What Is LinkedIn Impersonation? (Fake LinkedIn Account)
LinkedIn impersonation refers to any unauthorized use of your brand, people, or assets on LinkedIn to appear legitimate and gain trust. Attackers either create new fake LinkedIn accounts or hijack existing ones, then use that credibility to collect data, steal money, or manipulate users/customers.
You’ll typically see it in a few forms:
- Fake member profiles: Completely fabricated identities or clones of real employees, executives, or recruiters with copied photos, titles, and bios.
- Compromised real accounts: A legitimate profile is taken over and used to message coworkers, candidates, or partners.
- Lookalike company pages: Unofficial pages that copy your logo, name, and description to attract followers and post scams.
- Job listings and recruiter outreach: Listings and DMs that harvest resumes, SSNs, banking details, or “onboarding fees.”
- Comment and DM “support”: Accounts replying under your official posts with fake help links or asking users to “verify” details.
- Executive impersonation, including deepfakes: Profiles or media that mimic leaders to request urgent payments or sensitive files.
- Link and domain spoofs: Messages that send people to lookalike login pages or payment portals to capture credentials or divert funds. If you want to monitor for spoofed websites or lookalike domains and take them down, check out our brand protection tool.
Why do scammers love LinkedIn impersonations?
Well… because it’s easy to exploit the trust already built in the platform.
A convincing LinkedIn identity gets clicks and replies faster than a cold email.
What do scammers try to get from these LinkedIn impersonations?
- Credential theft
- Business email compromise
- Payroll or vendor payment diversion
- Investor or crypto fraud
- Malware delivery
- Long-term reputational damage.
If you discover any of these signals, you’re dealing with impersonation. The rest of this guide shows you how to investigate quickly and take down fake LinkedIn account profiles, pages, and posts before they spread.
LinkedIn Fake Account Detection: Signals & Red Flags
You don’t need fancy tools to spot trouble on LinkedIn. Most impersonators leave fingerprints.
Train your team to look for these tells during normal work, then move to take down fake LinkedIn account profiles before they spread.
1. Profiles that don’t add up
- Big titles with thin or vague experience, buzzwords instead of real responsibilities.
- Brand-new profile, lots of connections, almost no comments or post history.
- “About this profile” shows a recent creation date, no verified work email, and no recent updates.
- Personal Gmail/Outlook in the contact info when the person claims to work at a large brand.
- Links in the profile that don’t point to the company’s real domain.
- Endorsements or recommendations that look copy-pasted or land on the same day.
2. Company pages and job posts that feel off
- Lookalike company names or URLs with extra characters, few followers, and no link back to your real site.
- Job posts with no hiring manager, no location, or no path to your official careers page.
- “Recruiters” who refuse to use your corporate email domain, who ask for fees, banking info, or “equipment deposits.”
Learn more: Identify and take down lookalike domains, phishing websites, fake job postings, and more.
3. Message behaviour that trips alarms
- Urgent requests for invoices, payment detail changes, W-9s, payroll files, or MFA codes.
- Push to move the chat to WhatsApp or Telegram “to speed things up.”
- Support-style replies under your posts with “verify here” links that point off-domain.
- Executive “DMs” asking for secrecy, gift cards, or crypto.
4. Network patterns worth flagging
- Multiple clones of the same executive with tiny differences in name or handle.
- Clusters of accounts that only like and comment on each other, then target your followers.
- New “employees” listing your company that no manager recognizes.
If two or more of these signals show up, treat it as impersonation. Capture the profile URL, take quick screenshots, alert security or comms, and start the process to take down that fake LinkedIn account page or profiles before customers, candidates, or partners get pulled in.
Have You Been Impersonated? A Simple Confirmation Workflow
Move quickly, collect proof, then take down fake LinkedIn accounts with clean, consistent evidence.
These are the steps you could follow:
A. Centralize signals
- Create one reporting path (e.g.,
spoof@yourcompany.comor a Slack/Teams channel). - Funnel customer screenshots, suspicious messages, recruiter flags, and odd exec DMs into this queue.
- Auto-reply with what you need: profile URL, screenshots, any messages, and how they found it.
B. Verify in minutes (search checklist)
- Exact brand/exec search: LinkedIn search → People/Companies/Jobs tabs.
- Variations: Add misspellings, spacing, and homoglyphs (o/0, l/I, rn/m, underscores, “Official,” “Support,” “HR,” “Recruiting”).
