Most security leaders still measure their work in alerts, incidents, and controls. That work matters, but it is no longer the main thing your company expects from you.
The next stage of the CISO role has nothing to do with firewalls or cloud policies… it has everything to do with trust.
Boards and executive teams are starting to ask new questions.
- What are you doing to protect the company’s reputation?
- How are you keeping our leaders safe online?
- How are you defending our brand when attackers impersonate us?
- How fast can you detect misinformation before it spreads?
If you have not been asked these questions yet, you will be. The shift has already started across large companies in every industry.
Security teams are no longer judged only by how they protect internal systems. They are judged by how they protect the trust the business has earned with customers, partners, investors, and the public.
The New Attack Surface: Trust
For years, security has focused on internal assets, such as servers, endpoints, cloud accounts, identity systems, etc. Those areas are important, but they are not where most “trust-damage attacks” start.
Today, your real attack surface lives outside your network.
- It lives on social media, news platforms, search results, paid ads, messaging apps, and online communities.
- It lives on fake domains, fake profiles, and deepfakes.
- It lives anywhere attackers can impersonate your brand, your products, or your people.
That is why the CISO role is expanding. Most companies can deal with a technical breach, but few are prepared to handle what happens outside their perimeter.
Things like:
- A compromised social media account spreads misinformation before you can respond.
- A fake executive profile tricks your employees or customers.
- A lookalike website steals credentials and, unfortunately, your brand gets the blame.
- A deepfake video call tricks your finance team into sending money.
- A false news story about your company causes confusion or moves your stock price.

The Most Important Question for the New CISO Role
Boards used to ask about vulnerabilities, ransomware, and incident response plans. Now they ask about brand and reputation.
They also ask a simple question that many CISOs cannot answer: How are you protecting the trust we have built with customers?
Trust is one of the most critical assets for any organization because it:
- Drives revenue
- Shapes growth
- Influences market position
That is why companies now expect security teams to protect the people and public assets that represent the brand.
How does it usually work?
- Marketing owns visibility
- Comms owns the message
- Legal owns compliance
- Security owns risk
What else are risks?
- Brand abuse
- Impersonation
- Misinformation
The board sees that, and attackers, of course, know it.
Security leaders now need visibility and control over that new attack surface.
Brand Protection Is Becoming a Cyber Function
Five years ago, most brand abuse came from lookalike domains. Attackers would register a close variant of your domain name and use it for phishing, scams, or credential theft. That problem still exists, but it is no longer the main one.
What are the main threats now?
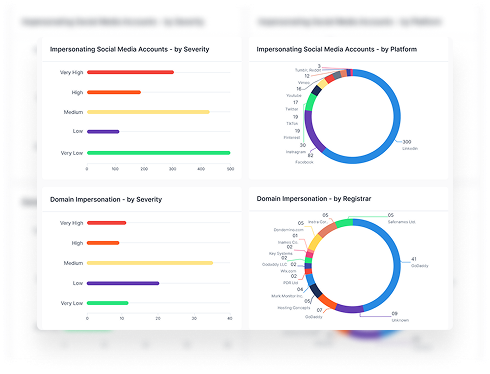
- Executive impersonation is growing faster than domain impersonation
- Fake accounts appear on LinkedIn, Instagram, and X
- False news stories spread through search engines
- Attackers set up paid ads that outrank your real website
- Scam networks run full operations built on impersonation
The Global Anti Scam Alliance reported one trillion dollars in global scam losses in the last twelve months (2024).
This is no longer a small threat. It is an entire underground economy built on stolen trust.
For most attackers, impersonation is easier and more profitable than hacking a network.
As this shift continues, brand protection will not sit in marketing. It will sit in cyber.
Executives Are Now the Easiest Way In
Most executives have a full public footprint. Their profiles, interviews, press quotes, speaking events, and travel schedules are all online.
Attackers know this and use it to build impersonations.
How?
Attackers now use deepfakes to imitate leaders during calls or voice messages. Some of these attacks have led to large wire transfers and internal approvals that looked legitimate at first glance. The victims believed they were speaking with the right person because the voice and face looked close enough to real.
