Executive protection has moved online. From social engineering to deepfake scams, public leaders face targeted attacks daily.
This article walks through what executive protection means now, the threats to watch for, and how to reduce real risk.
Let’s get started!
What is Executive Protection?
Executive protection is the practice of securing high-profile individuals — CEOs, board members, founders, and other public leaders — from targeted threats that can put them, their families, or their companies at risk.
It used to mean physical security: bodyguards, secure cars, safe travel.
That covered one part. But now, threats have moved online — and they’ve multiplied.
Today’s executive protection focuses on digital risks. Things like:
- Leaked personal data
- Impersonation and fake profiles
- Social engineering
- Account takeovers
- Mentions or threats on the dark web
It’s not just about protecting the person. It’s also about protecting their digital footprint, their reputation, and the company they lead.
This is the baseline. Without it, everything else is exposed.
Why Are Executives the Perfect Target for Cybercriminals?
Executives have everything attackers want: trust, access, and exposure. Their digital footprint is massive — and easy to exploit.
They show up everywhere: company sites, earnings calls, media features, and podcasts. It’s all free intel. Attackers can gather enough details in minutes to impersonate them with confidence.
And because they sit at the top, they’re trusted by default. A message from a CEO — real or fake — carries weight. People act fast to avoid friction or delays.
Let’s break it down:
- They have a big footprint: Photos, bios, and contact details are public. So are their speaking events, LinkedIn posts, and even travel plans.
- They carry authority: That power can be hijacked. Attackers impersonate them to push payments, gain access, or make demands that override standard processes.
- They handle sensitive data: Deals, legal docs, financial plans, investor relations — executive accounts are often a goldmine.
- They use personal devices: Phones, home networks, email addresses — these are easier to breach than hardened company systems.
- They’re public-facing: More than security or ops teams, execs are known and seen, making it easier to build a believable impersonation.
- They move fast: Their pace means less time to double-check requests, spot fakes, or catch red flags.
- Their families are exposed too: Spouses and kids often have even fewer protections, making them soft targets for attackers looking for a way in.
They go after executives because the reward is high — and the resistance is usually low.
Why Executive Protection Is Essential Today
The risks facing executives today go far beyond a fake email or a leaked phone number. What used to be rare has become routine. And what used to stay online can now lead to real-world harm.
Here’s what’s changed:
- Personal data is easier to find and abuse.
- Impersonation tools like deepfakes make fake messages harder to spot.
- Threats spread faster. Social media, group chats, and forums all act as megaphones.
- Attacks are more targeted. Hackers do research. They know who your executives are, who they work with, and how to get close.
The consequences hit hard:
- One impersonation can lead to wire fraud or unauthorized access.
- A single leak can expose legal, financial, or HR conversations.
- Reputational damage can spread across media, investor circles, and customer trust.
- The financial cost of incident response, legal fees, and lost business can be massive.
And it’s not just about one person. Attacking an executive is often the first step to reaching the business behind them.
Learn more: Executive Protection Hygiene: The Playbook.

Common Threats Faced by Executives
Most attacks start with one thing: visibility.
Executives are easy to find, research, and impersonate.
Here are the most common threats they face:
- Executive impersonation: Fake profiles, lookalike domains, or cloned email accounts used to trick employees or partners. These are often the start of phishing, wire fraud, or data theft. Read more: Executive Impersonation Explained
- Exposure of personal data: Home addresses, phone numbers, emails, family names, and other private details often surface on people search sites, forums, or breach dumps.
- CEO fraud: An attacker poses as a senior executive to pressure employees into wiring money or giving up access.
- Account takeovers: Weak or reused passwords make it easy to hijack personal or work accounts tied to executives.
- Reputation attacks: False claims, fake news, or manipulated content (like deepfakes) aimed at damaging an executive’s image.
- Misinformation and disinformation: Targeted campaigns that exploit social media to spread false narratives or create public backlash.
- Doxing: Personal or family information published online to intimidate or harass. Here is everything you need to know about doxing (or doxxing).
Learn more: 13 Social Engineering Tactics You Need to Know
Each one of these threats opens the door to bigger problems: fraud, data loss, legal trouble, and real harm to the company’s name. That’s why executive protection is vital for today’s business.
Common Red Flags and Warning Signs
Executive protection isn’t just about reacting to attacks. It’s about identifying the signals early, before damage spreads.
1. Fake executive profiles start appearing
Cloned LinkedIn or Twitter accounts using the same name, photo, and title. These are often used to build trust and launch phishing or fraud campaigns. Read more: Executive Impersonation Explained
2. Lookalike domains go live
Domains with the executive’s name or slight misspellings are created to impersonate the exec. They’re often tied to email scams or malicious websites.
