An AI-Powered, Unified Platform to Protect Your Brand From Cyber Threats
Get full visibility into digital risks, from brand impersonation to data leaks on the dark web.
Detect, analyze, and remediate threats, all in one unified platform designed for brand security.
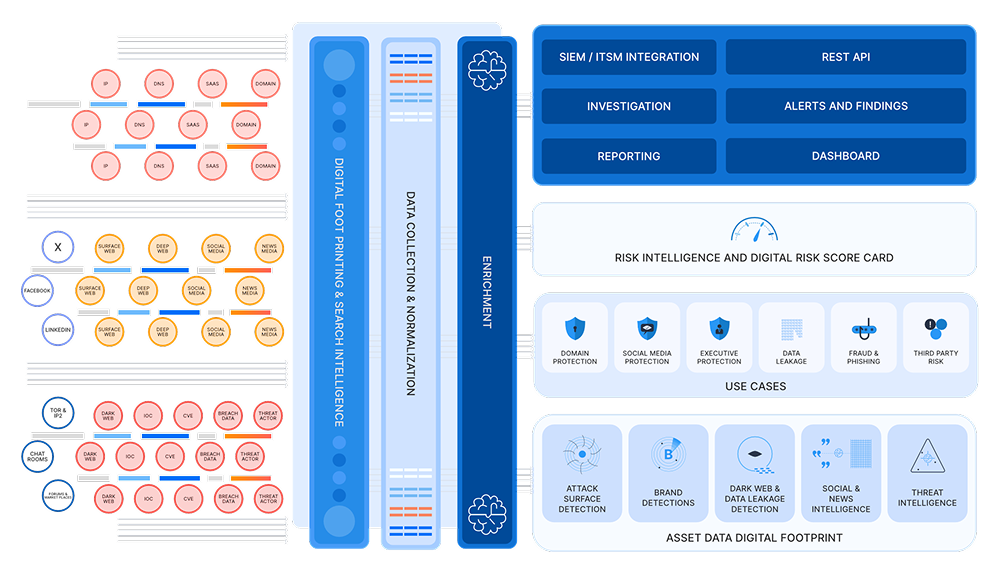
One Platform. Full Visibility.
Styx is a platform built to help companies monitor, detect, and act on external threats across domains, social media, executive presence, third parties, and even activity on the dark web.
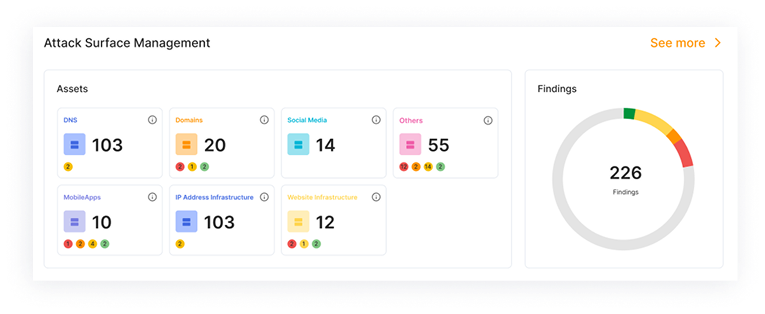
Know what’s out there. Track your full digital footprint — domains, social media, dark web, and third-party risks.
Spot threats early. AI-powered intelligence detects impersonation, phishing, data leaks, and security gaps in real-time.
Act fast. Styx Intelligence automates takedowns and enforces protection before threats harm your brand. Stay in control. Stay trusted.
Our Unique Advantage
Your brand is trust, reputation, and everything your customers believe in. We built Styx to protect that, combining deep intelligence, quick takedowns, and full visibility in one unified platform.
Built for brand protection, not just cybersecurity
Your brand is your most valuable asset. Styx Intelligence is purpose-built to protect reputation, trust, and customer confidence.

A fully consolidated platform
Everything you need for brand protection, including domain security, social media monitoring, dark web intelligence, takedowns, and more, built to work seamlessly in one place.
Brand Threat Detection & Integrated Takedown
Spot impersonation, phishing, and fake websites early, then shut them down fast with built-in takedown workflows for quick response.

