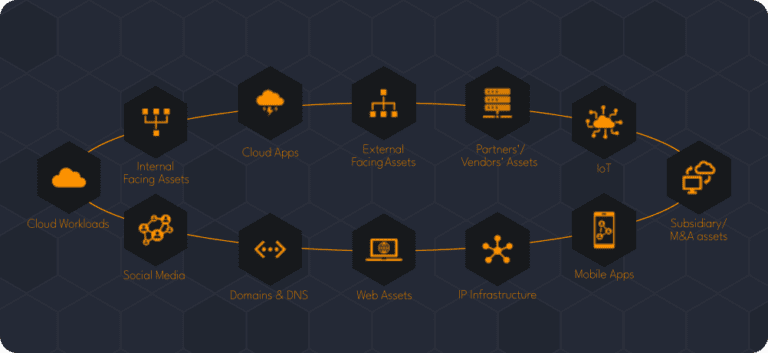
What Is Digital Risk?
Organizations have been undergoing a journey toward digital transformations and the dependence on digital product and services has grown exponentially through the pandemic. The adoption of digital products and services has led to an expansion of digital assets and data beyond our traditional boundaries with the adoption of cloud computing, Internet of Things, machine learning, and social media. However, while digital transformations are creating beneficial opportunities for organizations, they have also introduced a new dimension to the traditional view of risk. Furthermore, the resulting increased connectedness with supply chain partners and vendors have contributed to this exposure, especially with the lack of visibility into risk vectors. The impact of lacking the resources to manage digital risk is significant where incidents can affect organizations’ bottom line, client retention, and brand reputation.
