In this article, we break down what Digital Risk Protection is, why it matters right now, what it protects you from, and how it works — without the fluff.
You’ll learn who needs it, how real companies are using it, and what to look for if you’re evaluating a DRP platform for your own team.
If you’re responsible for brand protection, security, legal risk, or just want to know what’s really out there with your name on it — this is for you.
Let’s begin.
What Is Digital Risk Protection (DRP)?
Digital Risk Protection (DRP) is a cybersecurity discipline focused on identifying, monitoring, and mitigating threats across your entire digital footprint.
That includes all the exposed parts of your organization that live outside your network — things like domains, cloud infrastructure, mobile apps, brand assets, third-party services, and anything else tied to your name online.
DRP looks for threats across the open web, dark web, social platforms, and more. It helps you spot risks that involve your brand, people, or data — even if they start somewhere else entirely.
This can include things like:
- Brand impersonation
- Leaked data or credentials
- Phishing infrastructure
- Executive or employee targeting
- Exposure from third-party breaches
- Threat intelligence
Traditional tools aren’t built to see these risks. DRP fills that gap — giving you visibility and the ability to act early.
Check out more about The Future of Digital Risk Protection here.
Why Is DRP Important?
Your digital presence is bigger — and more exposed — than ever. Cloud tools, remote work, third-party platforms, and open data have made business faster. But they’ve also created new entry points for attackers.
Threats today don’t always come through the front door. They show up on fake websites, leaked credentials, phishing emails, or impersonation scams on social media — often before your internal systems even notice.
And with AI making it easier to create fake messages, deepfake videos, and cloned voices, these attacks are getting more believable by the day.

That’s why Digital Risk Protection matters.
It helps you:
- Stop breaches before they start.
- Reduce financial and reputational harm.
- Protect your brand and your people.
- Strengthen overall cybersecurity posture.
- Keep businesses running smoothly.
- Protect your company’s narrative and identity.
As your organization grows more connected, so do the risks. DRP helps you see them, prioritize them, and act fast — before someone else does.
What Does DRP Protect You From?
A robust DRP solution helps identify and mitigate a wide range of digital risks, including:
- Brand impersonation: Fake websites, social media accounts, mobile apps, and unauthorized use of your logo or brand identity.
- Data leaks: Stolen credentials, sensitive documents, or customer data exposed.
- Phishing and scam campaigns: Lookalike domains, fraudulent landing pages, and social engineering schemes targeting your employees or clients.
- Executive and employee targeting: Doxxing, impersonation attempts, and personal data leaks used for attacks. Learn more about executive impersonations here.
- Dark web chatter and data sale: Mentions of your company or assets on dark web forums and marketplaces.
- Misconfigured systems and exposed assets: Publicly accessible services, misconfigured cloud buckets, or open ports that expose your organization to attack.
- Third-party risk visibility: Exposure coming from vendors, suppliers, or partners — especially important in regulated industries.
- Unauthorized content and misinformation: Content that falsely claims affiliation or spreads misleading information tied to your brand.
These threats often live outside your direct control — DRP brings them into view so you can act fast.
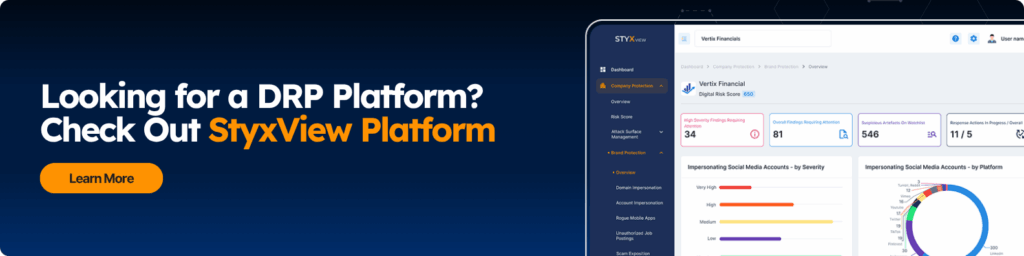
How Does Digital Risk Monitoring Work?
