A takedown is one of the fastest, most effective ways to protect your brand online.
If someone launches a fake website, impersonates your CEO, or posts a scam job listing using your name, a takedown gets it removed — keeping your digital presence clean and trustworthy.
In this article, we’ll break down what takedowns really are, how they work, when you need them, and what they help you protect.
Let’s get started.
Want the full picture of how takedowns fit into your broader security strategy? Start with our guide on Digital Risk Protection.
What is a Takedown?
A takedown is the process of identifying and removing online content that misuses your brand (or your name) — whether it’s malicious, misleading, or just not supposed to be there.
This could be:
- A fake website that looks like yours
- A social media account pretending to be your company or exec
- A rogue app using your brand name
- A phishing domain targeting your customers or employees
- A fake job ad collecting candidate data
- Counterfeit product listings on marketplaces
- Leaked sensitive data published online
- A misinformation campaign against your organization or executives
The goal?
Shut down the threat quickly, limit the damage, and restore control over your brand and digital presence.
Takedowns aren’t about chasing criminals. They’re about staying in control of how your brand shows up online — and protecting the people who interact with it.
When Do You Need a Takedown? Common Brand Threats
Takedowns are usually triggered when someone’s messing with your brand in a way that could harm your customers, reputation, or business.
Here are the most common threats we see out there:
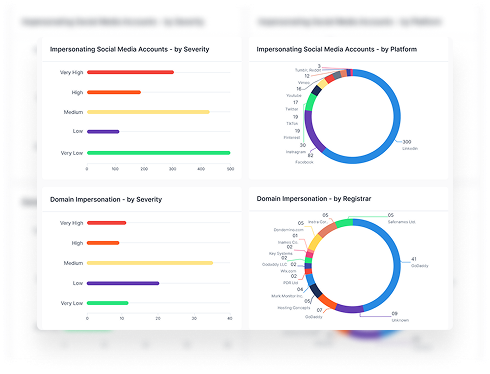
- Fake Websites & Lookalike Domains: Domains that swap letters, add hyphens, or mimic your brand to trick users. Often used in phishing, scams, or malware.
- Social Media Impersonations: Accounts that pretend to be your company or your executives — used to spread misinformation, mislead customers, or scam followers. Social media monitoring is key here to understand your brand’s perception online.
- Phishing Pages & Credential Harvesting: Pages that look legit but are designed to steal login credentials, financial info, or sensitive data.
- Rogue Mobile Apps: Apps that look like yours but are built to harvest data, push malware, or confuse your customers.
- Fake Job Ads: Listings using your brand name to attract applicants and steal personal info.
- Trademark Infringement: Unauthorized use of your logo, brand name, or other assets that mislead users or dilute your brand’s identity.
- Marketplace Counterfeits: Product listings on platforms like Amazon or Alibaba that misuse your brand to sell fake or unauthorized goods.
- Misinformation & Brand Abuse: False narratives or misleading content tied to your brand that spreads across forums, blogs, and news — destroying trust.
- Spoofed Emails & Executive Fraud: Messages that look like they’re coming from inside your organization but are designed to defraud or manipulate recipients.
- Doxing incidents that expose home addresses, phone numbers, or any other sensitive information.
Each of these attacks can be damaging on its own. Combined? They can seriously chip away at customer trust, security, and your brand’s reputation, which is exactly why quick, effective takedown capabilities matter.
We also covered brand impersonation takedowns here, including which ones are easiest to act on.

Where Do These Brand Threats Usually Show Up?
These threats don’t live on the dark web only — they show up right where your customers and partners are.
Here’s where brand abuse tends to pop up the most:
- Search Engines: Fake sites impersonating your brand can show up in search results and ads — catching users before they even hit your official site.
- Social Media Platforms: Impersonation accounts, fake giveaways, misinformation, and customer scams — all playing out on X, LinkedIn, Facebook, Instagram, and TikTok.
- Job Boards and Hiring Sites: Fake job listings that attract candidates using your company name, then phishing for sensitive data like passports, addresses, or financial info.