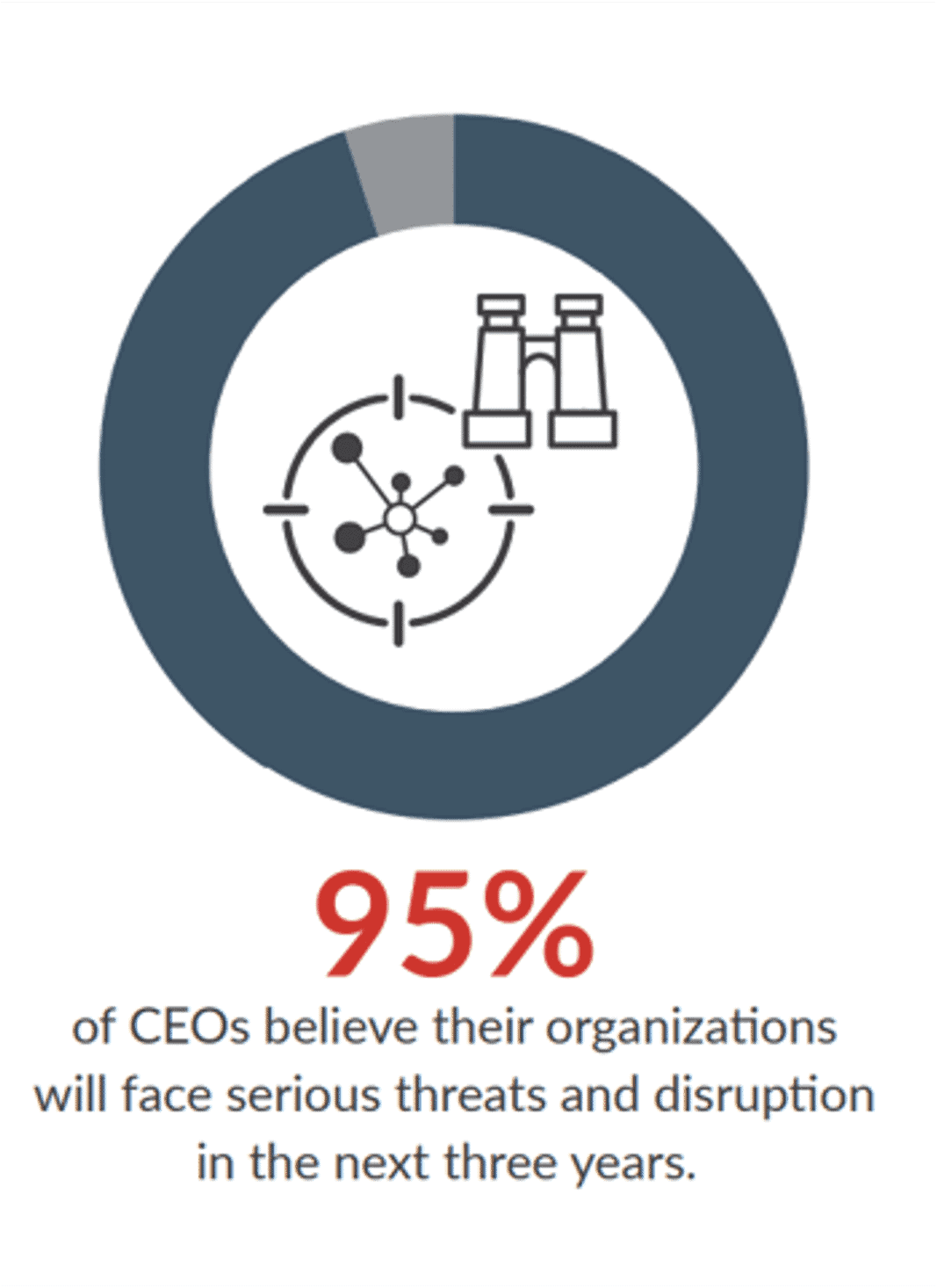
Sources: RSA & Deloitte

Increasing Attack Surface Introduces More Risk
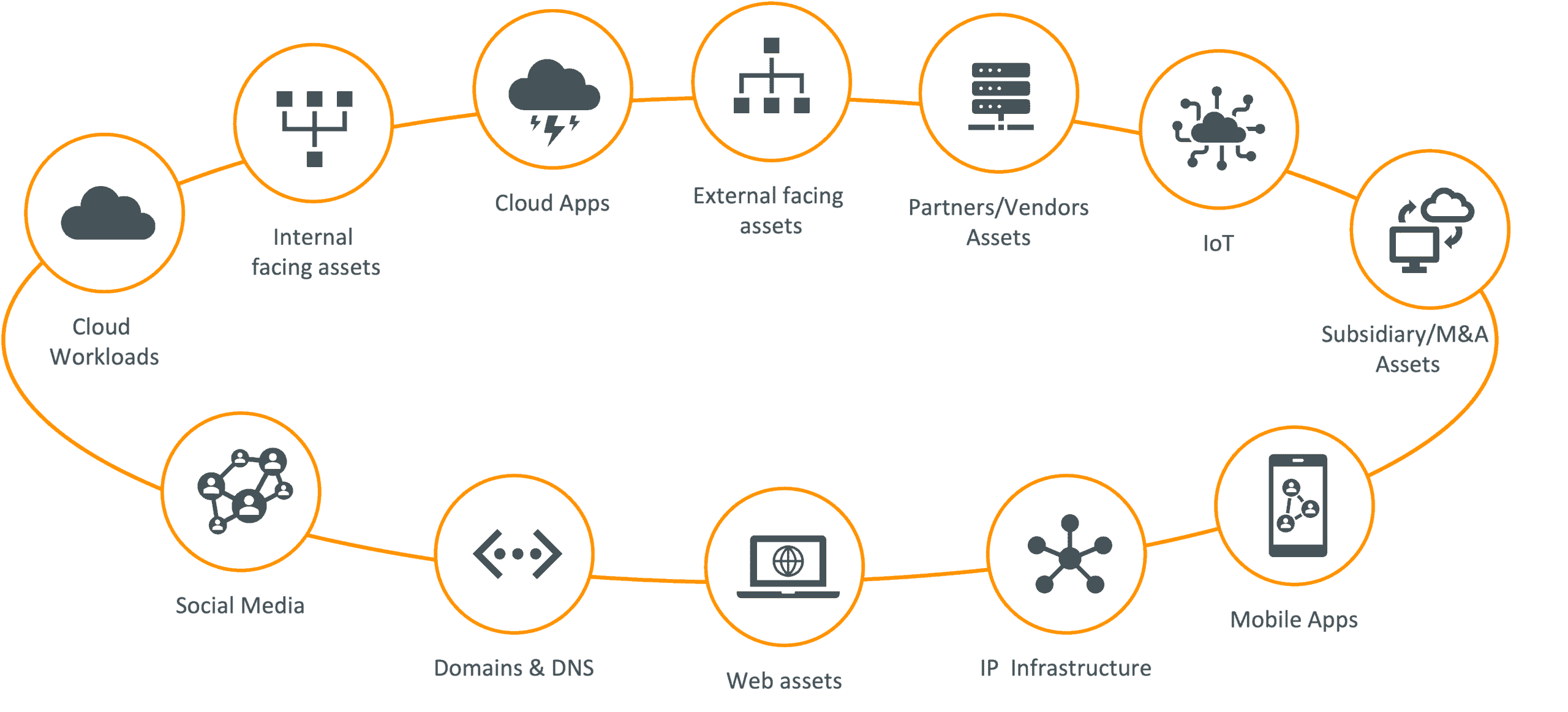
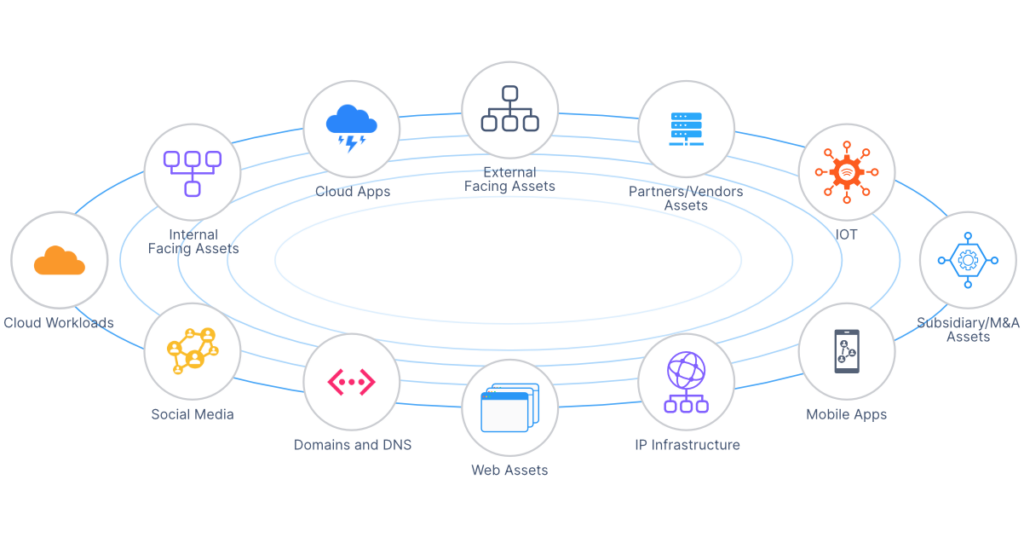
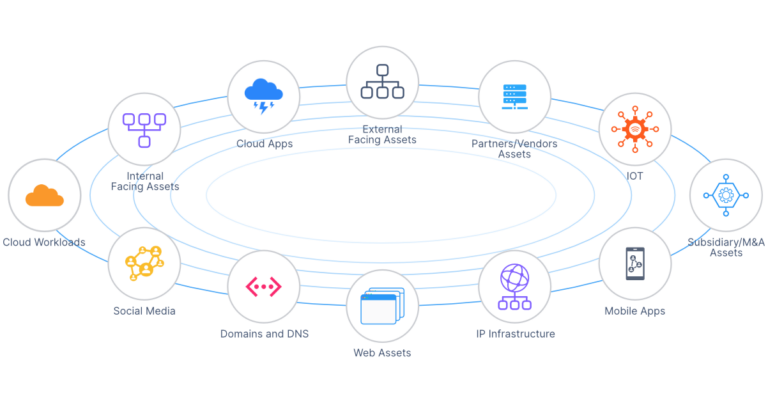
Before getting into the significance of this challenge, we must understand what the attack surface is in the first place. This is the set of points in an organization that cyber criminals use as entry into the network for exploitation, such as stealing data or uploading ransomware. This includes IP infrastructure, cloud applications, social media accounts, and web assets owned by partners and vendors. Unsurprisingly, this exemplifies how digital transformations introduce more risk in the form of increased attack surface exposure. With digitally driven business models, the traditional attack surface has completely changed and understanding this risk is crucial when making sure there aren’t any vulnerable network gaps.
How Are Breaches Happening?
When you think about what threats to mitigate, you have to understand how breaches occur. Like many people fulfilling a complex challenge, attackers will take the path of least resistance. by looking for weakness in an organization’s external footprint. Impersonations are occurring with more frequency – this includes domain spoofing and social media impersonation to launch phishing scams against unsuspecting employees and clients. Additionally, compromised account credentials pose another severe threat that gives direct access to threat actors with hackers exploiting employee accounts and passwords found in other data breaches.