Digital Risk Monitoring provides visibility and surfaces risks that traditional cybersecurity platforms often fail to detect — especially those emerging outside your network perimeter.
Here’s how it works here at Styx:
1. Identify
Start by mapping your digital footprint. This includes everything tied to your brand online — domains, cloud assets, executives, social handles, vendors, apps, and other exposed infrastructure.
2. Analyze
Once your surface is mapped, DRP looks for gaps. That could be misconfigurations, impersonation risks, exposed systems, or leaked data connected to your environment.
3. Monitor
Watch for threats across the open web, dark web, social media, messaging apps, cloud services, app stores, forums, and file-sharing platforms.
The platform continuously scans these environments using a mix of proprietary and open-source data — powered by AI, pattern recognition, and real-time search — to spot risks early and at scale.
What it’s looking for:
- Brand mentions, logos, or executive references.
- Suspicious domain registrations and fake infrastructure.
- Leaked credentials or internal documents.
- Threat actor chatter or signs of planned attacks.
4. Prioritize
Every threat is scored using the Styx Digital Risk Score — a dynamic scoring system that looks at impact, exposure, and urgency. It helps you understand which threats matter most and which ones can wait.
This means your team can act on the right risks, faster — without getting buried in alerts or false positives.

By the way, you can learn everything about how our Digital Scorecard works here.
5. Remediate
If something needs to be taken down — a fake site, leaked data, or a phishing campaign — you can kick off takedown requests directly from the platform. Check out this article to learn everything about takedowns
6. Report
Generate reports with context-rich insights to help your security team, leadership, or non-technical stakeholders understand what’s happening and what’s being done.
By tying all these pieces back to your digital footprint, DRP delivers the context you need to move quickly and confidently.
By tying all these pieces back to your digital footprint, DRP delivers the context you need to move quickly and confidently.
Core Capabilities of a DRP Solution
A Digital Risk Protection Platform isn’t a single tool — it’s a set of capabilities that work together to help you see what’s happening outside your network, and respond when it matters.
Here’s what those capabilities look like:
1. Comprehensive Digital Footprint Mapping
Track everything connected to your organization online — including domains, subdomains, cloud assets, mobile apps, vendors, and more. A clear view of your external exposure makes it easier to know what needs protection.
2. Brand Protection
Attackers often misuse a company’s logo, name, or website look to build fake sites, scam customers, or launch phishing campaigns. Brand protection tools help detect this type of misuse early, so it doesn’t spread unnoticed. Here is what brand protection is, and why it matters.
3. Phishing Detection and Prevention
Phishing is still one of the most common attack methods. Lookalike domains, fraudulent landing pages, and fake login portals are designed to steal credentials. Detecting these fast means less damage — and fewer people tricked.
Learn more: 7 Costly Ways Brand Impersonations Are Hurting Your Business.
4. Data Leakage Detection
Sensitive data doesn’t always leak from your own systems — it could come from a vendor, employee device, or cloud bucket. DRP tools monitor the surface, deep, and dark web for exposed credentials, documents, or databases connected to your organization.
5. Executive Protection
High-level employees are frequent targets. Their names, photos, and communication styles are often online — which makes impersonation easier. Monitoring for executive/leader impersonations helps protect both the individual and the organization.
6. Social Media Monitoring
Fake accounts and impersonations on social platforms are used for scams, phishing, or disinformation. Monitoring for brand mentions and account abuse gives you a chance to act before it escalates.
7. Adverse Media Monitoring
When a story about your company starts gaining traction — whether it’s accurate or not — it helps to know early. Adverse media monitoring tracks blog posts, news coverage, and online conversations that could impact your reputation.