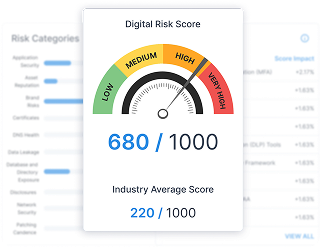
Risk-driven approach for smarter decisions
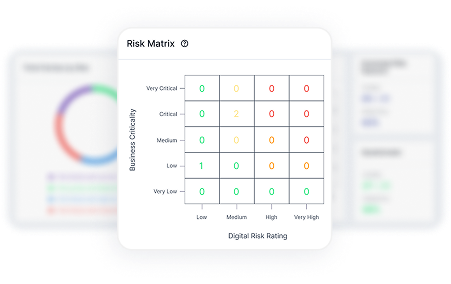
Go beyond alerts. Our digital risk score (DRS) helps you prioritize the most critical threats impacting your brand’s reputation and business.
Designed for seamless adoption across teams
A user-friendly, intuitive interface ensures seamless adoption across security, risk, legal, and brand teams — no steep learning curve required.
Connected and context-driven data
Styx’s proprietary data collection across the surface, deep, and dark web, including social media, provides actionable intelligence, not just raw alerts.
Faster, simplified onboarding
Get up and running in two weeks or less with streamlined provisioning and intuitive workflows for security, legal, marketing, and risk teams.

Social listening meets brand protection
The only platform that combines social media intelligence with brand security, so you can detect reputation risks before they escalate.
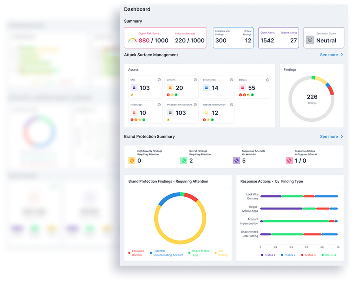
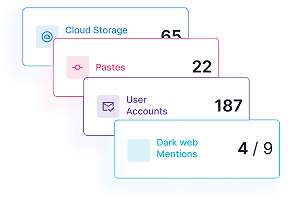
Single-pane-of-glass visibility
No more fragmented data. Our single-pane-of-glass dashboard gives you a clear, unified view of external threats and brand risks.

Styx Intelligence Use cases
- Domain Monitoring
- Social Media impersonation Monitoring
- Social Media Intelligence
- Sentiment Monitoring
- Rogue Apps Monitoring
- Job Scams Monitoring
- Automated Workflow for Takedowns
- Brand trademark Infringement
- Detection of non-authorized corporate assets — website and social media assets
- Impersonation Detection
- Personal Information Exposure Monitoring
- Online Presence Monitoring
- Digital footprint monitoring
- Social Media Impersonation
- Monitor of dark web for mentions of executives
- Real-time alerting and takedown of social media impersonation
- Phishing Website and Domain Takedown
- Social Media impersonation
- Evil Twin Website
- Malware
- Rogue Mobile Apps
- Trademark Infringements
- Marketplace Posting
- Data Leakage
- Advanced Request
- Brand Sentiment Analysis
- Social Media impersonation and phishing scams with integrated takedown capabilities
- Social Media Mentions Monitoring
- Fake News Misinformation
- Workforce’s social media activity to ensure alignment with brand values
- Real-time alerting of social media account takeover and impersonations
- Digital risk score to assess vendor’s overall posture
- Use risk-based matrix to visually compare and prioritize your most at-risk vendors
- Track vendor’s negative sentiment that could impact your brand by association
- Get notified about your third-parties’ data breaches or mentions on the dark web
- Automated security questionnaires to evaluate current practices and protocols
- Monitor surface, deep, and dark web for compromised credentials
- Dark Web Monitoring (Forums and Marketplaces)
- Real-time alerting of active data breaches
- Monitoring for exposed cloud storage
- Detection of leaked sensitive code
- Detection of exposed technical information
- Credit card monitoring
- Monitor cyber threats in real time
- Vulnerability intelligence = Identify and Prioritize Vulnerabilities
- Detect and Analyze data breaches
- Threat actor monitoring
- Understand the impact of global incidents
- Indicators of compromise
- Inventory of internet-facing assets
- Asset misconfiguration identifications
- Monitor email-related DNS records, IP addresses infrastructure and reputation, website infrastructure, and domains
- Scan external facing assets on demand
- Guidance on best practices for managing vulnerable assets and defending against active threats
- Real-time Alerting on misconfigurations
- Digital risk score
- Inventory of cloud application
- Detection of shadow IT
All solutions
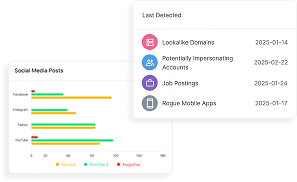
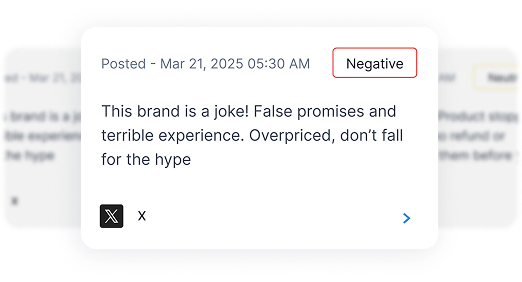
Social Media & News Monitoring
Monitor brand mentions, sentiment, and misinformation across social platforms and news sources.