- Company claim checks: People → “Current company = YourCompany” and scan for unfamiliar faces or roles.
- Jobs sweep: Jobs → search your brand + role titles; open each listing; note poster profile and destination URL.
- Ad/comments check: Visit your real posts; scan replies and DMs for “support” links or forms.
- About this profile: Open the panel; note created/updated dates and verification signals.
- Reverse-image: Run the headshot/logo through Google Lens or TinEye.
C. Distinguish the type
- Clone/Impersonation: New or lookalike profile/page using your brand, exec, or recruiter identity. Learn more: Executive impersonation explained.
- Compromised account: Real employee/exec profile showing off-brand posts, strange DMs, or login alerts.
- Fake job post: Role, salary, or process doesn’t match your careers site; off-platform applications.
- Comment/DM “support” fraud: Replies pushing forms, refunds, “verification” links.
Playbook: Everything you need to know to protect your executives.
D. Capture evidence (make the takedown easy)
- URLs: Profile/page/post/job; use More → Copy link.
- Screenshots: Full page with address bar; include conversation threads.
- Metadata: Date/time (with timezone), reporter name, and how it was discovered.
- Side-by-side proof: Your real page/profile vs the fake (logo, handle, bio, link destination).
- Victim impact (if any): Sums lost, PII requested, malicious domains.
E. Notify the right people
- Security/IT: For compromise checks, password resets, SSO/MFA audit.
- Comms/Support/Recruiting: To prepare holding lines and route suspicious LinkedIn messages.
- Legal: If trademarks, executive likeness, or victims are involved.
F. Decide and act
- Clear impersonation or fraud: Go to the section on how to take down a fake LinkedIn account.
- Unclear/low signal: Monitor, collect more proof, and warn front-line teams what to watch for.
- Confirmed compromise: Lock the account, reset credentials/MFA, post a brief notice, and document all changes.
Keep the workflow tight: One inbox, one checklist, one evidence packet. That discipline shortens review time and increases the odds that LinkedIn removes the fake profile on the first pass.

How Fake LinkedIn Profiles Hurt Your Organization
1. Phishing and BEC payment diversion
Impersonators request updated banking details, new vendor setups, or invoice “corrections.”
The results?
Funds move to attacker accounts, finance audits stall, and, unfortunately, the recovery is very unlikely.
2. Candidate and job-seeker fraud tied to your name
Fake recruiters collect resumes, SSNs, and “equipment fees.”
The problem here is that victims blame your brand, not the scammers. Also, Glassdoor ratings will drop, and your real talent pipeline will slow.
3. Investment scams misusing your brand or executives
Spoofed advisors and deepfake exec clips invite targets into “private” groups. People transfer funds to fraudulent wallets, then file complaints that drag your brand into the mess.
Learn more: 13 Social Engineering Tactics You Need to Know
4. Employee or page account takeovers
Leaked or reused passwords let attackers hijack real profiles or your company page. They post scams, message followers, and burn the audience trust you spent years building.
5. OSINT harvested for future spear-phishing
Cloned profiles mine org charts, vendor names, travel schedules, and tech stack clues. Every detail boosts the success rate of the next targeted pretext.
6. Vendor and supply-chain spoofing
Scammers pose as MSPs, logistics partners, or SaaS reps. They push malware as “updates,” swap ACH instructions, and compromise shared projects.
Learn more: Third-Party Risk Management: Everything you Need to Know
7. Comment and DM customer-support fraud
Lookalike accounts reply under your posts and DM customers with “verification” links. Credentials and PII leak, tickets surge, and your support SLAs suffer.
8. Funnel hijacking and counterfeit ads or offers
Lookalike pages and fake “promo teams” run paid media. They steal leads, mess up remarketing audiences, and trigger ad-platform penalties against your real accounts.
9. Sentiment and reputation damage with media blowback
Public complaints, chargebacks, and negative posts pile up. Reporters and analysts notice, partners ask questions, and brand sentiment trends downward. Not good.
Learn more: Social Media and News Monitoring: Protecting Your Narrative Online
10. Legal, compliance, and incident-response costs
Outside counsel, platform evidence packs, regulator outreach, and insurance scrutiny consume budget and time. Opportunity costs hit marketing, sales, and product roadmaps.
Now, how do we solve this? Takedowns.
Take Down Fake LinkedIn Account: Step-by-Step Takedown (People, Pages, Jobs)
Use this to take down fake LinkedIn accounts and other impersonations as quickly as possible.
