Threat intelligence sharpens your team’s vision — letting you detect attacks earlier, respond smarter, and align security with business priorities.
In this article, we walk through real-world use cases, explain what makes good intel, and outline how to pick a tool that actually helps.
Let’s get started!
What Is Threat Intelligence?
Threat intelligence is how security teams stop guessing and start making informed decisions.
At its core, threat intelligence is about gathering information on real-world threats — malware, phishing, impersonation, ransomware, and more — and turning it into something useful. Not just data, but insight: who’s attacking, what they’re using, why it matters, and what to do next.
Good threat intelligence gives security teams context.
Instead of just seeing an alert, you understand what it means, how dangerous it is, and whether it’s tied to something bigger.
That’s what separates useful intelligence from a noisy feed of indicators of compromise.
When done right, threat intelligence helps teams:
- Detect attacks earlier
- Understand scammers behaviour
- Prioritize the right risks
- Coordinate faster responses
- Communicate better with leadership
It’s not just about knowing what threats exist. It’s about knowing which ones apply to your business — and what to do about them.
Why Threat Intelligence Matters
Threat intelligence helps you understand what’s out there — and what could come for you.
It gives context to attacks: who’s behind them, what they want, and how they operate. With that, you can move faster, focus your defences, and make better decisions.
It also helps teams stop wasting time.
Instead of chasing every alert or blocking every IP, they can focus on threats that actually matter. That means less noise, fewer false alarms, and more impact.
And for leaders, it’s not just a technical tool. It’s a business enabler.
When you know what’s coming, you plan better, invest smarter, and build resilience before something breaks.

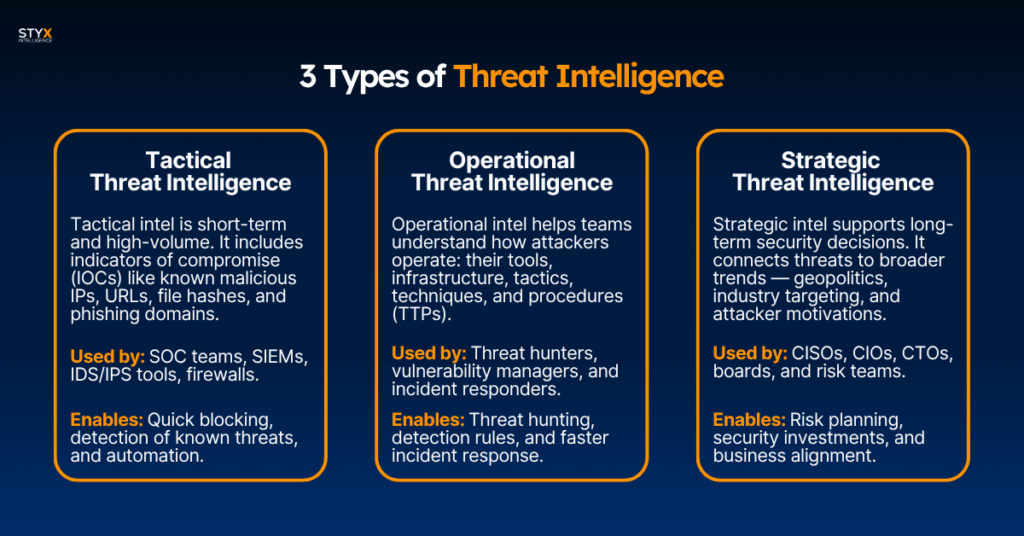
The 3 Types of Threat Intelligence
Threat intelligence isn’t one thing — it works at different levels depending on the problem you’re trying to solve.
Here’s how they break down:
Tactical Threat Intelligence
Tactical intel is short-term and high-volume. It includes indicators of compromise (IOCs) like known malicious IPs, URLs, file hashes, and phishing domains. This data feeds into firewalls, endpoint tools, and SIEMs to help block or detect known threats automatically.
It’s essential for fast threat detection and immediate response. But it’s not about context — it’s about recognition.
Used by: SOC teams, SIEMs, IDS/IPS tools, firewalls.
Enables: Quick blocking, detection of known threats, and automation.
Operational Threat Intelligence
Operational intel goes one layer deeper. It helps teams understand how attackers operate: their tools, infrastructure, tactics, techniques, and procedures (TTPs). It answers questions like:
- Who’s behind the threat?
- What are they after?
- How are they moving?
This intelligence is used to build more resilient defences, hunt for threats, and respond effectively to incidents.