3. Unexpected password reset requests
Executives receive texts or emails asking to reset passwords they never requested. It could mean someone’s testing access or prepping for an account takeover.
4. A spike in phishing emails to the team
Emails reference the executive by name or spoof their address. This often means attackers are trying to exploit their authority to trick employees into risky actions.
5. Mentions on the dark web or criminal forums
Their names, credentials, or personal data are spotted in cybercriminal chatter. This is a clear sign they’ve been targeted—or soon will be. Read more: What is Dark Web Monitoring?
6. Family or assistants start getting hit
Attackers target less protected individuals close to the exec. If their inner circle is getting phishing or scam attempts, the exec is likely the real target.
7. Sensitive personal info gets exposed
Home addresses, SSNs, or travel details appear in breach alerts or on data broker sites. This kind of exposure opens the door to identity theft, doxxing, and impersonation.
These aren’t just random events. They’re signs to take action — early detection gives you the chance to stay in control and stop threats before they grow.
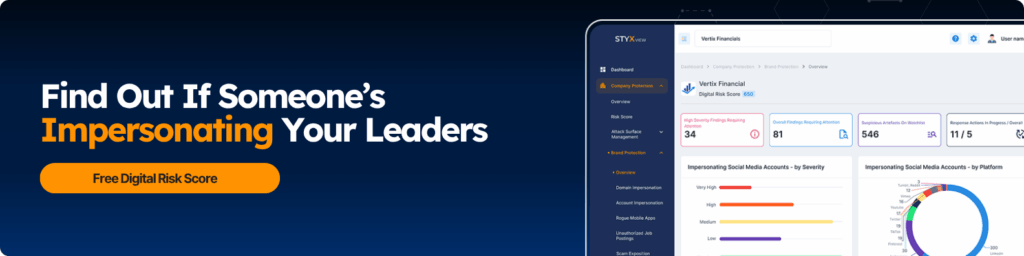
What Does Executive Impersonation Actually Cost?
Spotting a fake profile or spoofed email might not seem like a big deal — until it snowballs.
Executive impersonation hits fast, spreads wide, and, unfortunately, leaves real damage behind.
The cost isn’t just one phishing email or a mistaken wire transfer. It’s disruption, confusion, and a long road to recover trust.
Here’s how it affects you and your business:
- Loss of customer trust: If customers receive fake emails, see a deepfake video, or interact with a fake support account, they start to question whether your company is legitimate — or secure. That trust is hard to rebuild.
- Confused or panicked customers: When they’re unsure whether communication is real, customer service gets overwhelmed, and brand perception takes a hit.
- Direct revenue loss: Impersonators often reroute payments, steal customer credentials, or execute fraud. That’s real money lost.
- Drop in share value: Publicly traded companies can see immediate dips if the impersonation becomes a PR crisis or leads to media coverage.
- Legal and regulatory exposure: If customer data or investor communications are involved, legal consequences can follow.
- Internal resource drain: Your teams — security, legal, comms — drop everything to handle the fallout, which delays other projects and adds to costs.
- Investor and partner doubt: When execs are impersonated, stakeholders start asking tough questions. Trust drops, and so does confidence in your leadership.
- Media and social blowback: A convincing fake profile or a deepfake clip can go viral before your team even catches it. And once it’s out there, the reputational damage sticks.
It’s not a hypothetical risk. It’s already happening — and the price tag keeps growing.
Learn more: The Future of Digital Risk Protection
How Executive Protection Tools Address These Threats
Modern executive protection tools go beyond basic alerts — they watch everywhere, connect the dots fast, and help teams take action before threats escalate.
They do this by:
1. Identifying impersonators early
Track fake profiles and spoofed accounts across social media, email, messaging apps, and look-alike domains. Spot copied bios, photos, and usernames the moment they pop up.
