What Lookalike Domains Really Are (and Why They Work)
We have an entire post on what lookalike domains are and how to deal with them, but in short, a lookalike domain, sometimes called a spoofed or impersonated domain, is a fake version of a legitimate company’s website address.
It might change a single letter, replace a character with a number, or use a different top-level domain.
These small changes work because many people don’t double-check URLs. They trust what looks familiar. That trust is exactly what attackers exploit.
Once an impersonated domain is live, it becomes a launchpad for multiple types of fraud. It can host a phishing website, send convincing emails, or copy the real site’s design to steal credentials and payments.
In many cases, attackers register entire networks of evil twin websites to make their scams harder to track and shut down.
Let’s review some common ways lookalike domains damage businesses.
1) The Financial Damage
Lookalike domains create losses that hit immediately, then ripple through every corner of a business.
When a phishing website or spoofed domain succeeds, it triggers a chain reaction that extends far beyond the first stolen dollar.
This is how.
The First Hit: Direct Financial Losses
A single impersonated domain can reroute payments, fake invoices, or capture customer funds before anyone realizes what happened.
Even smaller companies are at risk. One fake invoice or urgent payment request can push losses past 100,000 dollars.
These losses happen when your own team approves a payment they believe is real. The email looks right, the domain looks right, and the money gets transferred.
Hidden and Ongoing Costs
The first payment is rarely the end. What follows are months of hidden costs and operational disruption.
- Forensic teams investigate how the fake domain slipped through.
- Legal counsel reviews exposure and potential liabilities.
- Refund programs and customer communication campaigns are launched.
- Insurance providers reassess coverage and raise premiums.
Meanwhile, support and finance teams are overwhelmed.
Why?
Customer calls increase, and you might need to process refunds and review recent payments one by one.
Even marketing pauses planned campaigns and shifts to clear updates for customers.
As you can see, the financial impact multiplies quickly.

Insurance Doesn’t Cover It
Many organizations expect cybersecurity insurance to absorb the damage. In most cases, it doesn’t.
Traditional cyber insurance policies often exclude “voluntary transfers,” which describe exactly what happens when an employee sends money to a spoofed domain that appears legitimate.
Because the payment was made willingly, even under false pretences, insurers classify it as outside the policy’s protection.
That leaves companies to carry the full cost. Legal fees, customer reimbursements, and recovery efforts fall entirely on internal budgets.
For small and mid-sized organizations, that can be devastating.
2) The Trust and Reputation Damage
Trust is fragile. Years of careful brand building can vanish in minutes when customers discover they’ve been scammed by someone pretending to be you.
When a spoofed domain or phishing website uses your name, people associate the harm with your brand.
That loss of confidence shows up in sales, renewals, and word of mouth.
Customers blame the real brand (YOU)
When someone is scammed by an impersonated domain or evil twin website, they often believe your company failed to protect them.
They see your logo and design, and they assume the site was yours. Explanations about registrars or hosting do not change how they feel. Trust falls, and some customers stop buying.
Common reactions you should plan for include:
- Customers question emails, texts, and ads that come from your real domain because attackers have made them doubt everything.
- People post warnings on social platforms and forums, which discourages others from engaging with you.
- Prospects slow down or walk away because they want to avoid any brand that feels risky.
How lookalike domains break your communication channels
A network of spoofed domains makes your normal outreach harder. Customers who have seen a fake login page start to ignore your password resets and security alerts.
Sales messages get caught in spam filters after a wave of phishing websites start using similar language (mimicking you).
Support teams spend time proving that a message is legitimate before they can help anyone.
The public record lasts
Impersonation incidents leave a long trail online.
News articles, forum threads, and social posts tie your name to scams long after you remove the malicious domains.
Search results surface these posts when people look up your brand. That history makes reputation recovery slower and more expensive than the technical cleanup.
Partners and stakeholders feel it too
Vendors and potential partners may delay contracts when they see active domain impersonation.
Due diligence teams add questions and require extra controls.
Furthermore, investors expect a clear plan for monitoring spoofed domains and taking down phishing websites quickly. If you cannot show control, confidence drops.

What can you do to protect trust?
You can reduce trust damage by making the real paths clear and acting quickly when abuse appears.
- Publish a short page that lists your official domains, social handles, app store links, and support emails. Keep it easy to find and up to date. Learn more about attack surface management.
- Monitor new registrations that contain your brand terms so you can spot an impersonated domain before it starts a campaign.
- Use a takedown workflow that gathers evidence, submits reports to registrars and hosts, and tracks status to closure.
- Send plain language updates to customers that explain what happened, what you fixed, and how they can verify official links.
- Add a simple form for customers to report suspicious sites or messages so you hear about issues early.
- Coordinate with your legal, security, and marketing teams to ensure responses are consistent, coordinated, and useful.
For a deeper view on how to protect your brand and customer trust, check out our blog on how to identify, monitor, and take down domain impersonations.
