Disinformation Security: The Next Cyber Discipline Every Organization Will Need

Most security teams focus on the threats they can see, such as breaches, ransomware, and account takeovers. But some of the most damaging threats grow outside your perimeter, on platforms you do not control, and in places your tools do not monitor. That is where disinformation lives. Scammers do not need to break into your […]
The Future of the CISO Role: Brand Trust and External Threats

Most security leaders still measure their work in alerts, incidents, and controls. That work matters, but it is no longer the main thing your company expects from you. The next stage of the CISO role has nothing to do with firewalls or cloud policies… it has everything to do with trust. Boards and executive teams […]
Understanding Your Attack Surface: Why EASM Is So Critical for Today’s Businesses

Why You Need to Understand Your Attack Surface Unfortunately, most organizations underestimate how visible they really are. They think their “attack surface” is only their main website, email servers, or cloud instances. However, the attack surface goes far beyond that; it includes: Each one carries your brand name or domain, which means attackers can use […]
Lookalike Domain Attacks by Industry: Why Every Sector Faces Rising Digital Risk
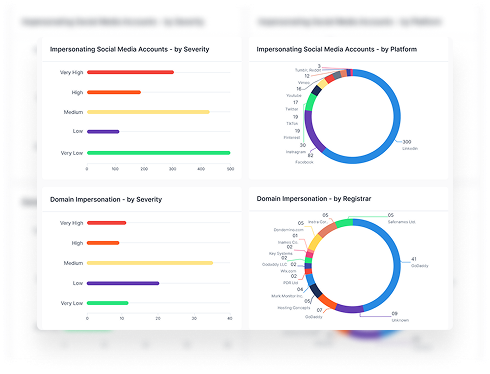
How Lookalike Domains Damage Businesses Lookalike domains and phishing websites disrupt trust, slow operations, and yes, they cost a lot of money. One impersonated site or phishing email can set off a chain reaction across your business. Here are some examples: 1. Tangible Costs The first hit is financial. For many companies, even a single […]
How Lookalike Domains Damage Businesses

What Lookalike Domains Really Are (and Why They Work) We have an entire post on what lookalike domains are and how to deal with them, but in short, a lookalike domain, sometimes called a spoofed or impersonated domain, is a fake version of a legitimate company’s website address. It might change a single letter, replace […]
Top 10 Cyber Threat Tactics in 2025 (And How to Spot Them Early)

The top cyber threats in 2025 aren’t all new, but they’ve changed. Attackers are using deepfakes, fake updates, stolen access, and QR codes to trick people and damage businesses. Although these tactics might seem simple, they’re effective and hard to stop. This article shows you the top 10 tactics threat actors are using right now, […]
Lookalike Domains and Phishing Websites: How to Find, Block, and Take Them Down

Cyber threats are getting harder to spot. Lookalike domains sit at the center of modern phishing attacks, costing businesses over $100 billion globally in 2024. These attacks don’t look suspicious anymore. They use proper security certificates, clean design, and domains that fool even careful readers. Here’s what you need to know to protect your business. […]
How to Spot and Take Down Fake LinkedIn Accounts

What Is LinkedIn Impersonation? (Fake LinkedIn Account) LinkedIn impersonation refers to any unauthorized use of your brand, people, or assets on LinkedIn to appear legitimate and gain trust. Attackers either create new fake LinkedIn accounts or hijack existing ones, then use that credibility to collect data, steal money, or manipulate users/customers. You’ll typically see it […]
The Future of Digital Risk Protection: Why Your Next Cyber Defence Lives Outside the Perimeter

The Future is Digital Risk Protection Yes, Digital Risk Protection (DRP) will move to the center of your security program. This means that DRP will be THE TOOL to help you find and take down external, public-channel threats tied to your brand, people, domains, or data. Over the next few years, attackers will focus on […]
Doxing: What It Is, Why It’s Growing, and How to Protect Executives and Families
What Does Doxing Mean? Doxing (sometimes spelled doxxing) is the deliberate collection and release of someone’s personal information without consent to apply pressure, cause harm, or gain leverage. The harm isn’t just that details are public… It’s that an attacker packages them, adds context, and pushes them to an audience that will act on them. […]