1. Confirm and document
Copy the profile or page URL. Save screenshots, timestamps, message threads, and any harmed user reports.
2. Report via the right path
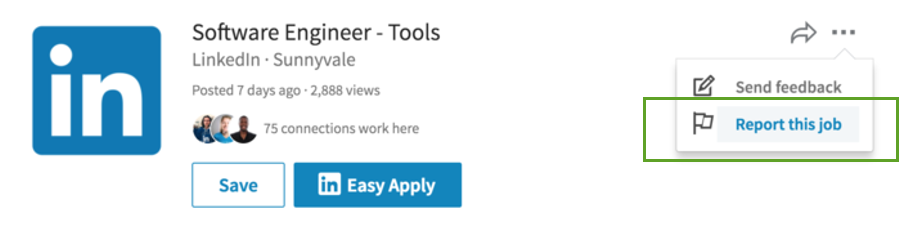
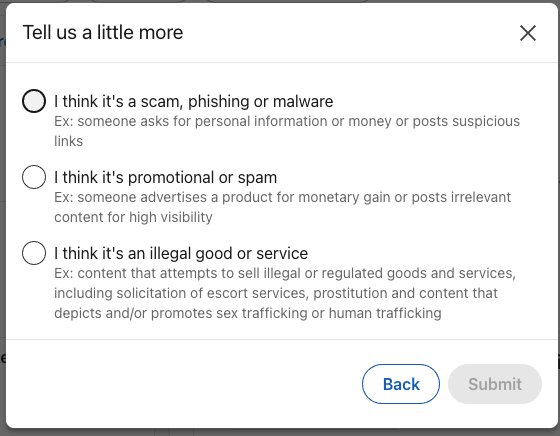
A. How to report fake LinkedIn job listings for removal:
- Open the job to the Job details page
- Click More (···) → Report this job
- Under Why are you reporting this?, select I think it’s spam or a scam
- Pick one:
- I think it’s a scam, phishing, or malware
- I think it’s promotional or spam
- Click Submit
Report abusive or fraudulent content through LinkedIn’s Help Center if needed.
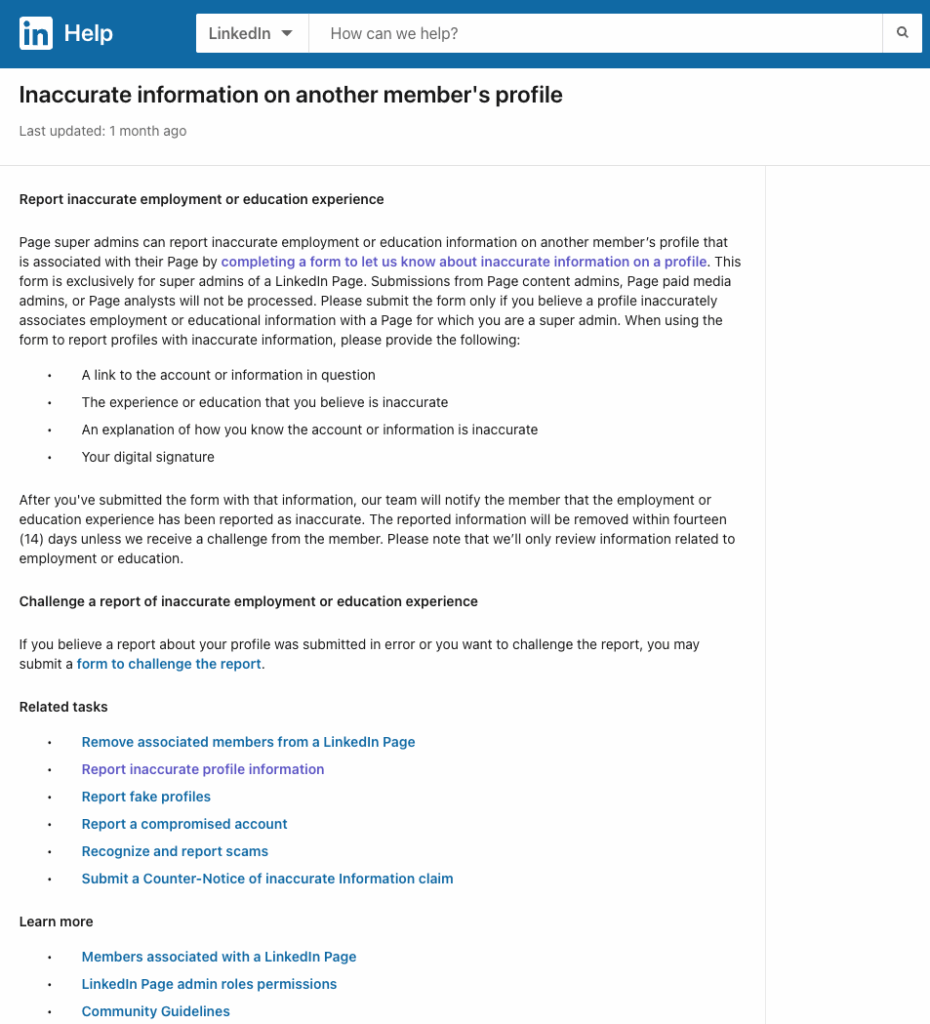
B. Reporting inaccurate information (best for fake roles on a profile)
Use LinkedIn’s “inaccurate information” complaint when a profile falsely lists your company or school. You’ll need:
- The URL of the profile or post
- The correct company/school name
- A short explanation of what’s wrong and why
- Your digital signature (type your full name)
LinkedIn routes these through the Help Center.
