Cyber threats are getting harder to spot. Lookalike domains sit at the center of modern phishing attacks, costing businesses over $100 billion globally in 2024.
These attacks don’t look suspicious anymore. They use proper security certificates, clean design, and domains that fool even careful readers.
Here’s what you need to know to protect your business.
What are Lookalike Domains
Lookalike domains are registered web addresses that imitate a real brand with small, deliberate changes. Attackers swap letters, add extra ones, change the ending from .com to .co, or pair your domain name with words like login, secure, or support. These tweaks pass a quick glance, which is why people click.
You may also hear them called cousin domains, spoofed domains, copycat domains, doppelgänger domains, or simply fake domains. The goal is the same. Make a web address look close enough to the real one so people trust it.
Lookalike domains often support phishing attacks. Criminals send emails or set up pages that appear to be from your company and try to collect passwords, card numbers, or other sensitive information. We will cover how these scams work in the next section.
6 Lookalike Domain Tactics
Modern attackers use more than simple typos. Here are eight tactics, with what to watch for and why they work.
1) Typosquatting
Attackers generate many slight misspellings, not just one or two.
- Missing characters: “netfilx.com” instead of “netflix.com”
- Extra characters: “googgle.com” instead of “google.com”
- Character transposition: “twiitter.com” instead of “twitter.com”
- Adjacent key errors: “maicrosoft.com” (exploiting keyboard layout proximity)
2) Homoglyph swaps with look-alike characters
Letters from other alphabets can look identical to Latin ones.
- Cyrillic substitution: “microsоft.com” (using Cyrillic ‘о’ instead of Latin ‘o’)
- Greek letter replacement: “αpple.com” (using Greek alpha instead of ‘a’)
- Number-letter confusion: “micr0soft.com” (zero for ‘o’), “goog1e.com” (‘1’ for ‘l’)
- Visual similarity: “rn” combined to mimic ‘m’ in “rnicrosoft.com”
Why it works: Most fonts make these pairs hard to spot, especially on phones.
3) Combo-squatting with trusted words
They add believable words so the domain feels official.
- Finance sector: “microsoft-banking.com”, “secure-paypal-login.com”
- Technology: “apple-support-center.com”, “googledrive-storage.com”
- E-commerce: “amazon-store-official.com”, “ebay-marketplace.com”
Why it works: The extra word matches the task in the message, so people click.
4) TLD and location tricks
They keep the brand name and change the ending or region.
- Country-code exploitation: “microsoft.co.uk”, “paypal.ca”
- New gTLD abuse: “apple.store”, “amazon.shop”
- Multiple TLD registration: Securing variations across .com, .net, .org simultaneously
Why it works: Endings are easy to miss on mobile and in long URLs.
5) Subdomain spoofing that looks “corporate”
They place trusted words at the front to mimic internal systems.
- “secure.login-microsoft.com” (legitimate-looking subdomain structure)
- “support.apple-id-verification.com”
- “mail.corporate-outlook-365.com”
Why it works: Many users only read the left side and assume it is real.
6) Dot-omission tricks
They drop a period so the address looks familiar at a glance.
- “wwwmicrosoft.com” (missing dot after “www”)
- “microsoftcom.au” (missing dot before “com.au”)
- “securelogin.bankcom.com” (missing dot before “com,” then padded with another .com)
Why it works: The eye skims past missing dots, especially on small screens.

Using Lookalike Domains for Phishing Websites
Phishing is when someone pretends to be a trusted organization to get you to share something valuable, such as logins, one-time codes, card details, or bank info.
Lookalike domains make that impersonation believable because the web address looks close enough to the real one that people don’t notice the difference.
How phishing and lookalike domains work together
1. Register a lookalike domain
Attackers buy a domain that’s close to yours, using any of the methods you saw in the previous section.
2. Copy the look and flow
They set up pages that mirror your design and normal sign-in steps. At a glance, it feels familiar.