3) The Operational Damage
The damage of lookalike domains goes beyond lost money and reputation. It’s also about how much work stops when one of these incidents hits.
A single phishing website or spoofed domain can slow an entire company, from IT and finance to marketing and customer support.
Here is how:
The cost of distraction
Once an attack is confirmed, productivity stops. IT and security teams shift into containment mode.
They have to reset passwords, scan devices, and review logs. On the other hand, finance might need to pause payments and review recent transfers to rule out further exposure. Finally, customer support needs to answer a spike in customer questions.
Also, customer support gets long queues of calls from people asking if an email or message was real.
The ripple effect inside your company
Each department feels the slowdown differently.
- IT teams pause projects to investigate alerts and reset compromised accounts.
- Finance freezes payments until they verify requests from leadership or vendors.
- Support teams answer anxious customers who want to confirm messages or refund requests.
- Marketing teams delay campaigns until they know all outgoing links are safe.
This can last days…
Sometimes it goes longer if accounts were used or systems were affected. Unfortunately, projects pause until you know the risk is gone.
The human side
The pressure to spot fake messages becomes a huge pain for teams.
Employees feel anxious, second-guess themselves, and sometimes hesitate to act at all. That stress leads to burnout and turnover, especially in teams that handle constant communication, such as finance and customer service.
Fear also creates new mistakes.
When people worry about clicking the wrong thing, they start avoiding legitimate work or overlook subtle red flags.
What can you do to keep work moving
Operational resilience starts with clarity and routine.
- Train teams to verify requests using fixed steps rather than personal judgment.
- Automate detection where possible so employees aren’t carrying the full burden of spotting threats.
- Encourage quick reporting instead of blame. When someone suspects a fake email or phishing website, the goal is to alert, not investigate alone. The faster your team reports, the faster you can contain the issue and return to normal work.
Automation, clear workflows, and shared awareness turn operational fear into control. Once employees know what to do and who handles it, they can focus on their jobs again instead of watching every message with suspicion.
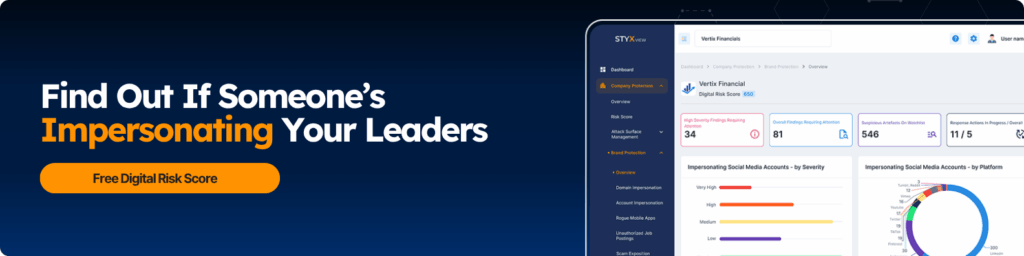
4) Targeted Damage (Executive Impersonations)
When executives get impersonated, the problem gets even worse.
Things like fake emails, phone calls, or websites that look official can trick employees, partners, or even customers into sending money or sharing sensitive information.
How do they do it?
Attackers use a leader’s authority to make people act before thinking.
Why executive impersonations work so well
Well, it’s simple… people trust leadership.
When a request looks and sounds real, they feel pressure or the need to act.
Attackers know that trust and urgency make a powerful mix. They combine those with lookalike domains that mimic company names and layouts.
AI makes it even worse.
Now that deepfake technology is cheap and easier to use, attackers are moving beyond email. They can clone voices or videos that sound like real executives.
Learn more: Executive protection hygiene: The playbook.
The impact inside the organization
As you know, executive impersonation leads to financial loss, but more importantly, it shakes internal trust.
- Employees start questioning every message from leadership.
- Important decisions take longer because everyone needs extra confirmation.
- It also damages the reputation of those leaders who were impersonated.
When an attacker uses an executive’s name to steal money, partners and customers begin to doubt official communication.
That loss of credibility spreads quickly across email, calls, and social media.
Learn more: How to deal with Social Media Impersonations?
What can you do to protect your executives?
The best protection starts with clear verification habits.
- Create a second, independent way to confirm financial requests, especially urgent ones.
- Teach teams to check full email addresses, not just display names.
- Use strong domain monitoring to detect new registrations that imitate your brand.
- Take down impersonated domains before they’re used in scams.
- Keep executives informed about how their names, emails, and likenesses could be abused.
5) Legal and Regulatory Damage
Lookalike domains can create legal exposure that lasts long after the phishing websites are gone.
A single impersonated domain or evil twin website can trigger breach notifications, trademark issues, and consumer complaints.
That turns these types of incidents into a very long process.
What triggers legal risk
These are the most common issues you should expect.
- A lookalike domain tricks customers and exposes personal data.