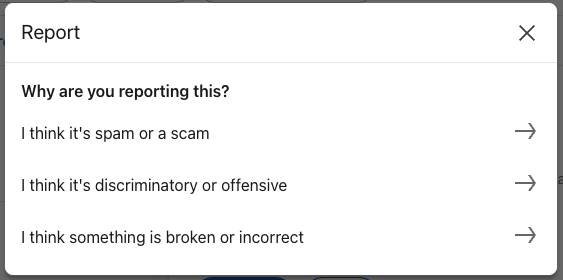
C. How to report a fake LinkedIn company page
- Open the company page in question
- Click More → Report abuse
- Choose “impersonation”, “fake account”, or “fraud or scam“
- Pick the most accurate reason and submit
This sends the report to LinkedIn’s safety team via the Help Center workflow.
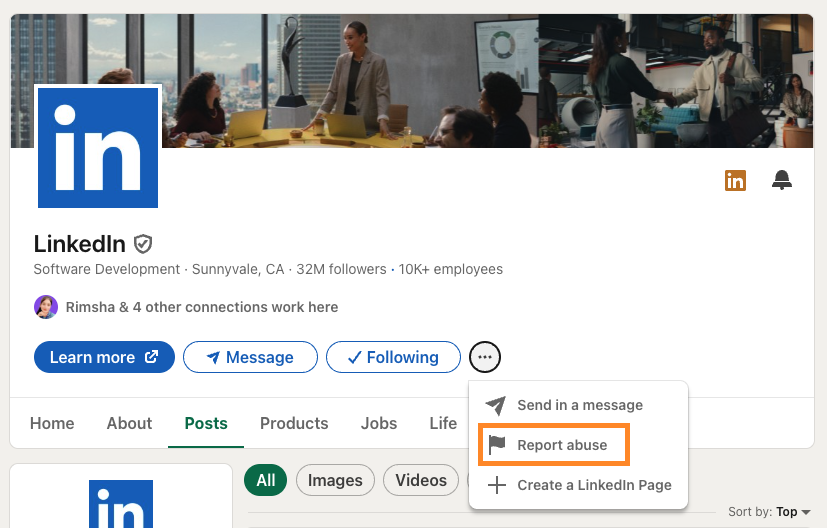
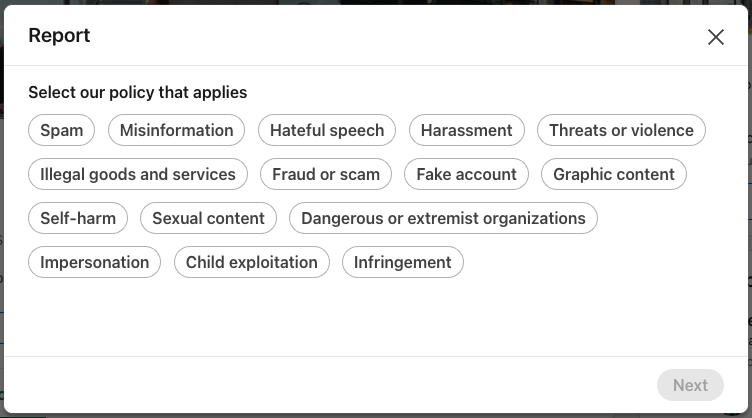
D. Reporting fake profiles
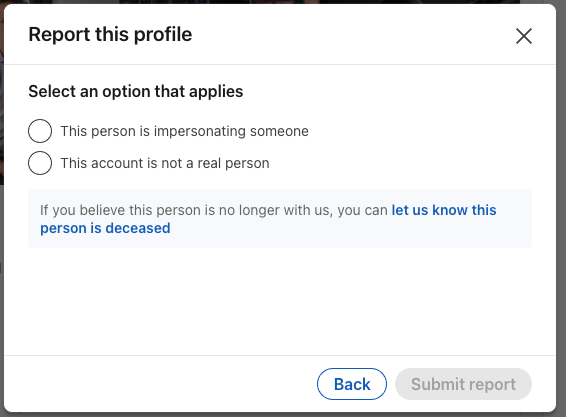
- Click the More button or the (···) icon on the member’s profile.
