn how brand monitoring can help.
2. CEO Fraud via BEC
A finance manager gets an email that appears to come from their CEO, asking for an urgent wire transfer to a new vendor. The attacker had studied the company’s org chart and mimicked the CEO’s writing style. The money is sent before the team realizes the email was fake. The loss is unrecoverable. Learn about executive protection here.
3. Fake MFA Notifications (MFA Fatigue)
An attacker floods an employee’s phone with multi-factor authentication prompts late at night. After dozens of pings, the employee taps “Approve” out of frustration. That one tap lets the attacker into the company’s internal network.
4. Grandparent Scam Over Voice
A scammer calls an elderly person pretending to be their grandchild in trouble. Using AI voice cloning, the caller says they’ve been arrested and need bail money. The victim wires thousands before realizing it was a scam.
5. USB Bait in Public
In a corporate office parking lot, attackers leave branded USB drives labelled “Layoff List Q3.” Curious employees plug them into company laptops. The drives auto-run malware, opening backdoors for attackers to access the corporate network.

How to Defend Against Social Engineering Tactics
Social engineering tactics target people, not just systems. So protection starts with habits, but scales with the right tools.
1. Human Habits
Strong habits are the first line of defence. Most attacks don’t need malware… they just need someone to click, trust, or share.
- Don’t open emails or links from people you don’t know.
- Avoid clicking suspicious URLs. Type them manually when possible.
- Be wary of offers that feel too good to be true.
- Don’t download random files, apps, or programs from unverified sources.
- Never share passwords, access codes, or sensitive info, even with someone who “seems helpful.”
- Be cautious of people who only interact through chat or email.
2. Security Controls
Smart technical controls reduce the damage when someone slips up.
- Use multifactor authentication (MFA) across all important accounts.
- Store strong, unique passwords in a password manager.
- Limit access to sensitive systems using the principle of least privilege.
- Run up-to-date antivirus and endpoint protection.
- Use a VPN on public or untrusted networks.
- Keep all systems and software patched and updated.
- Segment guest networks from internal systems.
3. Training & Awareness
Most people don’t know how social engineering works — until it hits them. Training helps your team spot risks early.
- Run regular security awareness training.
- Use phishing simulations to test and improve behaviour.
- Create a culture where slow, skeptical responses are encouraged.
- Teach employees how to verify identities and escalate concerns.
4. AI-Powered Technology
Modern social engineering attacks don’t always come through email. Attackers create fake domains, spoof executives, post fake ads, and even use deepfakes to trick people. AI tools give you visibility and speed that human teams alone can’t match.
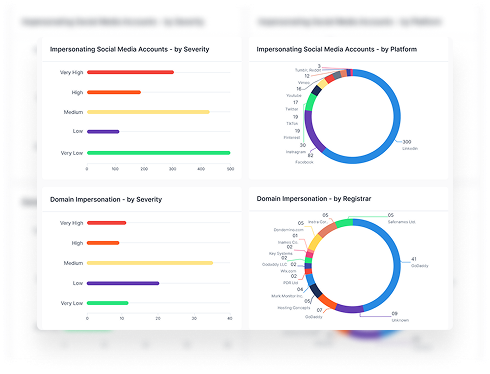
- Digital Footprint Monitoring: See how your brand, domains, and leaders appear online. Spot fake accounts, cloned sites, or suspicious use of your identity across the web.
- Dark Web Monitoring: Know if your employee logins, passwords, or customer data have leaked or are being sold on dark web forums. These exposures are often the starting point of bigger attacks.
- Impersonation Detection: Catch fake pages, spoofed email domains, or social media accounts pretending to be your brand or executives… before customers fall for them.
- Takedown Automation: Submit reports and get fake assets taken down, all within the platform.
- Real Risk Scoring: Risk scores help you focus on the most urgent problems first, the ones most likely to impact your customers or brand.

With the right tools, like Styx Intelligence, you can see threats sooner, act faster, and keep small issues from turning into full-blown crises. It’s about staying proactive, not reactive.
Identify Social Engineering Attacks Early and Protect Your Brand
Get full visibility into your digital footprint across your brand, leaders, domains, and platforms, so you can spot threats early and take down impersonation attempts before they spread.