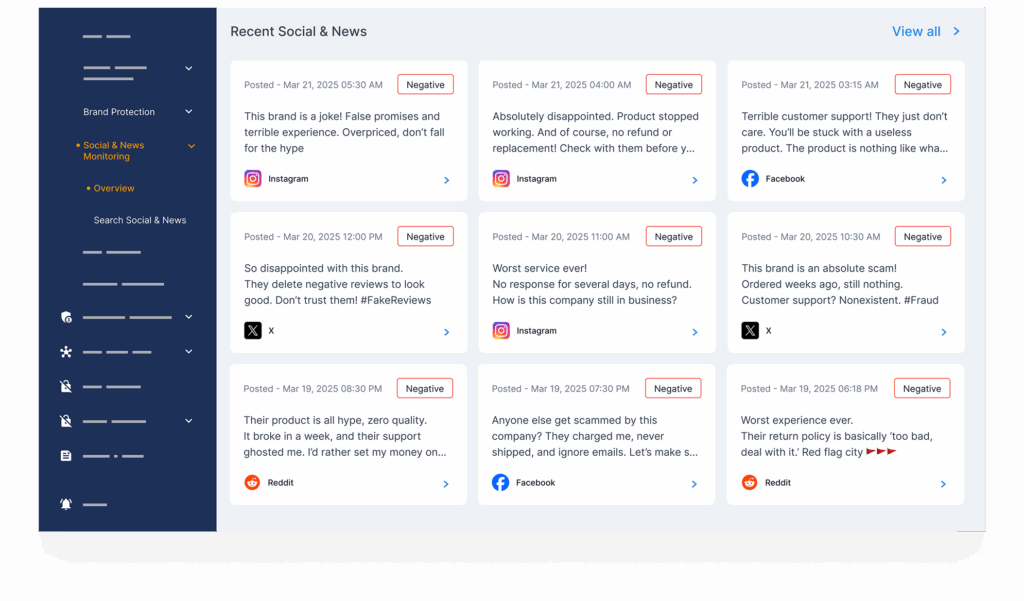
Learn more: How to Spot and Take Down Fake LinkedIn Accounts.
2. Spotting personal data exposure
Scan surface, deep, and dark web for exposed executive data — emails, addresses, IDs, credentials, financial info. Alert you as soon as personal details leak or nods of doxxing appear.
3. Monitoring executive mentions everywhere
Watch news sites, social media, and forums. Flag sudden spikes in mentions, negative sentiment, or suspicious account activity tied to execs.

4. Hunting dark web chatter
Monitor criminal forums and marketplaces for mentions of your execs — whether that’s stolen info, credentials for sale, or planning attacks on them or the organization.
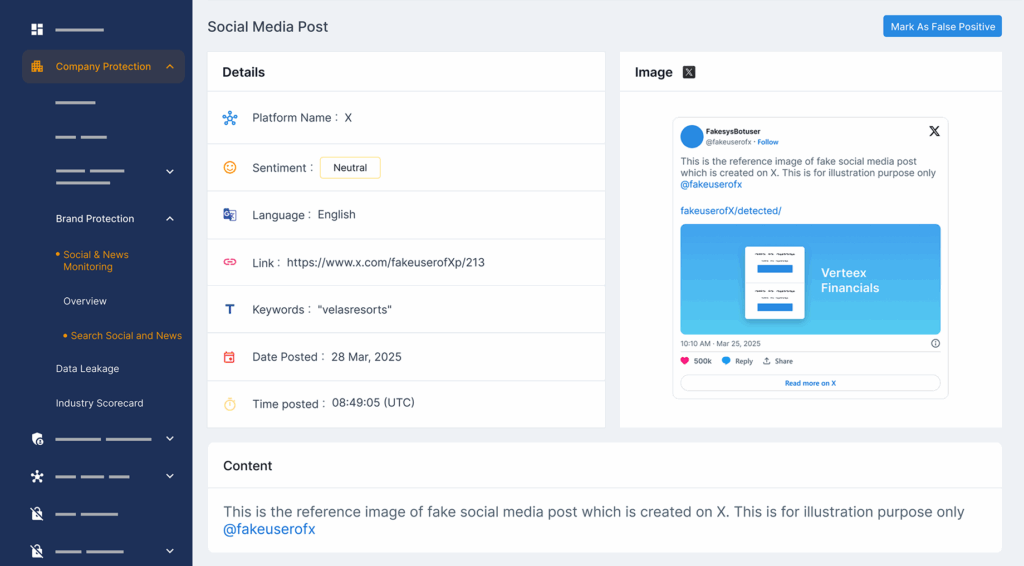
5. Sending real-time alerts with context
Alerts come with severity levels, exact timestamps, sources, and raw evidence. That means security teams know what happened, when, and where — immediately.