8. Sentiment Analysis
Understanding public perception is key. Monitor tone and sentiment across various platforms to help you gauge how people feel about your brand and identify potential issues, misinformation, or loss of trust.
9. Dark Web Monitoring
Many threats emerge where traditional tools don’t look. DRP platforms scan dark web forums and marketplaces for stolen credentials, internal data, or mentions of your company in attack planning.
10. Third-Party Risk Management
Even if your own systems are secure, third parties you rely on might be vulnerable. DRP platforms often include tools to monitor vendor exposure, track breaches, and assess partner risk levels using digital risk scores — so you can focus on the suppliers that matter most.
11. Integrated takedowns
Sometimes you need to take action quickly — like taking down a phishing site, shutting down a fake account, or responding to leaked data. Takedown workflows help make that process faster and smoother.

These are the types of capabilities that make up a real DRP strategy — and they’re the ones built into our platform.
Who Needs Digital Risk Protection?
Digital Risk Protection platforms are no longer a nice-to-have. If your company has a digital presence, uses cloud platforms, works with third parties, or interacts with customers online, DRP matters.
DRP By Industry
1. Finance
DRP helps prevent fraud and phishing attacks aimed at customers or employees. It also supports compliance and gives early warnings when credentials or sensitive data show up online. Learn more about protecting financial institutions here.
2. Healthcare
Patient data is a big target. DRP helps detect medical record leaks, impersonation attempts, and ransomware chatter — especially across the deep and dark web.
3. Retail & eCommerce
From fake product listings to counterfeit websites, brand impersonation is everywhere. DRP helps spot fraud, protect your brand, and respond to scams before they hurt your customers.
4. Technology & SaaS
Digital platforms often face copycats, IP leaks, and impersonation — especially of founders or engineers. DRP helps monitor for exposed code, stolen credentials, and misuse of your tools or branding.
5. Manufacturing & Supply Chain
Designs, plans, and supply chain details are often shared online — sometimes unintentionally. DRP helps prevent unauthorized sharing and keeps third-party leaks from catching you off guard.
6. Government & Public Sector
Public services and institutions are frequent targets for impersonation, misinformation, and fraud. DRP adds visibility and protection beyond internal systems. Learn more about how DRP helps government and public sector services.
7. Telecom
Telecom providers handle vast amounts of sensitive data. DRP helps monitor for customer-targeted scams, exposed infrastructure details, and threats against public-facing assets.
DRP By Role
1. Security Operations Teams
DRP adds external threat intelligence — helping SOC teams detect and respond to risks happening outside the perimeter.
2. Risk & Compliance Officers
External exposure can lead to legal or regulatory issues. DRP helps identify those risks early, including data leaks and vendor-related threats.
3. Brand & Marketing Teams
When your logo or product gets misused, it’s not just frustrating — it’s a reputational risk. DRP helps you stay ahead of impersonation, counterfeit listings, and social media abuse.
4. Legal Teams
DRP can support evidence collection, takedown requests, or incident response — especially for cases involving impersonation, copyright abuse, or leaked confidential data.
5. Executive Security Teams
High-profile employees face growing risks from impersonation, deepfakes, and doxxing. DRP helps monitor for these threats before they’re used in a scam or attack.

In short: If your organization is online — and especially if you have something to protect — DRP helps you see what’s out there and reduce the risk before it turns into something bigger.
Real-World Use Cases for DRP
Digital Risk Protection helps detect threats before they turn into full-blown incidents. These aren’t abstract risks — they show up in everyday business.
Here are some examples of how DRP makes a difference.
1. Phishing Website
A bank’s fraud team received a call from a confused customer trying to verify a wire transfer request that had never been sent.
The team traced the issue to a fake website — identical in look, feel, and branding — set up to trick clients into entering their login info.
DRP flagged the domain hours after it was registered, and a takedown was initiated before more customers were affected.