- Domain Registrars and Hosting Providers: Lookalike domains and spoofed subdomains pop up constantly — often with malicious content attached.
- App Stores and Third-Party Marketplaces: Rogue apps claiming to be yours (or “sponsored” by you), aiming to scam users or collect personal data.
- News, Forums, and Blogs: Misinformation or coordinated campaigns to spread false narratives, damage reputation, or manipulate sentiment.
- Dark Web Forums: Leaked credentials, internal documents, and discussions about exploiting your brand show up in underground spaces all the time.
The hard part?
These attacks don’t come with red flashing lights. They often blend in with your original content, visuals, and communication style.
The Takedown Process (No Legal Team Required)
Most people hear “takedown” and think lawsuits, lawyers, and long waits.
Not anymore.
Modern takedown workflows are fast, streamlined, and often handled without needing legal teams involved — especially when you have the right platform or partner doing the heavy lifting.
Here’s how it typically works:
1. Detect the Threat
A phishing site, fake profile, or rogue app pops up.
Detection can come from:
- Monitoring tools
- User and phishing detection reports
- Threat intelligence feeds
- Brand impersonation alerts
2. Verify the Violation
Not every suspicious item requires or qualifies for a takedown.
So the next step is to check the following:
- Is it impersonating your brand or exec?
- Is it violating your trademark or intellectual property?
- Does it violate laws, brand policies, or terms of service?
- Is it hosting malicious content or phishing?

3. Build the Case
Once verified, you gather the evidence. This usually includes:
- Screenshots of the violation
- URLs and timestamps
- Proof of brand ownership or trademark registration (when needed)
4. Submit the Takedown Request
This is sent to the right party — domain registrars, hosting providers, app stores, or platforms like Meta, LinkedIn, or X. Each has its own process, but most support standardized takedown forms.
If necessary, escalate unresolved cases to organizations like ICANN or local authorities.
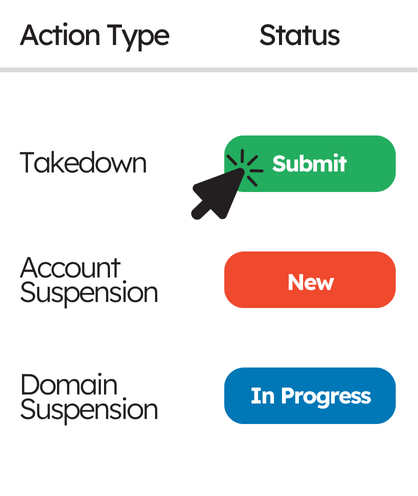
5. Track, Follow Up, Repeat
Once submitted, you monitor for:
- Confirmation of removal
- Delays or rejections
- Resurfaced threats
NOTE: Post-takedown, ensure continued compliance by monitoring domain activity for recurring threats.
If it’s part of a platform like Styx, the entire lifecycle is tracked in one place — with workflows that make follow-ups easy.
What Can You Protect With Takedowns?
Takedowns are much more than removing a fake website or a rogue profile. They’re about protecting the people, systems, and outcomes that make your organization run.
Check out this article to learn everything about what brand protection is.
Here’s what’s really on the line — and what smart takedown workflows help you protect:
- Your customers: Takedowns help stop phishing pages, scam job ads, and malicious apps designed to steal customer data, money, or trust.
- Your team: Impersonation of executives or employees can lead to payroll fraud, internal confusion, or leaked credentials. Taking these down keeps your team safe and focused.
- Your sensitive data: Sensitive business files, exposed credentials, leaked source code — once they’re out, they’re public. Takedowns can help reduce the damage and limit access before things spiral. Learn more about data leakage and how to keep your sensitive information safe.
- Your reputation and trust: Trust is fragile. A single impersonation on LinkedIn or a fake domain spreading malware can damage how customers, partners, and even the media perceive your brand.
- Your growth: Misinformation and brand abuse cause confusion, but also kill deals. When fake listings or misinformation make their way into the market, it impacts investor confidence, pipeline health, and customer acquisition.