3. Send people to the fake site
Links arrive by email, text, social messages, paid ads, QR codes, or search results. The domain looks right enough that many people click.
4. Collect sensitive information
The page asks for a password, MFA code, payment details, or a consent prompt that grants access to mail or files.
5. Use access to scam and harm people
With those details, attackers sign in as the user, change payment info, send messages from their account, or request transfers.

Common attacks that rely on lookalike domains
1. Email-based phishing
Attackers use lookalike domains to send emails that appear authentic with subject lines: “Invoice ready,” “password reset,” “document shared”, all these linking to a phishing website.
Check: Hover the link, confirm the exact domain, and make sure the sign-in path matches what you normally use.
2. Paid search and social ads
Ads on your brand name lead to a cloned login or checkout on a similar domain.
Check: Watch for odd endings, hyphens, and add-on words like verify or refund in the address.
3. Search results for support
A convincing “help” site on a similar domain asks you to call a number or start a chat.
Check: Support pages that push phone contact first, ask for card details to “verify,” or request remote access.
4. Texts, DMs, and QR codes
Short links and QR stickers send people to phishing sign-in or payment pages.
Check: Urgency + shortened URLs, and any site asking for MFA right after you scan.
5. Account recovery prompts
A fake recovery page asks for your one-time code and uses it immediately.
Check: Only enter codes on sites you reached by typing the address yourself.
6. “Continue with Microsoft/Google” app consent
A consent screen on an evil twin website grants an unknown app access to mail or files.
Check: App name, requested permissions, and the exact domain in the browser bar.
7. Billing and vendor changes
A cloned portal or lookalike vendor domain requests new banking details.
Check: Confirm changes through a known channel before updating any payment info.
Why this works
- The domain is registered and looks legitimate, so people skim past small differences.
- The pages match real layouts and wording, so the process feels normal.
- The message asks for a routine action (sign in, view invoice, confirm details), so people move quickly.
Why Lookalike Domains and Phishing Attacks Are So Dangerous
Lookalike domains combine a believable design with real, legally registered web addresses. That mix makes them hard to spot and very costly when they succeed.
Here’s what’s at stake and how it shows up in day-to-day operations.
1. Financial impact
Attacks that start on a lookalike domain don’t stop at a fake login page. They lead to account takeovers, fraudulent payments, incident response work, legal help, and customer support surges.
Costs stack up:
- Lost sales.
- Increased support and refund costs.
- Long-term drop in customer lifetime value.
- Recovery work across IT and finance.
Many companies also feel pressure to adjust prices to cover fallout.
2. Technical sophistication
Modern fake sites look clean and “valid.” They use HTTPS, real certificates, and often publish SPF/DKIM/DMARC on the sending domain.
That technical “care” helps them slip past quick checks and some filters. On mobile, small screens and truncated URLs make it even easier to miss a subtle change in the address.
3. Business disruption
One successful click can slow a company down very quickly. Things like password resets, account lockouts, phishing cleanup, and customer outreach pull teams away from their core work.
In some cases, stolen access leads to malware or ransomware. Without strong detection and automation, the cleanup drags on and keeps costs high.
4. Regulatory and legal exposure
If customer or employee data is involved, you may face breach notifications, investigations, and fines under privacy rules. Advertising claims, deceptive design, and consent flows also draw attention from regulators.
On the domain side, brand abuse drives more disputes and takedown actions. You need a clear, documented process to show you acted quickly and in good faith.
Bottom line: Lookalike domains work because they feel familiar and pass casual checks.
Learn more: How lookalike domains damage businesses
How to Detect Lookalike Domains and Phishing Websites
Identifying these sites early takes a few layers working together: block suspicious traffic, spot new registrations as they go live, and train people to slow down when something looks almost right.