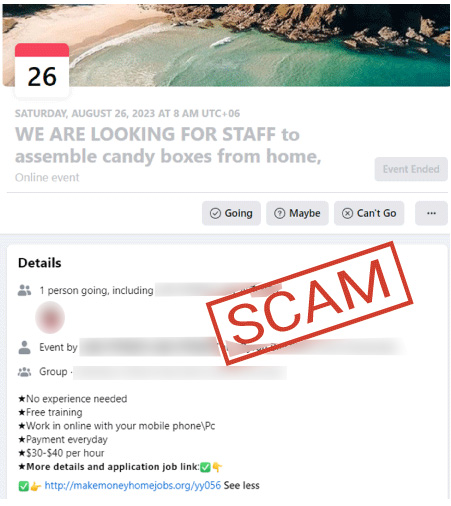
2. Fake Job Listings
An HR team started getting emails from people thanking them for job offers they never made.
Turns out, scammers had set up fake recruiter profiles on LinkedIn and were emailing “candidates” official-looking contracts asking for passport copies and banking details.
DRP uncovered the impersonation campaign by tracking brand mentions and rogue accounts across job boards and social media.
3. Leaked Credentials
A SaaS company detected a spike in suspicious logins. DRP tools scanning the dark web had picked up on a fresh dump of internal credentials — stolen during a third-party breach.
The security team reset the impacted accounts and rolled out multi-factor authentication (MFA) to prevent unauthorized access.
4. Counterfeit Product Listings
A global apparel brand noticed customer complaints about poor-quality items that they never made.
DRP surfaced multiple online stores — many on popular marketplaces — selling counterfeit goods under the company’s name.
With screenshots and evidence, the team issued takedowns and blocked the sellers.
5. Executive Impersonation
An assistant to the CFO received a Slack message from “her boss” requesting an urgent transfer.
Everything looked legit — except the CFO never sent it.
DRP monitoring flagged a spoofed domain and a fake email account mimicking the executive’s internal address.
The team blocked the sender and escalated the incident.
Want to learn more about executive impersonations? Check out this article.
6. Social Engineering via Doxxing
An energy company’s CEO started receiving harassing emails that referenced private travel plans and personal data.
DRP monitoring showed that the executive’s information had been posted on a dark web forum — likely pulled from a mix of public records and old breaches.
The security team tightened online exposure controls and worked with authorities.
7. Scam Promotions on Social Media
A cosmetics brand saw its followers tagging the company in giveaways they weren’t actually running.
DRP flagged multiple fake Instagram accounts offering “free makeup kits” in exchange for credit card details.
The campaign was part of a broader scam targeting beauty fans.
Accounts were reported, and new alerts were set up to catch similar activity.
8. Data Leak from a Vendor
A healthcare provider discovered PDF files containing sensitive internal records floating on a pastebin site.
The files had come from a vendor’s misconfigured cloud bucket.
DRP detected the upload shortly after it went public, allowing the company to respond before regulators — or the media — found it first.
These examples aren’t rare.
They’re the kind of threats organizations deal with every day — often without realizing it.
DRP gives you the visibility and context to stop them early, before they turn into reputation damage, compliance issues, or financial loss.
What to Look for in a DRP Platform
When evaluating a DRP platform, look for solutions that provide:
1. Comprehensive Digital Footprint Mapping
Ensure the platform can identify all your external-facing assets — domains, subdomains, cloud services, mobile apps, and third-party connections. This visibility is crucial for understanding your organization’s exposure to digital threats.
2. Broad Monitoring Coverage
A robust DRP solution should monitor across the surface web, deep and dark web, social media platforms, mobile app stores, and cloud infrastructure. This wide coverage helps detect threats like brand impersonation, data leaks, and phishing campaigns wherever they may arise.
3. High Accuracy and Relevance
Look for platforms that prioritize signal over noise, providing context-rich insights with minimal false positives. This ensures your team focuses on genuine threats, enhancing efficiency and response times.