Assessing Risk Related to Digitization
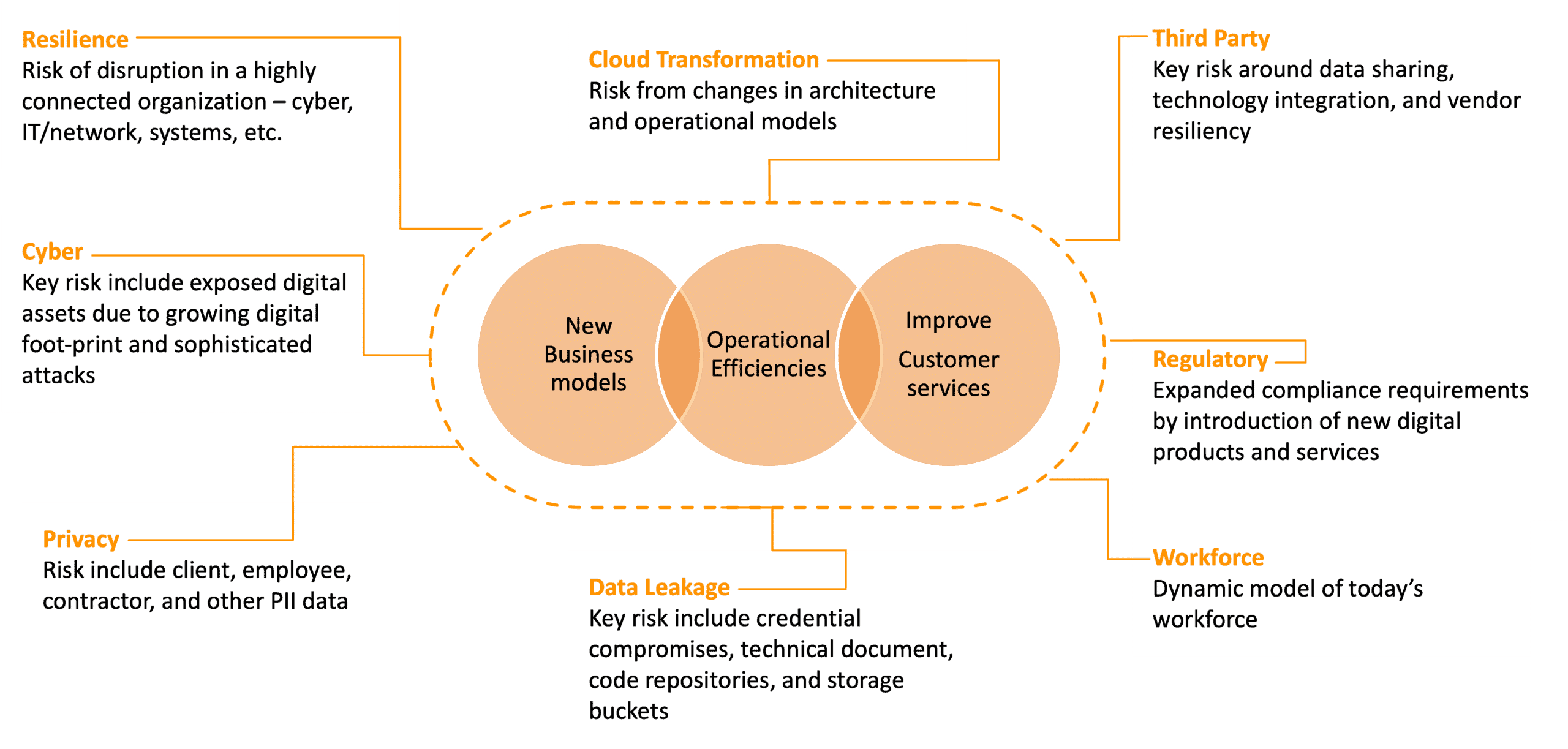
How do you get started with approaching digital risk? The first step is to identify your organization’s crown jewels; such as core competencies, business processes, systems, and data; that might have all been affected by digital transformation. This will allow you to focus on tightening up protocols and practices on your most critical business assets that drive day-to-day operations. The next step is to know the boundaries and interconnection between each of the items considered previously to turn your attention to the most imperative weak points. This can include the interconnection of hosted systems, how data is shared with vendors in your supply chain, or the bridge between employees and customers. This also allows you to understand where the service provider’s responsibility starts and ends, especially with third parties and cloud applications. One of the main struggles with this process is the lack of visibility into these risks. This is especially apparent as digital architecture becomes more complex and sources of threats are not visible with outdated security tools.
Managing Digital Risk
Now that you have a better idea of how to assess risk, how do you take action? Discovering vulnerabilities and threats can be achieved with digital footprinting tools and raising awareness through workshops for your employees and executives. By understanding the role different parts play for your digital assets and business processes, you can then analyze and prioritize the risks that need to be taken care of. From there, it is important to create a roadmap to plan out what changes have to be made, an action plan for potential incidents, and the steps for implementation. After executing your strategy, you should continuously monitor your risk vectors so that you can detect threats as they come up and deal with them armed with your playbook. This can be an intensive process, but you can achieve the best return on investment by getting involvement from your employees and executives who are often the first line of defence. Greater awareness of mitigating threats from your people allows for more efficient and effective risk management.
Digital Risk Protection with StyxView
Safeguard your organization from digital threats and manage risks effectively with StyxView’s comprehensive and unified approach. Our platform offers complete visibility into the surface, deep, and dark web; enabling you to identify and prioritize threats quickly. Monitor your brand’s online reputation with our social listening capabilities. Take prompt action against active threats, such as impersonators and data leaks, with coordinated incident remediation guidance. StyxView empowers your organization to thrive in today’s high-risk digital world by providing integrated visibility and actionable insights.