Municipalities and Political Leaders Services
Protect Municipalities and Leaders from Digital Threats

Prevent impersonations, misinformation, and attacks that target public institutions, political leaders, and citizens. Detect, monitor, and take down threats before they damage trust, disrupt services, or put people at risk.

Trusted by leading companies worldwide.




External Attack Surface Management

- Map and monitor the digital footprint of public services — from utilities and transportation to emergency services and citywide systems.
- Detect exposed assets across departments, city halls, libraries, and remote offices, reducing entry points for attackers.
- Manage risks tied to legacy systems, forgotten subdomains, and cloud misconfigurations.
- Strengthen visibility and reduce digital blind spots by Identifying vulnerabilities in personal or public-facing infrastructure connected to political leaders.
Personal and sensitive data protection
- Monitor for exposed personal data across the surface, deep, and dark web — including credentials, financial info, and identification details tied to government systems or political leaders.
- Identify leaked records like tax data, voter rolls, or public safety information that could put municipalities or citizens at risk.
- Protect political leaders from exposed credentials, confidential financial information, identification numbers, physical addresses, and personal history.
- Get alerts when political leaders are involved in data breaches, with full visibility into what was exposed and how.
- Receive practical guidance to reduce exposure and protect public trust — whether you manage citizen data or hold public office.
"As a government and public services entity, trust is everything. Styx helps us safeguard our digital footprint, ensuring that brand reputation is never at risk. Their expertise in managing third-party risks adds another layer of protection that we depend on."
Sumon Acharjee
Chief Information Officer, City of Markham
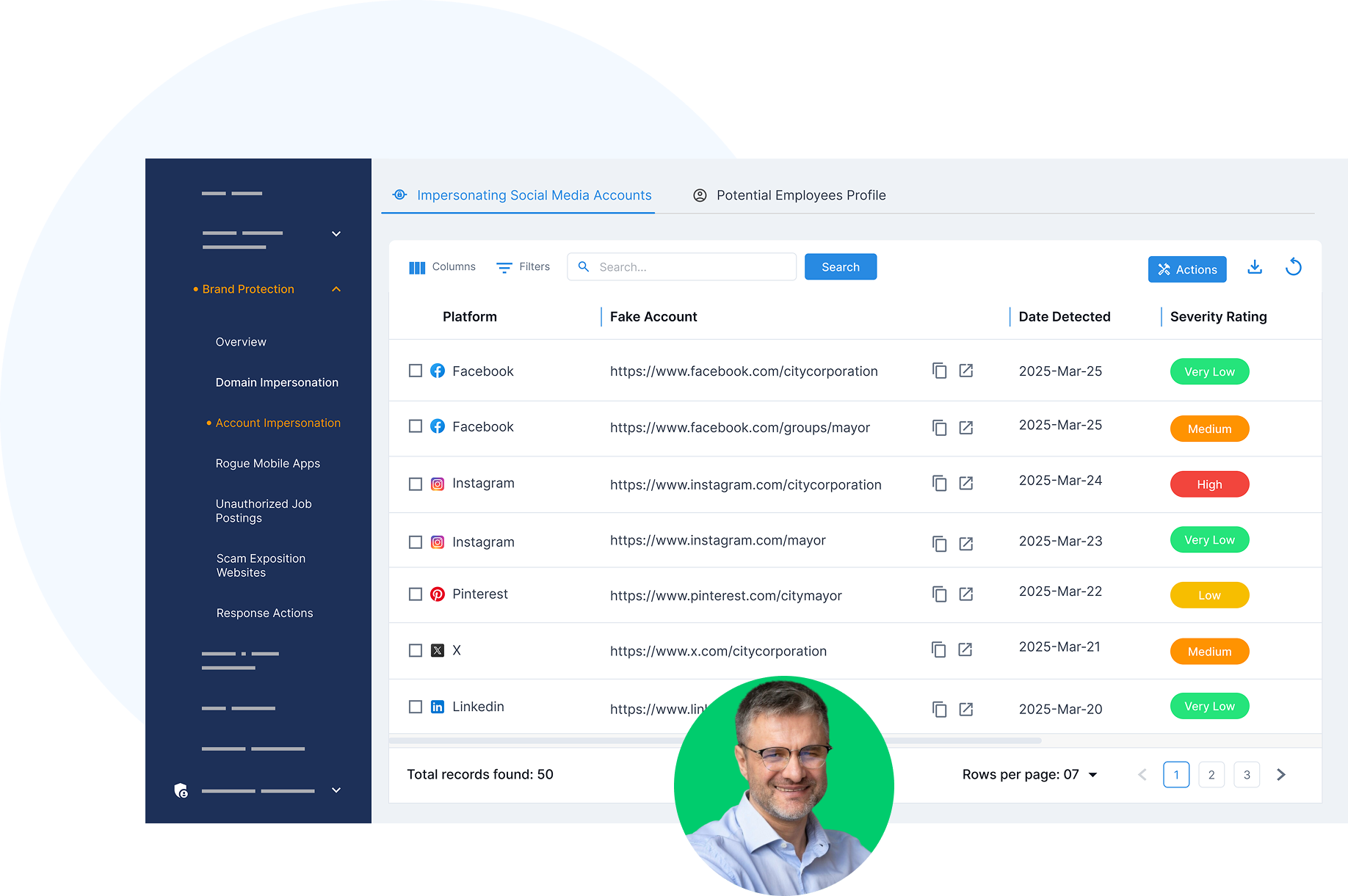
Monitor and Take Down Impersonations and Digital Threats

