The top cyber threats in 2025 aren’t all new, but they’ve changed.
Attackers are using deepfakes, fake updates, stolen access, and QR codes to trick people and damage businesses.
Although these tactics might seem simple, they’re effective and hard to stop.
This article shows you the top 10 tactics threat actors are using right now, and what to do about each one.
1) Initial Access Brokers (IABs)
Initial Access Brokers (IABs) break into organizations first, then sell that foothold to other criminals. The “product” can be stolen VPN credentials, active RDP access, web shells on edge devices, or full domain logins. Ransomware groups and other crews routinely buy this access to speed up attacks.
How it shows up
- New VPN or RDP logins from unusual locations, sometimes without strong MFA
- Sudden privilege jumps on regular users, new local admins, and new high-risk groups
- First-seen remote tools or web shells on gateways and servers
- Fast lateral movement after the first login, directory discovery, and auth spikes
What to do
- Use MFA everywhere, prefer FIDO2 or WebAuthn, and add number matching for pushes
- Watch identity signals, alert on first-time VPN device, new geo, disabled MFA, sudden role or group changes
- Cut remote exposure, turn off unused RDP, enforce device posture on VPN, patch edge and RMM tools, and alert on first-seen admin tools
- Contain early movement, baseline directory queries, watch for mass auth failures and token theft right after odd logins
2) Multimodal Deepfake-Enabled Impersonation
Attackers clone voices and faces to pose as executives, vendors, or family members. They run this over video calls, phone calls, and chat. The goal is to get quick approval for payments, credentials, or sensitive files.
Law enforcement and government agencies have warned about voice cloning and deepfake fraud against businesses.
How it shows up
- A video call with “familiar” faces that push an urgent transfer or document share, often after hours. Example: Hong Kong police confirmed a $25M loss tied to a deepfaked multi-person meeting that imitated senior staff at a global firm.
- A phone call that sounds like your CFO or CEO asking for bank details, gift cards, or a wire change.
- A chat or email that moves you to a quick call to “confirm,” then rushes a new payee or changed banking info.
What to do
- Verify out of band for irreversible actions, call back on a saved number, use two-person checks for new payees and bank changes
- Give finance and executive assistants a simple rule: if a request mixes urgency and secrecy, pause and verify on a known channel
- Limit what one approval can move, use thresholds, dual control, and short delays for first-time beneficiaries
- Train on basic tells, lip and audio out of sync, odd background blur, robotic cadence, and requests to switch to a personal device
Learn more: Executive Protection Hygiene: The Playbook
3) Beating MFA Via Fatigue, Token Abuse, and Multi-Channel Social Engineering
Attackers flood your phone with MFA prompts until someone taps approve. They also steal active sessions from browsers so they can skip MFA. They add pressure with calls, texts, or DMs asking you to “just confirm.”
How it shows up
- MFA prompts when you didn’t try to sign in
- A call or text telling you to approve to “stop the prompts”
- A sign-in from a new place or device right after those prompts
- Consent screens for unknown apps asking to read or send your mail
What to do
- Use passkeys or security keys where you can
- Turn on number matching and show app name and location in prompts
- Block repeated prompts and ask for a fresh login if anything looks odd
- Re-check identity for money moves, mailbox rules, password or MFA changes
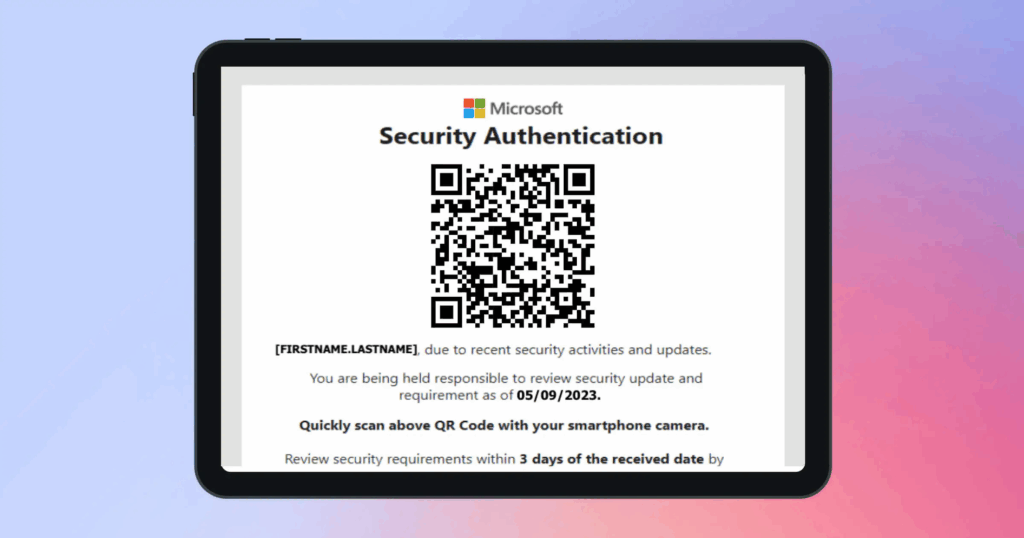
4) Quishing: QR-led Phishing
Scammers hide the link inside a QR code so filters don’t see it. You scan on your phone and land on a lookalike page that asks for a password, a one-time code, or app access. It works because people scan quickly, and phone browsers hide parts of the address.