- Your revenue: Malicious lookalikes steal traffic, trick customers into fake purchases, and redirect sales away from you. The longer they’re up online, the more money you stand to lose.
- Your time and focus: A good takedown process is automated and streamlined. You’re not chasing down hosting providers or filling out forms all day — you’re solving the problem with a few clicks, not chaos.
- Your future risk exposure: The longer malicious content lives online, the more it spreads, gets indexed, and becomes harder to remove. Fast takedowns help stop that snowball before it starts.
- Your uptime and operations: Some impersonations generate lots of disruptions. Fraudulent activity tied to your brand can trigger internal fire drills and shift teams away from real work.
In short: Takedowns protect your brand’s credibility, your customers’ experience, and your ability to keep growing — without being constantly dragged down by digital noise.
Why Takedowns Matter Now More Than Ever?
Impersonation threats aren’t a “someday” problem — they’re already everywhere.
AI has made it easier (and faster) than ever to spin up fake websites, deepfake executives, clone voices, and launch scam campaigns at scale — again, all these threatening trust and reputation.
Meanwhile, your brand isn’t just on your website anymore. It’s on marketplaces, in DMs, on job boards, forums, and fake social media accounts you’ve never even heard of.
This explosion of off-channel exposure means one thing:
You’re being represented online in ways you didn’t approve — and probably don’t even know about.
Here’s what’s changed:
- Impersonation is cheap now: Bad actors can spin up dozens of fake domains, profiles, or job ads in minutes — at scale, with almost no cost.
- Scams are more convincing: Thanks to AI-generated images, bios, and polished branding, fakes don’t look fake anymore. Customers and employees fall for them — fast.
- Brand attacks move fast: This increases the need for continuous monitoring and proactive responses
- Trust is fragile: One fake listing, one impersonated email, one bad customer experience — and real trust is gone. For your buyers, your partners, even your investors.
- You don’t control where your brand lives anymore: It’s not just your website or your LinkedIn. Your brand lives on search results, marketplaces, forums, social platforms, and scammy corners of the web.
You don’t need to control the whole internet. But you do need to control how your brand shows up — wherever it shows up.
That’s the foundation of Digital Risk Protection. It’s about visibility, speed, and staying ahead of threats — not just reacting to them.
Do You Need Takedown Services?
If your brand is growing, visible, or trusted by others, protecting it may no longer be optional.
Takedown services help you stay in control of how your brand shows up online, and make sure nothing undermines the trust you’ve worked so hard to build.
You are not sure if you need this?
You should consider takedown services if you are doing any of the following:
- You’re building a strong digital presence: The more visible your brand is, the more likely it is to be misused.
- You rely on customer trust: Whether you’re selling products, offering services, or just building community — trust is everything.
- You’re hiring online: Fake job posts can trick applicants, harm your reputation, and flood your team with confusion. Takedowns help protect your employer brand.
- Your executives or team are active on social media: Leadership visibility is powerful but, unfortunately, prone to impersonations.
- You run campaigns or paid ads: Every campaign boosts your visibility — and that’s exactly what scammers exploit.
- You’ve had customers report suspicious emails or sites: That’s a signal. Takedown services help you act on it, fast.
- You want to protect sensitive data and IP: If your name is on exposed data, rogue apps, or code snippets — even indirectly — that exposure can ripple through trust, legal, and security issues.
- You care about brand reputation: Reputation is about what others see online and what they associate your business with. Takedowns remove the noise that dilutes your story.
- You’re investing in long-term growth: Growth needs consistency. Takedowns help you maintain a trusted online presence as you scale — so reputational risks don’t slow you down.
- You don’t want your team wasting time: You want to automate the heavy lifting, so you’re not chasing domains, writing legal emails, or reacting manually to threats.
What do you think?
If you checked even one of these, it’s time to think seriously about takedowns.
Curious how exposed your brand really is? Get a free Digital Risk Score — and get a clear view of what threats need action now.

If you want to connect with our team to get more info and learn about Styx’s platform, book a demo here.