Used by: Threat hunters, vulnerability managers, and incident responders.
Enables: Threat hunting, detection rules, and faster incident response.
Strategic Threat Intelligence
Strategic intel supports long-term security decisions. It connects threats to broader trends — geopolitics, industry targeting, and attacker motivations. It helps executives and leadership teams decide where to invest, what risks matter most, and how to align security with business.
Used by: CISOs, CIOs, CTOs, boards, and risk teams.
Enables: Risk planning, security investments, and business alignment.
Each layer supports a different role. Together, they help organizations understand what’s happening now, how it’s happening, and what could happen next.
The Benefits of Threat Intelligence
Threat intelligence gives you visibility into risks you can’t see from inside the network. It helps you detect, prioritize, and act on threats faster — and more confidently. But more than that, it aligns your entire organization around real, data-backed risks.
Here’s what it unlocks:
- Stronger prevention and detection: Identify threats before they hit — and recognize them when they do. With timely IOCs and TTPs, security systems and teams can detect attacks earlier and more accurately.
- Faster, smarter response: Context-rich intel gives incident response teams what they need: who’s attacking, how, and why. That means fewer delays, better containment, and quicker remediation.
- Proactive defence: You’re not just reacting to alerts — you’re hunting, patching, and building defences based on real attacker behaviour. That shifts security from a reactive to a proactive approach.
- Better use of resources: Threat intel helps prioritize what matters. Which vulnerabilities are actually being exploited? Which risks are relevant to your business? That cuts noise and saves time.
- Improved decision-making: For leadership, threat intelligence brings clarity. It connects risks to business impact, helping guide investments, roadmap decisions, and risk strategy.
- Reputation and brand protection: Spot impersonation, fraud, leaks, or narrative attacks before they spread. Intel gives you early warning — so you can act before customers or the media do. Learn more about what brand protection is here.
- Legal and compliance readiness: Many regulations require evidence of threat monitoring and response. Threat intelligence supports compliance by demonstrating due diligence and providing documented action.
- Stronger communication between teams: Threat intelligence bridges the gap between technical teams and leadership. Security can speak the language of risk — not just alerts — making conversations clearer and more actionable.
In short: Threat intelligence gives you information others don’t have, and the ability to act before threats become real problems (and big headaches).

Who Needs Threat Intelligence (and What For)?
Threat intelligence isn’t just for massive security teams or government agencies.
Today, it’s essential for any organization that wants to stay ahead of targeted threats, fraud, or digital abuse — especially if you’re a visible brand or operate in a high-risk industry.
Here’s how different roles and teams benefit from it:
- Security teams: SOC analysts, threat hunters, and incident responders rely on threat intelligence to detect and validate threats, enrich alerts with context, and respond faster. It helps them move from reactive alert-chasing to targeted defence and proactive threat hunting.
- Intelligence analysts: They go deeper into threat actor behaviour — tracking who’s targeting your org, what tools they use, and where your biggest risks are. Intel helps them build profiles, map campaigns, and create meaningful defence strategies.
- Executives and board members: CISOs, CIOs, and CTOs use strategic threat intelligence to guide long-term decisions — from budget planning to security roadmaps. It gives them visibility into business risks and emerging threat trends that could impact growth or reputation.
- Risk and compliance teams: Threat intel supports risk assessments, compliance reporting, and third-party evaluations. It provides evidence of monitoring and mitigation efforts and helps prioritize remediation based on real-world threat activity. Check this out to learn everything you need to know about Third-Party Risk Management.
- Digital trust, fraud, and brand teams: These teams use intel to find impersonation, scams, leaks, or abuse across digital platforms. Whether it’s detecting fake profiles, malicious domains, or leaked credentials, threat intelligence adds clarity and speed to takedowns and remediation.
- Small and mid-sized businesses: Even with smaller teams, threat intel helps focus limited resources where they matter most — understanding what threats are relevant, and which ones aren’t worth the time.
If you have a digital presence, a recognizable brand, or sensitive data — you need threat intelligence. It’s how you stay informed, stay protected, and stay in control.
Common Use Cases That Actually Matter
Threat intelligence is much more than collecting feeds just to say you have them. It’s about solving real problems across teams.
These are some of the most valuable, high-impact use cases we see today:
- Open, deep, and dark web monitoring: Track mentions of your brand, domains, credentials, or executive names across forums, paste sites, marketplaces, and criminal chatter. Find out when you’re being targeted — or already exposed. Here, we explain what dark web monitoring is.