This is how to do it:
1) Automated detection (your first line)
a. Protective DNS (network-level blocking)
Filter DNS requests so risky domains never load in the browser. Use threat feeds that flag new, lookalike, and known-bad domains.
b. Email and link protection
Scan links in email, chat, and documents before delivery and again at click time. Rewrite links so clicks get checked in real time.
c. Machine learning URL analysis
Score URLs by structure (length, characters, added words like login/verify), hosting, and page behavior. Pair this with “does the page look like ours?” checks.
d. Brand monitoring
Watch for new domains that resemble yours, ads using your name, and profiles that point to fake sites. Monitor certificate transparency logs to catch SSL certificates issued for lookalike domains. You can check out our brand protection solution to see exactly what it does for you.
2) Manual checks (quick inspections anyone can do)
a. Read the core domain
Ignore the beginning. Read right-to-left to the first “/” and confirm the exact domain and ending (.com vs .co, .shop, country codes).
b. Look for small changes
Swapped letters (rn vs m), numbers for letters (0 for o, 1 for l), extra hyphens, or add-on words like login, verify, support, billing.
c. Sense check the path
Does the page ask for full credentials or an MFA code outside your normal login flow? Does the consent screen grant broad access (e.g., “read and send mail”) to an unknown app?
d. WHOIS at a glance
Red flags: registered very recently, privacy-protected owner, unusual registrar for your region, many similar domains on the same day.
e. Basic technical tells
- SSL: missing lock, or the certificate is for a different name.
- DNS/MX: no mail records for a “support” domain, or odd mixes of providers.
- Hosting: brand-new site hosted with a low-cost provider used across many spammy domains.
3) Visual and content cues
- Fonts, icons, or spacing slightly off compared to your real site.
- Buttons that open a sign-in in a new tab on a different domain.
- Forms that ask for card/bank details before login.
- Download prompts for “security tools,” drivers, or VPNs from a lookalike domain.
4) Evidence you should capture (for takedown and response)
- Full-page screenshots (include the address bar).
- The exact URL, plus the link you clicked (from the email or ad).
- WHOIS details, registrar, and hosting IP.
- SSL certificate details (issuer, valid-from date).