- Click Report / Block.
- Select Report [member’s name] or entire account on the Report or block pop-up window.
- Select This person is impersonating someone or This account is not a real person on the Report this profile pop-up window.
- Select Submit report.
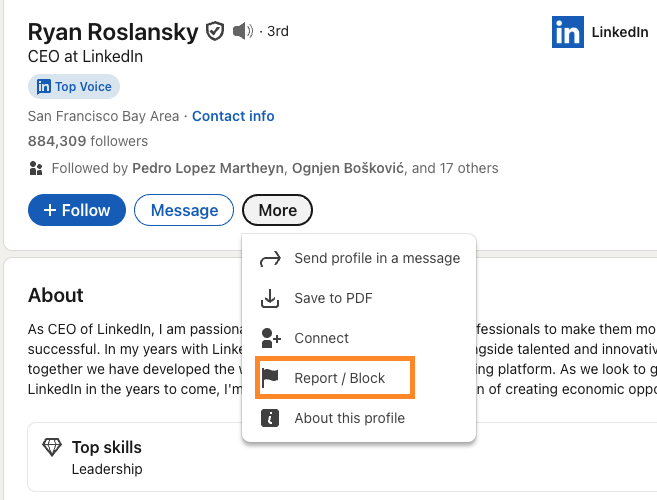
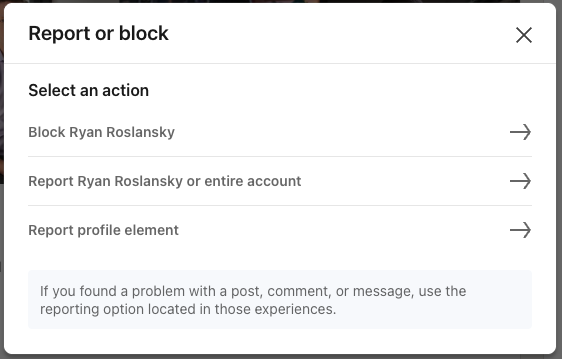
E. Reporting trademark or copyright infringement
Trademark (brand misuse, logos, names): Use LinkedIn’s IP complaint process for non-copyright issues (trademark, logo, false profile, other IP). LinkedIn provides a standard notice that covers trademark and other content violations.
Report trademark infringement here.
Copyright (images, text, video you own): Use LinkedIn’s DMCA notice. There’s also a counter-notice if your content was removed in error.
Report copyright infringement here.
F. Reporting compromised (hacked) accounts
- Open the member’s profile
- Click More → Report/block → Report profile
- Select Hacked account → Submit
For additional help, open a support ticket via the Help Center.
3. Multiply credible reports
Ask verified employees, partners, or victims to report the same URL with evidence.
How many reports are required to delete a LinkedIn account?
There is no fixed number. Clear proof and multiple independent reports speed review.
4. Protect while you wait
Post an advisory on your site and company page. Pin official recruiter names and job links. Route all suspicious LinkedIn messages to one inbox. Brief support, recruiting, legal, and security. Contact law enforcement if money or PII was taken.
5. After removal
Re-scan for clones and lookalike handles. Log the takedown, add new variants to monitoring, and close the loop with anyone affected.
Build a Proactive Program
The following steps will help you build a simple, repeatable program so your team finds and acts on fakes quickly and confidently.
1. Foundations
- Own the real estate: Create and maintain your official Company Page, short vanity URL, and verified domains. List official job links and support channels on your website and pin them on your LinkedIn page.