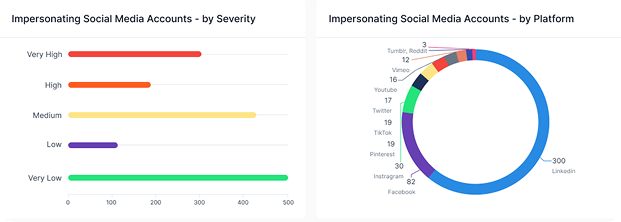
Brand Protection
Detect and take down fake websites, phishing domains, and impersonation scams before they damage your reputation and customer trust.
Takedown Service
Quickly take down phishing sites, fake accounts, fraudulent ads, and leaked corporate assets before they cause harm.
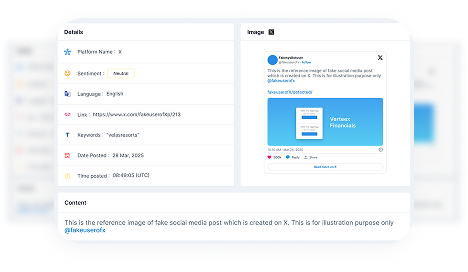
Executive Protection
Secure your leadership from impersonation, doxxing, and credential leaks with continuous monitoring and real-time threat detection.
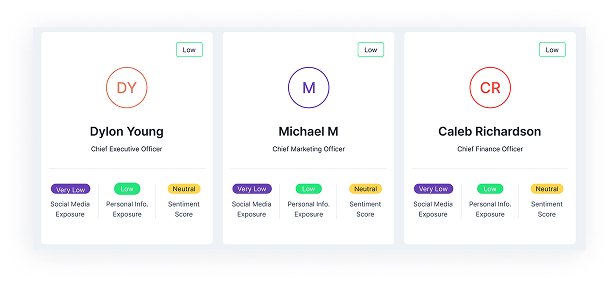
Third-Party Risk Management
Assess and monitor vendor security risks, compliance gaps, and data breaches to protect your brand from supply chain threats.
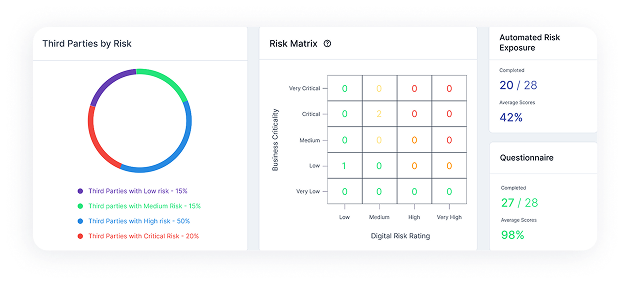
Threat Intelligence
Track emerging cyber threats, monitor hacker forums, and analyze dark web activity to detect vulnerabilities, data breaches, and malicious actors before they target your brand.
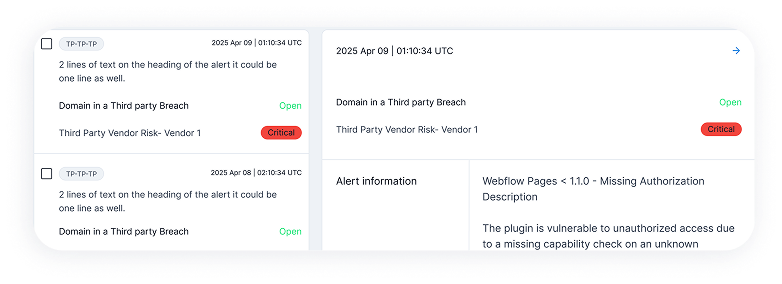
Digital Risk Score (DRS)
Quantify and prioritize brand threats with a dynamic risk score that helps you focus on the most critical vulnerabilities impacting your reputation and security.
External Attack Surface Management
Gain full visibility into your digital footprint, identify vulnerabilities, and secure misconfigured or exposed assets before hackers exploit them.