- Executive and brand impersonation: Detect fake social profiles, spoofed domains, or phishing pages that target your team, customers, or partners. These attacks damage trust and can open doors to fraud or account compromise. Learn more about executive impersonation here.
- Threat indicator enrichment and investigation: Instead of chasing random IOCs, threat intel gives you context — where they came from, who’s using them, and what they’re tied to. That’s how you validate risk and focus your time.
- Campaign tracking: Connect threats across time, assets, and actors. Find out if one alert is just noise — or part of something bigger, like an ongoing phishing or ransomware campaign aimed at your industry.
- Incident response support: During an attack, threat intelligence helps answer fast: who’s behind it, what they want, how they got in, and what they’ll likely do next. That context cuts response time and limits damage.
- Vulnerability prioritization: Not every CVE matters equally. Threat intel tells you which ones attackers are actually exploiting in the wild, so you patch the right risks first — not just the ones that make headlines.
- Brand abuse and scam detection: Spot fake websites, rogue apps, lookalike domains, or fraudulent ads using your brand or product name to deceive users. Threat intelligence helps take them down before they spread.
These are just a few of the ways threat intelligence shifts your security from reactive to informed. You stop guessing. You start knowing. And that changes everything.
How Threat Intelligence Actually Works (The Lifecycle)
Threat intelligence follows a loop. One step feeds the next. Each pass helps you get clearer, faster, and more relevant.
1. Define requirements:
Start by asking the right questions. What threats are we tracking? What gaps are we trying to close? You define the goals with stakeholders, from CISOs to legal, to guide what data to look for and how to use it.
Learn more: The Future of the CISO Role: Brand Trust and External Threats
2. Collect from multiple sources (feeds, logs, dark web, etc.)
Pull data from where it matters: internal logs, threat feeds, social media, underground forums, paste sites, and the dark web. The more angles you cover, the more complete your view of the threat landscape.
3. Process raw data:
Raw data is noisy. You clean it, filter out false positives, convert formats, and align it under a standard model — so it’s ready for real analysis.
4. Analyze and contextualize
This is where intel comes to life. You dig into patterns, connect dots, and understand what a threat actually means for your business. You identify who’s behind it, what they’re after, and how they operate.
5. Disseminate with action in mind
Share findings with the people who need to act. That could mean writing a report for execs, pushing alerts into a SIEM, or briefing your SOC on new IOCs. Format and timing matter.
6. Feedback loop to evolve over time
After the action, you gather feedback. Did the intel answer the right questions? Was it used? What changed? That input improves the next cycle.
This loop helps you get sharper with every threat you face. It’s not just about more data — it’s about making that data work for you.
What to Look for in a Threat Intelligence Platform
Not all threat intelligence platforms are built the same. Some overwhelm you with noise. Others leave you blind to what matters.
A good platform should give you real insight, not just raw feeds — and make it easy to act fast when it counts.
Here’s what to look for:
- Full-spectrum intelligence: You need more than IOCs. The platform should support tactical, operational, and strategic threat intelligence, so you can stop immediate threats, understand attacker behaviour, and align long-term risk strategies.
- Real-time alerts and automated enrichment: Time matters. The right tool sends instant alerts — and enriches them with context, evidence, screenshots, and threat metadata so your team doesn’t have to dig for it.
- Threat scoring and prioritization: Not every alert is equal. Look for digital risk scoring based on severity, exposure, and business impact to help you focus on what’s urgent. Here is how a digital risk score actually works.
- Connected data across sources: The platform should connect the dots between surface web, deep and dark web, social media, forums, and internal telemetry — so you see full patterns, not isolated events.
- Built-in workflows and takedowns: The best tools don’t stop at detection. They let you act — trigger takedowns, open tickets, assign ownership, and follow resolution all within the same platform.
- Accessible for multiple teams: Security is a team effort. Your platform should be intuitive enough for security, legal, and communications teams to use without training.
- Ongoing tuning and support: Threats change fast. You need a platform that adapts, with hands-on support to keep detection accurate and aligned to your risks.
- Access to experts: When high-risk threats emerge, built-in support from experienced intel analysts helps validate what you’re seeing and plan next steps.
These aren’t bonus features — they’re the foundation. If a threat intelligence platform doesn’t help you detect, understand, and act on threats faster, it’s just more noise.

Book a demo and see how Styx Intelligence transforms raw alerts into context-driven intelligence — so your team can detect, prioritize, and act fast.