Risk, Compliance, and Legal Teams
Businesses can experience severe fines for not meeting regulatory standards. Ensure adherence to security mandates by protecting your customer’s data and monitoring your third parties.
Tighten Up Your Security and Prevent Liability
Even unintentional compliance breaches can come with significant costs. For instance, a data breach against a third party in your supply chain can make you liable, especially if it affects your customers’ or end-users’ data.
Stay ahead of advanced cyber threats and prevent regulatory breaches with our data leakage detection and vendor assessments.

Data Leakage Detection

Poorly handled responses to data breach events perpetrated by malicious actors can result in hefty fines. Maintain comprehensive visibility into the surface, deep, and dark web to discover if your customers’ data has been mishandled. Our platform also checks for paste bins, code repositories, and forums. Always stay informed with the tools necessary to meet data storage regulatory guidelines.
Monitor Your Attack Surface
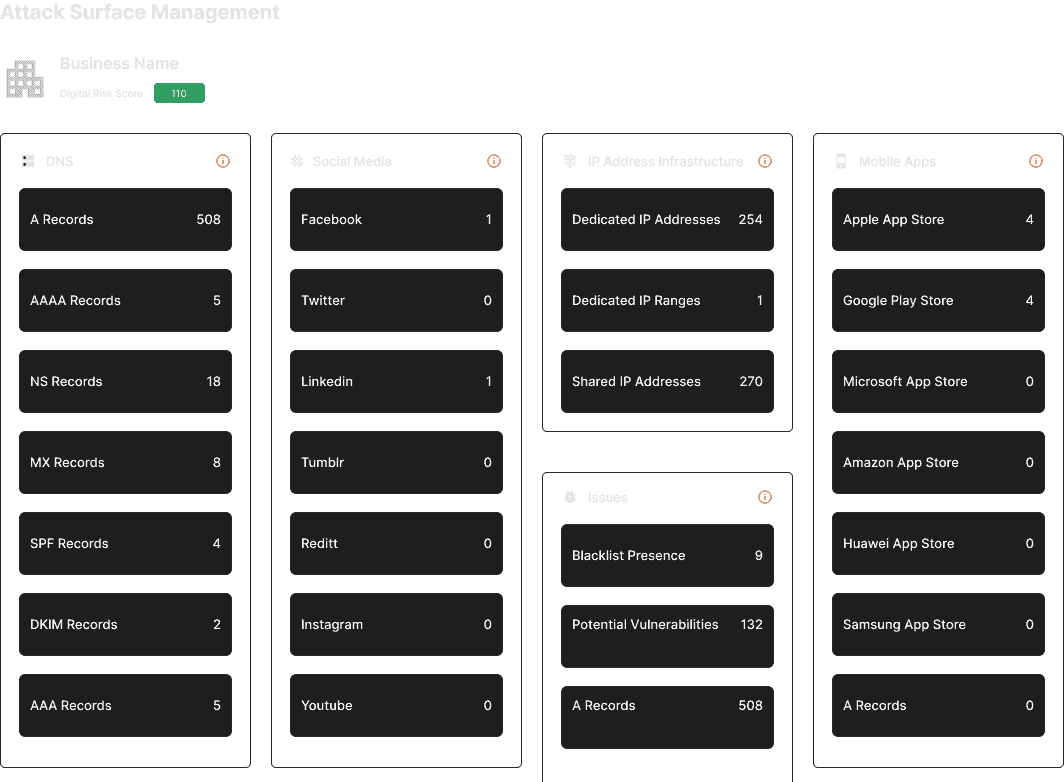
Our solution informs you of vulnerabilities in your attack surface, helping you understand and address the root causes of security issues. With our in-depth analysis of your internet-facing network and systems including CVEs and misconfigured assets, StyxView provides you with the insights needed to bolster your protective protocols and ensure compliance with industry regulations.


Assess Your Third-Party Vendors

Protect your business from third party security risks with StyxView’s vendor risk assessment solution. Our digital risk scorecard and questionnaire workflow helps to assess their digital security posture, generating a risk score to highlight potential red flags. Stay informed with our scalable risk matrix visualization and direct your focus on those critical third parties that pose the greatest threat to your information, business, and supply chain.
See StyxView in Action
Book a Demo
Explore Solutions for Risk, Legal, and Compliance Teams
Third Party Risk
Streamline due diligence on vendors with security scorecard and automated third-party questionnaires.
External Exposure Management
Real-time visibility into your organization’s digital exposure, helping you proactively manage new risks created by increasing digital connectedness.
External Data Leakage Detection
Monitor the surface, deep, and dark web for compromised credentials, exposure of sensitive documents, code repositories, cloud storage, and other data leaks.