- Detect fake social media accounts and impersonating profiles targeting political leaders, city departments, or public services.
- Monitor for sentiment shifts, coordinated smear campaigns, and hate speech that could escalate into real-world risks or reputational damage.
- Track the spread of fake news and disinformation that targets elections, government initiatives, or individual leaders.
- Get real-time alerts on account takeovers and unauthorized use of official branding or imagery, with immediate action options within the platform.
- Use integrated takedown workflows to quickly shut down malicious content, impersonations, and digital threats — before they gain traction.
Cyber Threat Visibility for Municipalities and Political Leaders
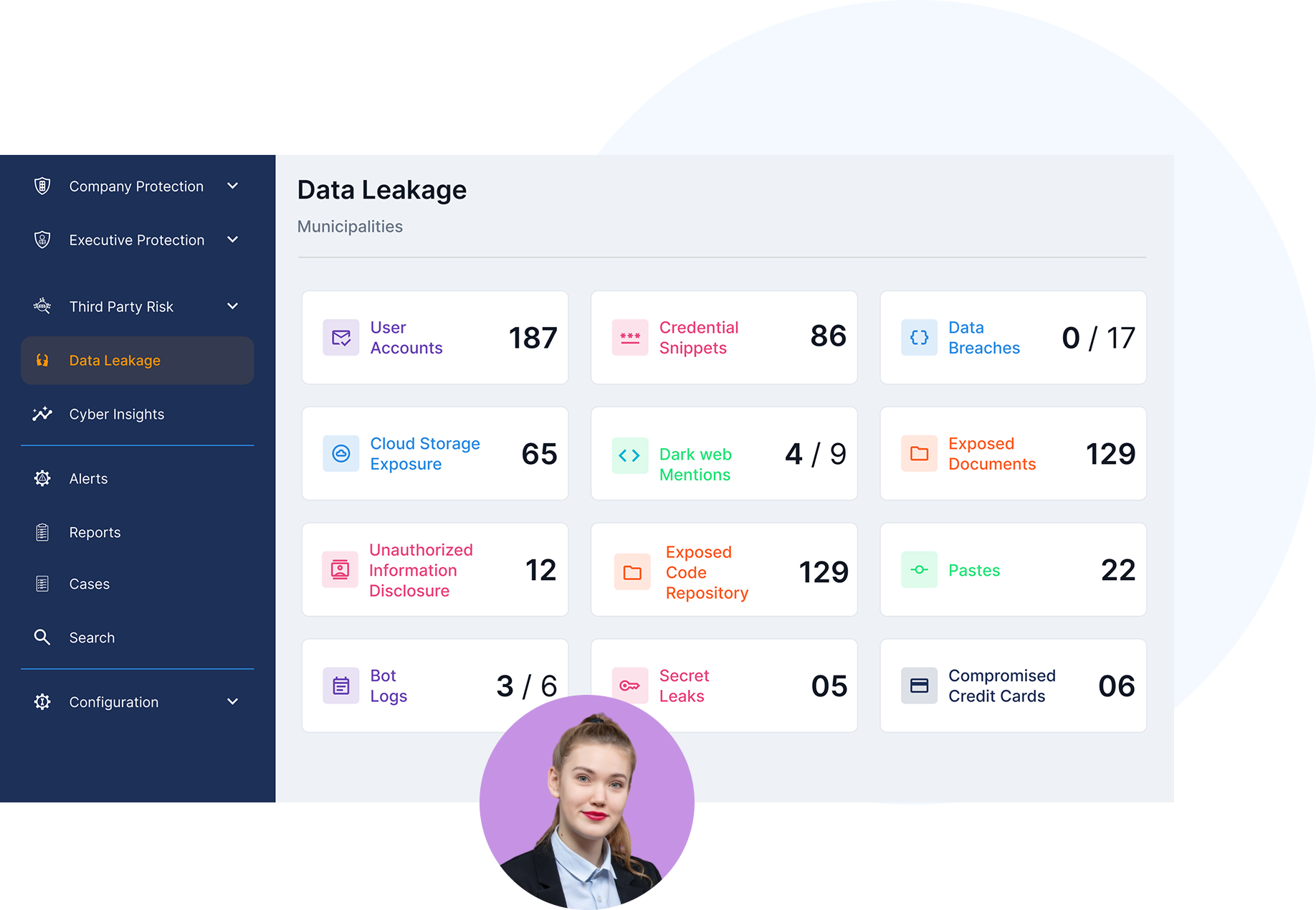
- Track ransomware groups and hacktivist activity targeting local governments, public infrastructure, and political figures.
- Monitor deep web, dark web, and forums for early chatter about planned attacks, data leaks, or system vulnerabilities.
- Get real-time alerts and rapid response tools when sensitive data or disinformation begins to circulate.
- Receive detailed breach insights, including which leaders or systems were affected, what data was exposed, and what it means for your risk.
- Get strategic recommendations to strengthen your cyber defences and reduce future exposure.

Take Control of Your Brand’s Reputation
Ready to see how Styx Intelligence can help you protect your brand online?

Third-Party Protection That Matches Public Sector Risk

- Gain full visibility into vendor and partner ecosystems, including cloud providers, software vendors, and IT service firms.
- Identify risky third parties by analyzing breach history, threat exposure, and ongoing security practices.
- Assess and prioritize external threats before they impact public services, citizen data, or leadership communications.
- Monitor for third-party data leaks, misconfigurations, or impersonation threats connected to your supply chain.
- Strengthen procurement and compliance with continuous security insights that support better vendor oversight and contract decisions.