That is not rare anymore…
Why?
- Voice cloning tools take minutes.
- AI-generated profiles look legitimate.
- Fake conference calls are convincing.
- Public information makes impersonation simple.
Executives also move fast, rely on assistants, and expect quick support. Those habits create “trust shortcuts” that attackers use.
This is why executive protection is no longer a personal concern but a business risk.
Disinformation and Misinformation Are Now Core Business Risks
False information spreads faster than any attack vector we have ever seen.
You’ve probably heard about the following:
- A fake announcement about tariffs moved the financial markets for a short period.
- A compromised social media account at the SEC influenced the price of Bitcoin for about twenty minutes.
- False job offers have targeted journalists and other public figures for months before anyone knew the truth.
These are much more harmful than technical incidents because they damage your reputation and customer trust.
Gartner predicts that disinformation security will become a formal discipline inside cyber over the next few years.
This prediction lines up with what companies are already experiencing.
- Marketing tools are not designed for risk
- PR teams do not track attacker behaviour
- Legal teams cannot detect issues early
Cyber teams are the only group with the skills and visibility to treat misinformation as a threat.
So, this is our prediction: Disinformation will not stay a media problem. It will become a core cyber function.
Why CISOs Must Own the Public/External Attack Surface
Your company already monitors internal systems. The gap is everything outside the network.
That is where attackers impersonate your brand, target your executives, and shape public narratives.
Security teams now need:
- Visibility into social, news, and community platforms: This is where false narratives and fake accounts begin.
- Visibility into new domain registrations and lookalikes: This is where phishing and scam sites start.
- Visibility into dark web and messaging channels: This is where leaked data, hate, or targeted risks show up.
- Takedown workflows: This is how you shut down threats.
- Cross-functional alignment with comms and legal: This is how you respond as one team.
Right now, most companies do not have this system in place… that is why attackers keep winning.
The Next Three Years Will Reshape the CISO Role
The profile of a modern CISO is shifting. The job is no longer about protecting internal assets; it is about protecting trust.
Security leaders will need to work closely with communications/marketing, compliance, and legal. More importantly, they will need clear playbooks for executive risk, brand abuse, and public disinformation. Beyond all that, they will need real-time visibility outside the firewall.
They will also need to answer new questions from the board.
- Are we monitoring for impersonation?
- Are we detecting fake profiles or fake ads?
- Are we tracking news or social posts that could harm the company?
- Are we prepared to respond when false information spreads?
- Are we protecting the executive team from targeted attacks?
These questions signal the next stage of security leadership.
How CISOs Can Prepare Now
Your team does not need to solve everything at once. You only need a clear starting point.
This is what you can do:
1) Build an inventory of public-facing assets
- Executives
- Social accounts
- Brand terms
- Domains
- Products
- Apps
This becomes the baseline for all monitoring.
2) Establish collaboration with marketing, comms. and legal
You need shared criteria for abuse, impersonation, fraud, and misinformation.
You also need clear owners for each step of the response.
3) Monitor social media, news, and domain activity in real time
You cannot respond unless you see the threat, so you need to know what’s happening out there.
Learn more: Social Media Monitoring: Protecting Your Narrative Online
4) Treat impersonation like an incident
Use evidence capture, classification, and takedown requests.
Learn more: Brand impersonation takedowns
5) Protect your executive team
Monitor for fake profiles, hate speech, or targeted threats.
Executives are the highest value targets for impersonation.
Learn more: Executive Protection: Securing Leaders in the Digital Age
6) Educate your board
Explain the link between trust and revenue.
Show why brand protection is now part of cyber risk.
This shift will take time, but if you start now, you will be ready when your board expects it from you.
A Final Thought
Companies can protect systems without much trouble. However, protecting trust is harder… because trust is public and misinformation moves quickly.
This is why the CISO role is expanding.
Not because security teams asked for it, but because the risk now lives outside the perimeter.
If you want to prepare your team for this change, you need visibility into brand abuse, impersonation, and misinformation before they reach your customers.
Book a demo to see how Styx protects your brand, your executives, and your external attack surface.