How it shows up
- Email or PDF with a QR to “verify account,” “update MFA,” “view invoice,” or “track delivery”
- Stickers slapped on posters, doors, kiosks, or conference signs
- Event badges and handouts with “quick login” or “secure check-in” codes
- A QR that opens a page on a lookalike domain right after you scan
What to do
- Don’t scan a QR to log in, reset MFA, or change payment details
- Type the address or use a saved bookmark for anything sensitive
- Turn on web filtering and threat protection on phones, not just laptops
- Auto-quarantine emails that mix a QR with “verify,” “reset,” “MFA,” or “account update” language
- Walk your spaces and remove slapped-on QR stickers, replace tampered signs
- Give people one place to report suspicious QRs with a screenshot and the opened URL
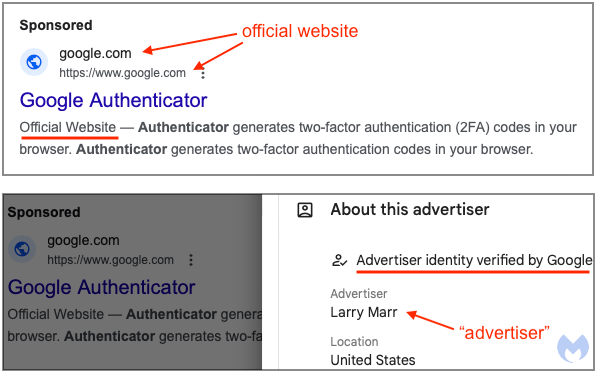
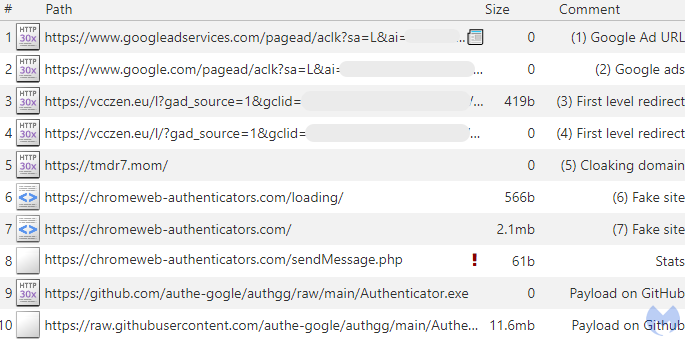
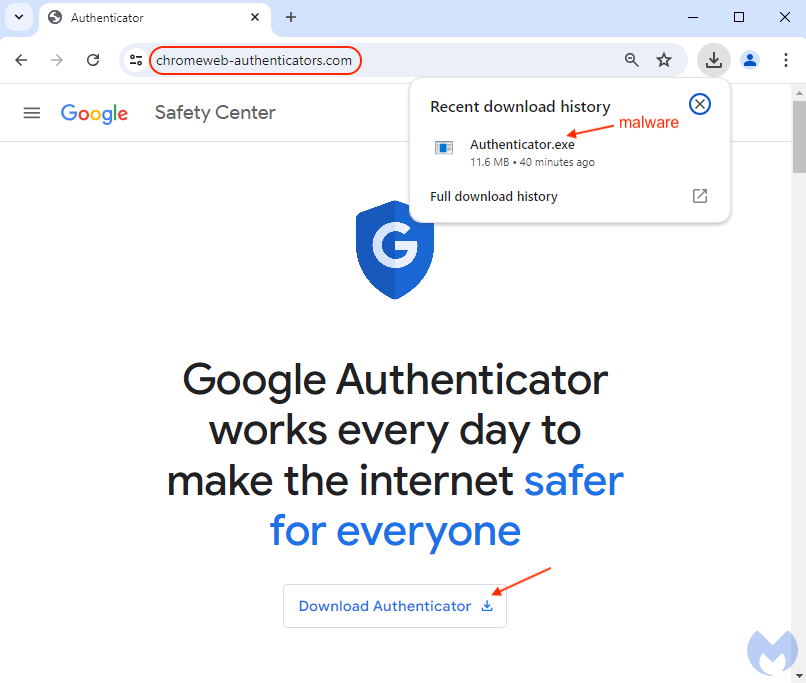
5) Search-Led Compromise: SEO Poisoning and Malvertising
Scammers buy ads on brand names, push fake “top” results, and create phishing websites that mimic real ones. They also create fraudulent support pages with a phone number that directs calls to a call center, where someone tries to convince you to install malware as a “fix”.