4. Risk-Driven Prioritization
A valuable feature is a dynamic risk scoring system that assesses and categorizes threats based on severity and potential impact. This approach aids in prioritizing responses and allocating resources effectively.
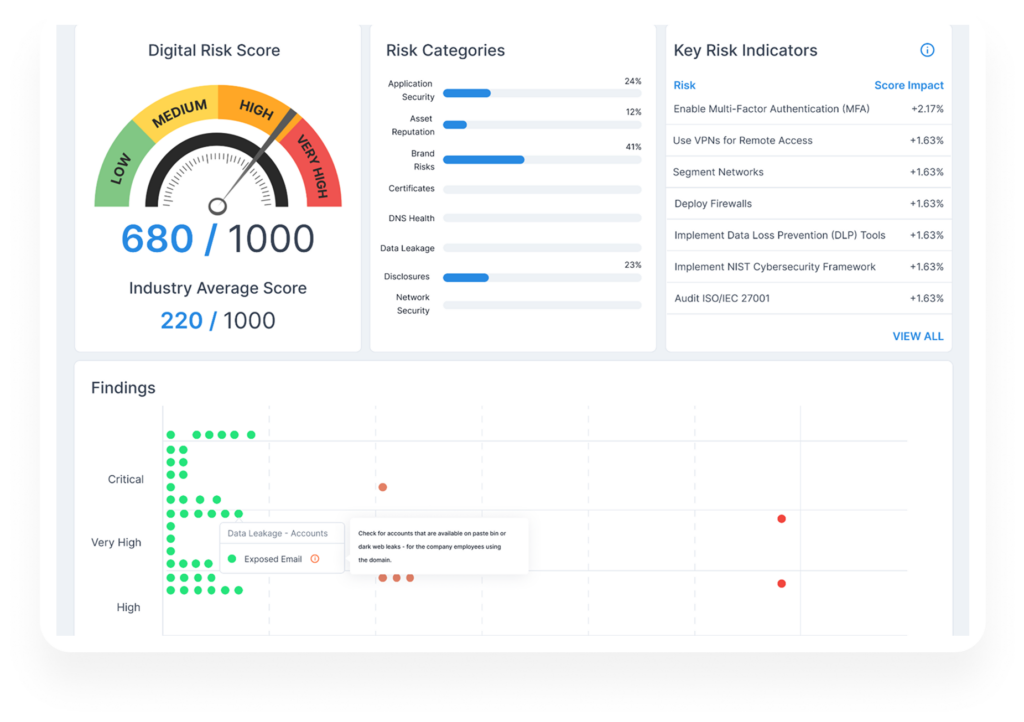
5. Integrated Takedown and Remediation Support
The ability to swiftly act on detected threats is vital. Platforms should offer integrated workflows for initiating takedowns of phishing sites, fake social media accounts, and other malicious content, streamlining the remediation process.
6. User-Friendly Dashboards and Reporting Tools
An intuitive interface with clear dashboards and reporting capabilities allows for easy visualization of your digital risk posture, aiding in decision-making and communication with stakeholders.
7. Fully Integrated Capabilities
Everything should work together — domain monitoring, social media impersonation alerts, leaked credential detection, dark web surveillance, takedown workflows, and more. A single platform that ties it all together saves time and reduces complexity.
8. Fast, Simplified Onboarding
You shouldn’t have to wait months to get started. A great platform is up and running in weeks — not quarters — with guided setup and streamlined provisioning for security, legal, risk, and marketing teams alike.

9. Built for Team Collaboration
It’s not just a tool for cybersecurity. DRP needs to work for brand protection teams, legal departments, and risk managers, too. Look for an intuitive, user-friendly interface that helps everyone get value — without training manuals or IT bottlenecks.
Guess what?
Styx Intelligene can offer you all these and more.
Connect with our team to see how DRP can help you protect your brand, people, and data before the next attack begins.