- Fake ads or cloned pages misuse your trademarks and brand assets.
- Phishing websites collect payments or credentials under your name.
- Victims file complaints with regulators, platforms, and consumer bodies.
- Partners raise due diligence flags and ask for proof of control.
Each one adds work for legal, security, and communications.
Why this gets hard and costly
You are dealing with multiple rules at once. Registrars, hosts, ad networks, and social platforms all have their own policies. Each one needs specific evidence and a clear request. Some of them are simple to resolve, but others take time.
You also have to document everything.
That means screenshots, headers, domain records, timestamps, and copies of your notices. If you skip this step, follow-up is slower, and repeat offenders are harder to stop.
Trademark and brand misuse
When attackers use your company name, logo, or product images on fake websites or ads, customers start to confuse the impersonated domain with your official one. That confusion hurts trust and can damage your trademark rights if you don’t respond.
Courts and online platforms expect you to protect your brand.
If you ignore repeated impersonations, it becomes harder to prove later that you own and actively defend your marks.
Privacy and breach rules still apply
If customers share data on a fake site that looks like yours, you may still need to notify them. The rules depend on where you operate and where users live. GDPR and similar laws focus on impact to the person, not just where the data leaked.
Two actions that can help you.
- Tell people what happened and how to protect themselves.
- Show that you found the phishing websites, removed the spoofed domains, and tightened checks.
Clear updates reduce risk and rebuild trust.
For reference, GDPR allows fines up to 20 million euros or 4 percent of global annual revenue, whichever is higher. That is why quick detection, clear notices, and proof of action matter.
What you can do now
Set the basics before the next incident, so you are not writing under pressure.
- Keep a public page that lists official domains, social handles, and app links.
- Capture evidence the same way every time. Include URLs, WHOIS, DNS, and screenshots.
- Use takedowns for registrars, hosts, ad networks, and social platforms.
- File trademark and impersonation notices with side-by-side comparisons.
- Prepare plain-language customer notices with verified links and simple steps.
- Track every case from report to removal, including who did what and when.
- Review with legal and privacy leads after each incident and update the playbook.

6) Technical Sophistication Fear: Why Old Defences Fail
Lookalike domains and phishing websites have dramatically evolved.
What changed is how advanced, simple, and realistic they’ve become. The tools that once helped you block spam or filter malicious links can’t keep up anymore.
Attackers now use automation, AI, and public infrastructure to create fake websites that look perfect and pass security checks. That’s why companies still fall for them even when they have modern defences in place.
Why traditional controls don’t work anymore
Most phishing websites today look legitimate. They use HTTPS, so you see the padlock in the browser. They use real branding, professional design, and often publish SPF, DKIM, and DMARC records. All the signs that people associate with “safe” are there.
Security systems can’t always tell the difference. Detection tools rely on signatures or domain reputation, but attackers rotate domains too quickly for those systems to adapt.
Recent data shows that more than one million phishing sites are created every month. That’s a 700 percent increase since 2020. Each one can go live, steal data, and disappear before traditional scanners flag it.
How AI changes the game
Artificial intelligence has made phishing faster and harder to detect. Attackers use AI to clone websites, create fake text and images, and send personalized messages that look natural.
Phishing attacks have increased by more than 1,200 percent since generative AI tools became public. More than 70 percent of them now use AI to bypass filters or imitate brands.
AI also helps attackers create entire “phishing kits” in minutes. These include fake landing pages, cloned logins, and automated email campaigns that target users at scale.
The human gap
Even the best tools can’t fix the human side of this problem.
Most phishing links are designed to look normal, especially on a phone. The font is small, the URL is short, and the screen hides key details. People are distracted, so they click without checking.
The imbalance between cost and damage
Here’s the hardest truth: it costs attackers almost nothing to launch a lookalike domain, but it costs you thousands to find and take it down.
Registering a domain is cheap, often less than twenty dollars. Creating a fake site takes minutes. But detection, validation, and takedown take hours of coordination with registrars, hosts, and legal teams.
That imbalance keeps defenders behind.
For every domain you remove, new ones appear under different extensions or with minor spelling changes.
What helps close the gap
To keep up, you need visibility beyond your network.
- Start by mapping all official domains and brand assets.
- Monitor public channels, ad networks, app stores, and domain registrations.
- Mitigate ASAP when you find impersonations. Collect evidence, send takedown requests to multiple platforms at once, and track every case until it’s closed.
Remember:
Speed and automation matter. The quicker you detect and shut down a phishing website, the less time attackers have to cause damage.
That’s exactly what Styx Intelligence helps you do.
It helps you:
- Detect lookalike domains and impersonated websites before customers find them.
- Monitor public channels, forums, and social platforms for brand misuse.
- Take down phishing websites, with proof and full tracking.
- Protect your executives, your customers, and your reputation.
- Provides you with actionable insights, prioritized by business impact.
