Some campaigns exploit URL parameters to insert a fake phone number into help pages. The same tricks show up in AI assistants that pull links from the web, so a bad result gets even more reach.

How it shows up
- You search “Zoom download,” “Adobe Reader,” “bank support,” “Google Authenticator,” and the first result looks right, but it’s a phishing website.
- A “Support” result shows a big phone number, and the agent asks for remote access or payment
- Ads that use your brand name, but the landing page uses a lookalike domain. Learn more: Brand Impersonation Takedowns
- AI answers that cite a lookalike site for “official download” or “help center”
What to do
- Lock software installs to a safe list, company app store, managed browser downloads, no random EXEs from search
- Publish official links and numbers on your own channels, and pin them where users actually look, such as the login page and help center.
- Monitor brand keywords and lookalike domains, especially paid ads that use your name
- Teach the quick check, read the exact domain, type the address for downloads or support, and avoid calling a number you found in a search result
- Report fake ads and fraudulent results, cut their traffic while you begin the takedown
- Add a “safe path” banner on common tasks, how to download, how to contact support, and one click to the real page
6) Software Supply Chain Pivots
Attackers are targeting the tools and packages teams install every day. They take over maintainer accounts, push “new versions” that steal tokens or change builds, and inject code that spreads by itself through scripts and GitHub Actions.
How it shows up
- A “hotfix” release adds new install scripts or network calls you didn’t expect
- CI makes outbound requests to odd domains right after an update
- Developers see warnings during install, but everything still completes
- Production reaches a new domain soon after a deploy
- A maintainer “handoff” post is followed by a release that behaves differently
What to do
- Lock how software is pulled, use an internal package proxy and approved registries only
- Require signed releases and signed builds, block if the signature or attestation is missing
- Add new dependencies through a simple approval step, freeze by default
- Watch for version spikes across many packages, or a tiny library jumping versions quickly
- Keep CI secrets short-lived and scoped. Don’t expose them to every job
- Keep an up-to-date inventory of what runs in builds and in prod, scan on each build and after deploys
- Treat install-time scripts as risky, review or block packages that run post-install hooks
- Be ready to roll back when needed. Pin to the last known good version with one click
7) Fake Updates And Support Pop-Ups That Install Malware
Scammers build phishing websites and pop-ups that look like Chrome, Microsoft, Apple, or your antivirus. They display messages like “update required,” “device at risk,” or “call support.” However, the download contains malware, and the phone number directs you to a call center that prompts you to install a remote tool.
How it shows up
- A page says your browser is out of date and pushes a “critical update”
- A “support” page shows a big number, or an agent asks for remote access or payment
- Pop-ups that copy system alerts and use the right logos and colours
- You land on a real help page, but the phone number is different from the one on the brand’s site
What to do
- Don’t install updates from a web page. Use your company’s update channel or the app’s built-in updater
- Post your real download links and support numbers where people look, login page and help center
- Block executable downloads from unknown sites. Use a company app store or managed catalogue
- Teach one rule, browsers and operating systems do not ask you to call a number
- Flag first-seen downloads from the web. Review them before they can run
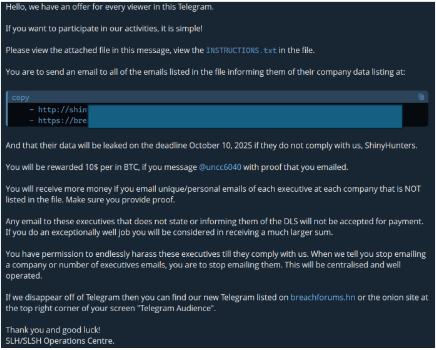
8) Coordinated Harassment Swarms Against Executives
Groups spin up “volunteers” to harass leaders online. They mass-report accounts, flood DMs and SMS, leave fake reviews, and boost lookalike profiles. They leak or fake “receipts,” doxx home info, and push urgency to force mistakes. The noise also covers more serious cyberattacks happening at the same time.