- Any files served and where forms submit data.
Tip: Type the address for anything sensitive (login, payments, recovery). If the path or domain is even slightly off, stop and report it.
Examples of Phishing Websites Using Lookalike Domains
Real incidents show how small domain changes and familiar layouts lead people to share credentials or payment details.
Here are some examples:
1. Financial services
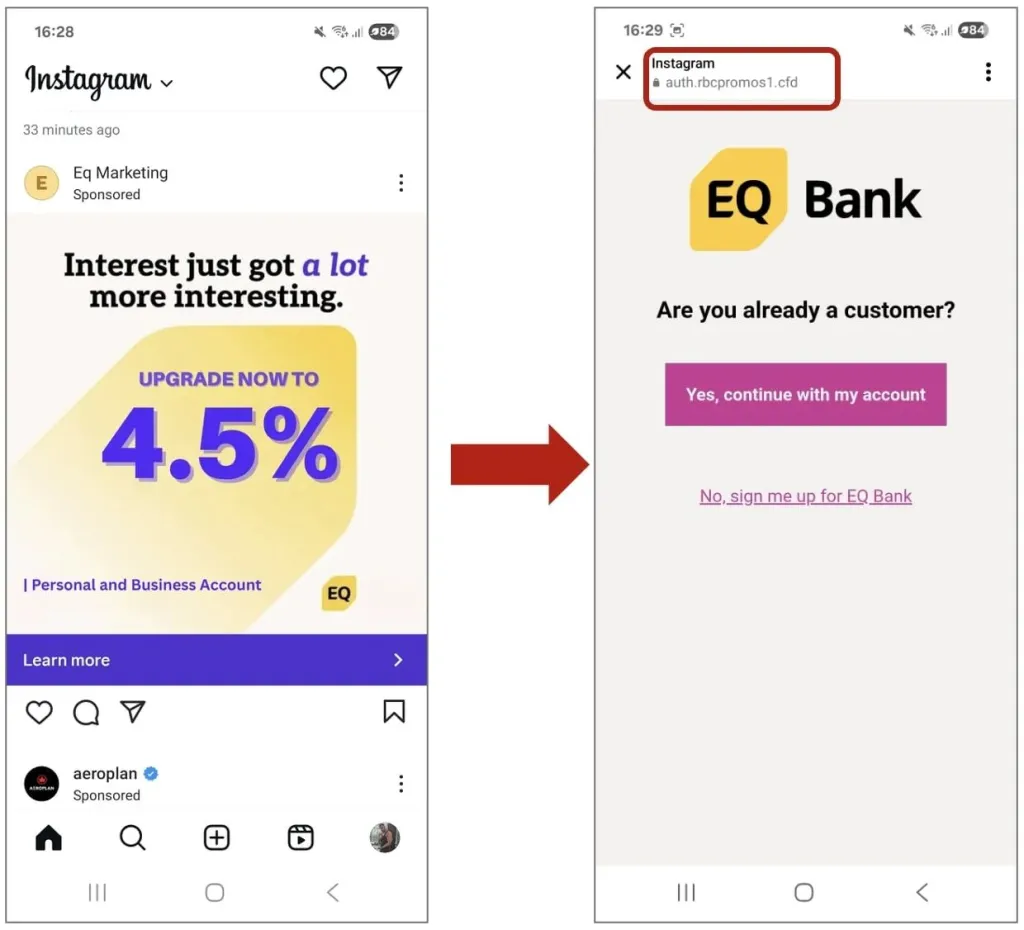
a. EQ Bank impersonation via social ads
Scammers ran Instagram ads that copied EQ Bank branding and sent people to fake banking pages hosted on lookalike domains. Several security teams warned about this pattern targeting Canadian banks, including EQ Bank.
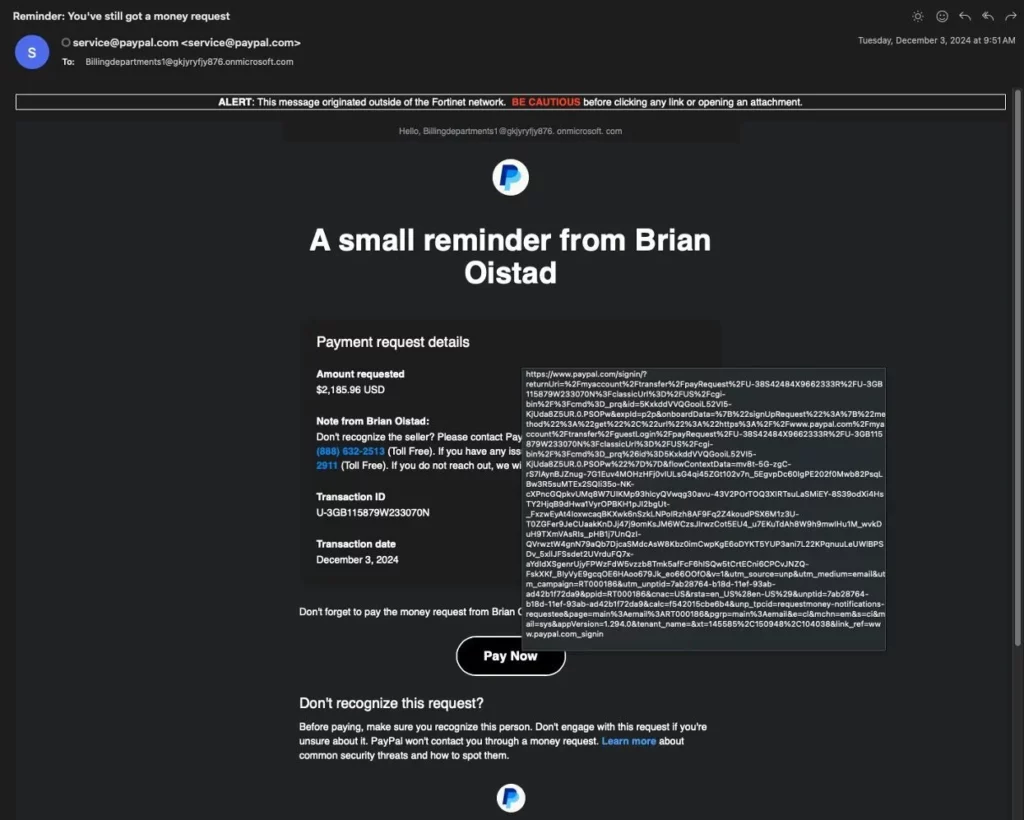
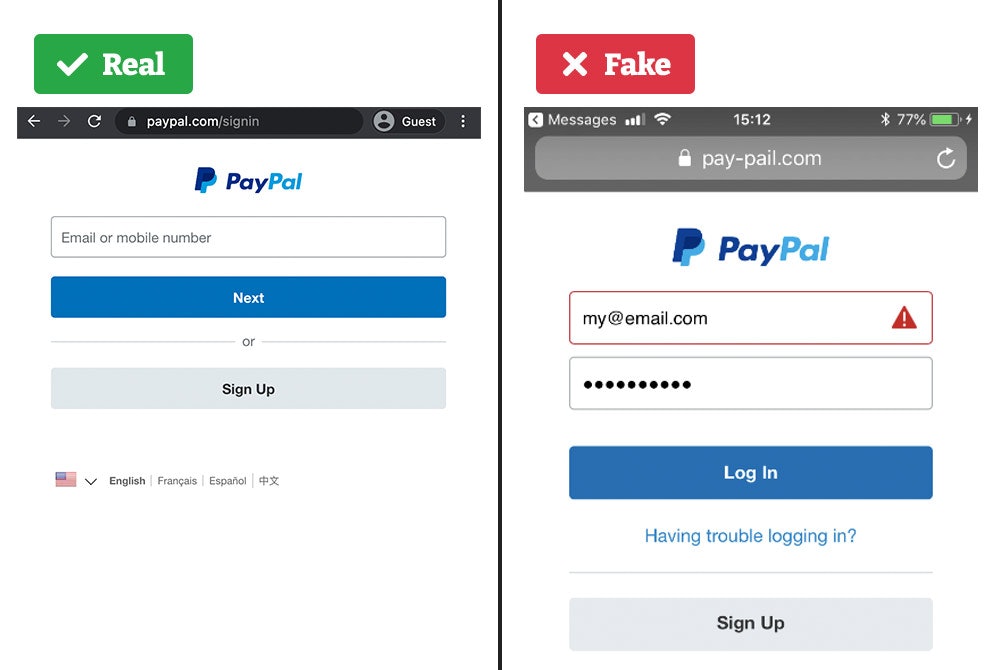
b. PayPal login clones on lookalike domains
Attackers continue to host PayPal-style sign-in pages on domains that look close to the real thing, aiming to capture credentials and card data.
2. Technology brands
a. Microsoft 365 sign-in replicas
Microsoft remains a top target for brand impersonation, with fake Microsoft 365 login pages appearing on phishing websites. Multiple reports in late 2024 and early 2025 rank Microsoft as the most impersonated brand.