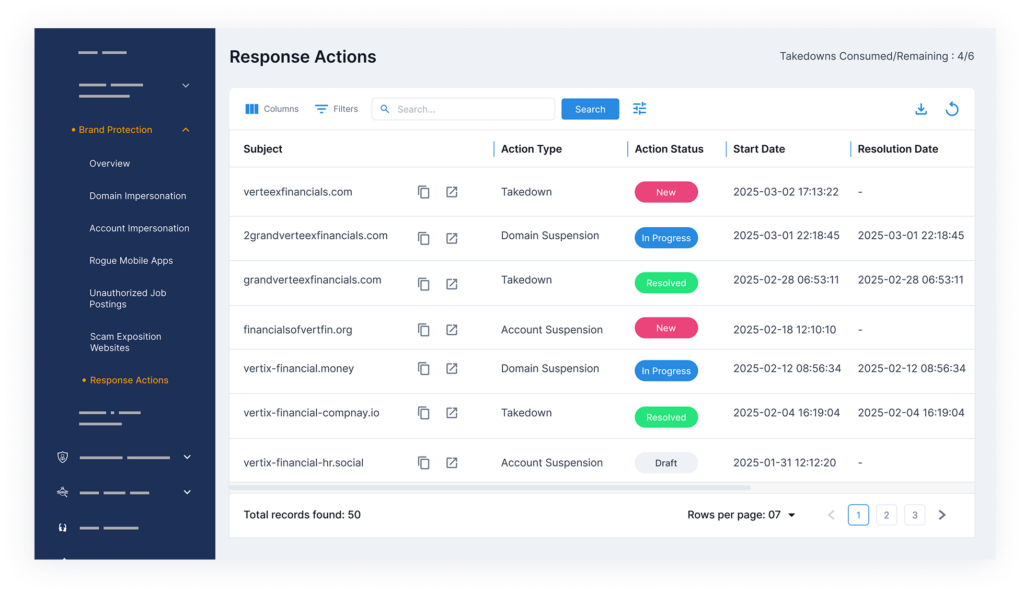
6. Automating takedown requests
From fake social profiles to leaked files, takedowns are triggered right from the platform. Requests are tracked, ensuring threats are removed fast.
7. Prioritizing threats and tracking progress
Alerts are ranked by risk level. You can monitor takedown status, see trends in exposure over time, and spot high-risk patterns for each person.
These tools go beyond reporting threats — they build a secure, actionable workflow. You get fast detection, smart prioritization with a digital risk score, and clear paths to closing the risk.
Real-World Use Cases
Here’s how executive protection plays out in real life:
1. A fake CEO profile appears on LinkedIn
Attackers clone an executive’s profile and begin messaging employees, vendors, and customers. The platform detects the impersonation within hours, triggers a takedown request, and sends an alert to the security team. The profile is removed before it causes real damage.
2. Executive credentials are spotted in a breach
A company president’s email and password show up on a criminal marketplace. The system picks it up via dark web monitoring, flags the exposure, and suggests immediate steps — like resetting credentials and investigating further access.
3. Sensitive data tied to an executive leaks
Personal documents and ID details of a CFO are posted on a deep web forum. An alert goes out immediately. Legal, comms, and security teams are looped in. The data is scrubbed from indexed sources, and the executive receives privacy recommendations.
4. Negative sentiment spike tied to a public appearance
The CMO speaks at a public event, and hours later, online mentions spike — some real, some manipulated. Monitoring tools identify trends, flag unusual activity, and help communications teams address and de-escalate issues quickly.
5. Threats made in a forum targeting an executive’s family
A message on a dark web forum links an executive’s name to a threat involving a family member. This triggers high-priority escalation, with security reviewing home protections, law enforcement getting notified, and platform takedowns initiated.
Each of these cases shows one thing: Executive protection spots attacks, but, more importantly, stops chaos before it starts.
How to Reduce Risk and Protect Your Leadership Team
Protecting executives isn’t a one-time fix — it’s a continuous process that blends smart tools with smart habits. Here’s how to get started:
- Educate your executives (and their families): Digital hygiene matters. From phishing awareness to privacy settings, regular training reduces human error and boosts resilience.
- Monitor executive exposure across the web: Use tools that scan social media, the news, forums, and the dark web for mentions, impersonations, and leaks tied to leadership. Check out our platform here.
- Automate impersonation detection and takedowns: Set up alerts for fake accounts, spoofed emails, and unusual activity. Move fast with built-in takedown requests and resolution tracking.
- Limit public availability of personal info: Scrub unnecessary PII — addresses, phone numbers, emails — from public sites and data broker platforms. The less info out there, the less attackers can use.
- Build executive protection into your broader security plan: Align executive security with your incident response playbook, threat intelligence, and brand protection strategy. It shouldn’t run in isolation.
- Run regular audits: Assess what’s been exposed, what protections are working, and where gaps remain. Prioritize high-profile and high-risk execs.
Protecting your leadership team is protecting your brand. The cost of inaction is reputational damage as well as operational, financial, and legal.
The right executive protection program helps you catch threats early, respond fast, and maintain trust with customers, partners, and investors.
Want to see how it works?
Book a demo to see how Styx monitors, detects, and takes down threats targeting your leadership — before they impact your team, your brand, or your bottom line.
