- Lock down access: Use SSO, MFA, and least-privilege roles for page admins. Remove access during offboarding the same day. Review admin lists monthly.
- Publish a verification hub: One public page that lists your real pages, recruiter emails, hiring domains, and how to report suspicious profiles.
2. Monitoring
- Search patterns daily: Brand and exec name variants, common misspellings, homoglyphs, and punctuation swaps. Include “support,” “HR,” “recruiter,” “careers,” “promo.”
- Watch comments and DMs: Scan replies under high-reach posts for “we can help” links and fake support scripts.
- Track jobs and people: Search “People” who list your company, new “Employees” without internal records, and job posts that use your brand.
- Extend coverage: Monitor lookalike domains, public code repos, and paid ads that reference your brand.
Learn more: What is Brand Protection? (And Why You Should Probably Care)
3. Playbooks and Roles
- Intake: One inbox and a Teams/Slack channel for suspicious activity reports from customers and staff. Triage within 1 hour.
- Evidence: URL, screenshots, timestamps, message threads, and any payment or wallet details. Store in a shared case template.
- Report: Use LinkedIn’s specific flows for fake profiles, fake pages, fake jobs, inaccurate employment, and hacked accounts. Escalate with multiple independent reports from verified employees or affected users.
- Notify: Post a short advisory on your official channels when a scam is active. Point users to your verification hub.
- Protect: Pause paid campaigns that scammers are mirroring. Add temporary keyword blocks to social scheduling.
4. Hardening
- Standardize recruiter bios and email formats so fakes are easier to spot. Publish the current recruiter list.
- Rotate executive headshots and watermark banner art. Remove old assets that scammers reuse.
- Enforce strong passwords and MFA on personal LinkedIn accounts for all admins and executives.
- Enable email authentication (SPF, DKIM, DMARC) for brand protection across channels that feed LinkedIn scams.
5. Metrics to keep in mind
- Time to detection: First sighting to triage start.
- Time to removal: First report to platform action for each URL.
- Volume and impact: Number of fakes per month, number of user reports, number of refunded victims if applicable.
Targets
- Detect high-risk fakes within four hours during business hours.
- Submit the first report within one hour of confirmation.
- Aim to take down fake LinkedIn account variants within 24–48 hours, then rescan for clones and update your watch terms.
This structure gives you clear owners, fast evidence, and consistent follow-through, so impersonators lose reach quickly and your team stays ahead.
How can you optimize and scale this?
How to Take Down Fake LinkedIn Accounts at Scale
Manual reporting works for a one-off incident. It does not work when scammers spin up new profiles every week or even every day.
An AI-powered brand and social protection platform can help you find, prioritize, and take down fake LinkedIn accounts quickly, then prevent repeats.
This is exactly what a tool can do for you:
1. Brand and social monitoring
Add your brand terms, domains, logos, and official pages. The system monitors LinkedIn and other networks for impersonations, spoof company pages, fake recruiters, and comment spam. You get clear alerts with the exact URLs and screenshots.
2. Executive impersonation monitoring
Upload approved headshots and bios for your leaders. The platform flags new profiles, ads, or videos that reuse their name or image, including basic deepfake patterns. You see what was copied, where it lives, and who it is reaching.
3. Risk scoring and evidence packs
Each hit is scored by similarity, visibility, and likely harm. The platform auto-builds an evidence pack with screenshots, timestamps, message copies, and a short summary. This is the bundle reviewers need to act on, which cuts back and forth and shortens the time to removal.
4. Takedown automation
Choose the correct LinkedIn path, fake account, impersonation, hacked account, inaccurate employment, company page, or job post. Forms prefill from the evidence pack.
You submit, track status, and share updates with Legal, Security, and Comms. Time-to-removal and repeat-offender trends are measured so you can prove progress.
5. Dark web and credential exposure
If employee credentials tied to your domain show up in breach dumps or forums, you get an alert. You can force resets and MFA before an attacker uses those logins to take over a real account.

Why does this save you time?
One queue for all incidents, less manual hunting, fewer screenshots in email threads, faster reports that match what platform reviewers expect, and a repeatable process your team can run every day.
Book a demo with our team to see how Styx detects impersonations, prepares comprehensive takedown reports, and helps you shut down fake LinkedIn accounts more efficiently.
