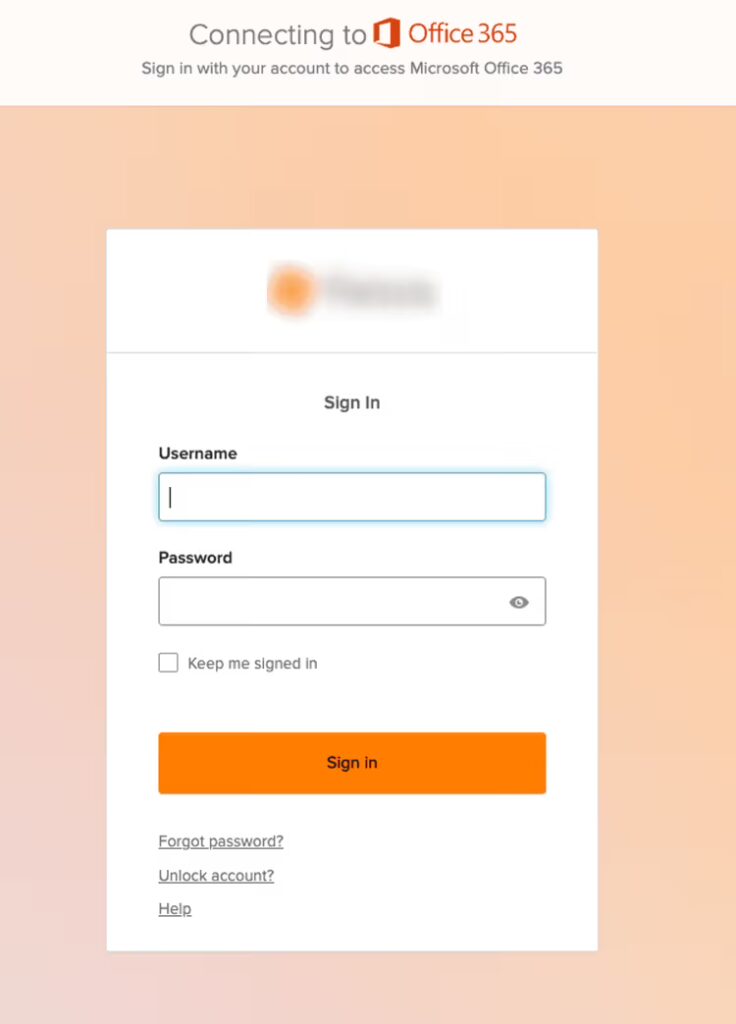
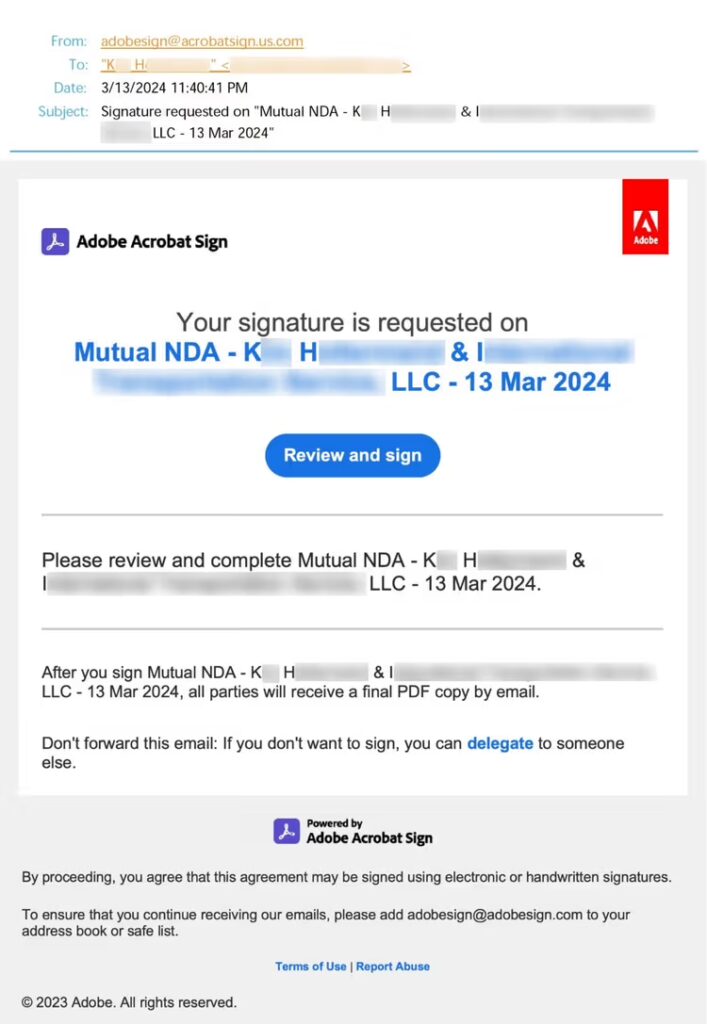
b. Adobe Acrobat Sign impersonation
Campaigns have delivered “Review and sign” messages that lead to pages styled like Acrobat Sign, often customized with the victim company’s logo, to collect credentials or OAuth consent.