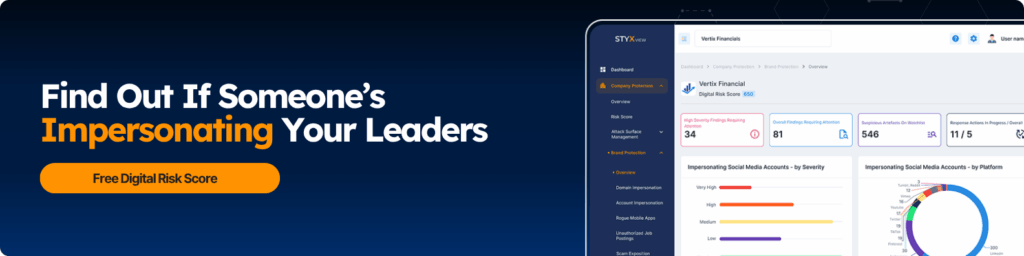
How it shows up
- Sudden spikes in mentions, tags, and reports on one executive
- New profiles that copy the exec’s name and photo, link to lookalike domains
- DM and SMS floods from fresh accounts and unknown numbers
- Review brigades on Glassdoor, Google, or app stores
- Posts sharing personal details, travel, family info, or “leaked” documents
- Login alerts and phishing attempts that rise during the swarm
What to do
- Run an executive protection playbook, find and remove fake profiles, lookalike domains, and posts that share personal info
- Lock down contact paths, restrict who can DM or comment, route public contact to a monitored inbox, and publish the official channels in bios
- Treat exec email and phone as Tier-0, use separate public aliases, enable SIM PIN and port-out locks, screen unknown calls and texts
- Rate-limit new senders, add rules for bursty mail and unknown SMS links, block link shorteners where possible
- Pre-write statements, acknowledge the swarm without amplifying it, point to the official channel, and log everything
- Save evidence, screenshots, URLs, headers, timestamps, launch takedowns with platforms, escalate if there are threats or doxxing.
- Extend protection to family, tighten privacy settings, remove home listings, opt out of data brokers, and rotate exposed info where needed
9) Third-Party and Downstream Targeting Via Access Resale
Attackers buy or get access to smaller suppliers, then use that trust to reach bigger targets. Think VPN or RDP logins, shared portals, service accounts, and app integrations.
Typically, mid-market vendors are the first to be affected.
How it shows up
- A vendor portal login from a new place or device
- New OAuth consent or API keys created for an integration you didn’t plan
- Vendor API traffic at odd hours or to new endpoints
- A service account tied to a partner suddenly gains broader scopes
- Email from a lookalike vendor domain asking for bank or scope changes
What to do
- Require strong MFA on every vendor portal and shared admin path
- Use least-privilege for integrations, narrow scopes, short-lived tokens, and rotate often
- Alert on new consents, new API keys, new scopes, and first-time endpoints
- Add a kill switch for each integration, be able to revoke tokens and block IPs fast
- Allowlist vendor IPs where possible, log all vendor traffic, and review after every change
- Put it in contracts, passkeys or security keys, SSO, logging, and 24-hour revocation support
- Verify the sender and the domain before you accept any vendor request to change scopes, keys, or banking details
- Run a simple drill, disable one critical vendor integration and restore it, and fix the gaps you find
Learn more: Third-Party Risk Management: Everything You Need to Know
10) Data Theft-First, Encryption-Optional Extortion
Attackers steal your data and threaten to publish it, sometimes without even encrypting it. They buy access or use info-stealers, grab files, then try to force payment by posting samples on their own website, by emailing your customers, or by blasting it on social.
The damage comes from exposure, not downtime.
This highlights the importance of brand reputation and how attackers leverage it to achieve their goals.
How it shows up
- Big downloads from file shares or cloud storage in a short window
- Sudden creation of large ZIP or RAR archives on desktops, jump hosts, or build servers
- Traffic to personal cloud or file-sharing sites you don’t allow
- Service accounts pulling data they’ve never touched before
- New scheduled tasks or scripts that stage data in a “temp” or “backup” folder
- Password-protected archives or exfil tools dropped in user profile folders
- A small initial breach window followed by a leak site “countdown” post
What to do
- Watch for staged exfiltration, large archives, cloud-to-external transfers, and unusual egress destinations
- Lock down service accounts, least privilege only, short-lived tokens, monitor new scopes, and bulk reads
- Block personal cloud and unknown file-sharing sites, and allow only approved destinations
- Alert on mass downloads, first-time access to sensitive buckets, and archive creation on servers
- Use DLP on endpoints and cloud, add simple rules for credit cards, customer lists, source code, and HR exports
- Watermark and canary sensitive datasets so you can confirm exposure fast
- Keep a clean rollback and a comms plan, know who notifies customers and regulators, and how you’ll prove what left and what didn’t
Attackers today buy access, fake people on calls, spam MFA, push QR codes, poison search, tamper with packages, pressure leaders, and steal data to force payment.
How can Styx help?
Styx is an AI-powered platform built to help companies monitor, detect, and act on external threats across domains, social media, executive presence, third parties, and even activity on the dark web.
Connect with our team to discover how we can help protect your brand from these tactics and more.