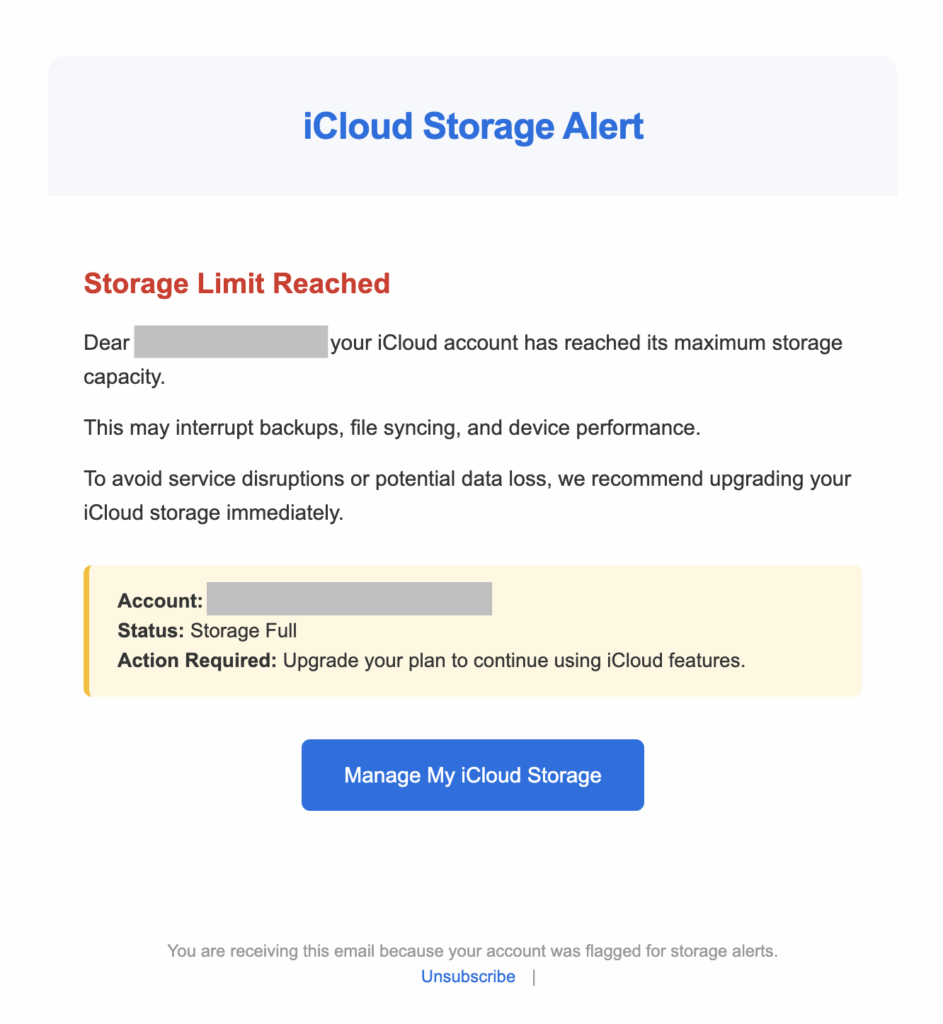
c. iCould storage alert
A phishing email pretending to be an iCloud storage alert. It pushes you to click “Manage My iCloud Storage” and sign in or pay on a website that looks like Apple but isn’t
These cases share the same pattern: A registered domain that looks close to the real one, a page that mirrors the brand, and a prompt to sign in, share a one-time code, or download software.
Keep the exact-domain check front and center, and report any evil twin website you see so they can be taken down quickly.
How to Take Down Fraudulent Sites Using Lookalike Domains
There are two ways to handle takedowns.
A manual path you can run with internal effort, and an automated path using a purpose-built platform.
Here’s how they differ and what each involves.
Option 1: Manual takedown (hands-on, time-intensive)
1. Collect proof
- Full-page screenshots with the address bar visible.
- The exact URL, page source, where forms send data, any files served.
- WHOIS, nameservers, hosting IP, SSL details, and timestamps.
2. Prioritize
- Payment or credential capture first.
- Executive or vendor impersonation next.
- Inform support/comms so they can guide customers to the correct domain.
3. File abuse reports (in parallel)
- Registrar/Registry: Request domain suspension for phishing/brand abuse.
- Hosting/CDN: Request content removal for policy violations.
- Search/Ads: Remove paid ads and search listings that drive traffic.
- Certificate Authority: Revoke the certificate used on the fake site.
- Social/Messaging: Remove posts or profiles that send users to the domain.
- Payment processors: If card data is collected, notify their designated teams.
Include: Evidence, a short impact summary, and the specific policy each party enforces (phishing, brand misuse, malware, deceptive practices).
4. Track and escalate
- Log ticket numbers, deadlines, and responses
- If stalled, escalate to the registry or upstream network, request browser blocklisting, and push search/ads delisting again
- For persistent cases, start a UDRP/ACPA process with the evidence already packaged
5. Watch for reappearances
- Manually monitor for new lookalike domain registrations (same email, ASN, nameserver, certificate pattern)
- Keep a case history so that repeat domains are taken down faster
Option 2: Automated, AI-driven platform
Use a dedicated platform when speed and repeatability matter. The platform discovers lookalike domains and alerts you as they go live (24/7 monitoring), assembles proof, routes the request to the right provider, and tracks status, all in one place.
It also monitors re-registrations and related domains, so repeats are handled efficiently.
This is how it’s done:
1) Discover, monitor, and verify
- Detect and monitor lookalike domains and pages that impersonate your brand or executives.
- Auto-gather WHOIS, hosting, SSL, creation date, and related infrastructure.
- Confirm misuse with screenshots, content match, and form destinations.
2) Score & prioritize
- Use a Digital Risk Score to rank by business impact (credentials, payments, executive/vendor, malware).
- Surface top cases for immediate action.
3) Build the evidence pack
- Bundle URLs, screenshots (with address bar), WHOIS, IP/ASN, SSL, redirects, and policy fit (phishing, brand/copyright misuse, deceptive practices).
4) Submit to the right parties
- Send requests to registrar/registry, host/CDN, search/ads, CA, social/messaging, and payment processors.
- Include the correct policy language each provider enforces.
5) Track and escalate
- Show live status (submitted/in progress/actioned).
- Auto-escalate if timelines slip (alternate contacts, upstream network, additional proof).
6) Watch for re-registrations
- Monitor for new variants by the same actor (using the same infrastructure/certification patterns).
- Link clones to the same case family to speed future takedowns.
7) Report & learn
- Produce audit-ready summaries (what was found, who acted, when, and outcome).
- Feed indicators back into email/web/DNS tools to reduce repeat exposure.
That’s the clean split: The manual route you can run with internal effort, and the automated route that removes busywork and shortens the time from detection to takedown.

See it in action.
If you’re ready to cut the manual work and speed up lookalike domain takedowns, book a demo to see how an automated, purpose-built platform handles discovery, evidence, and take downs end-to-end.
















