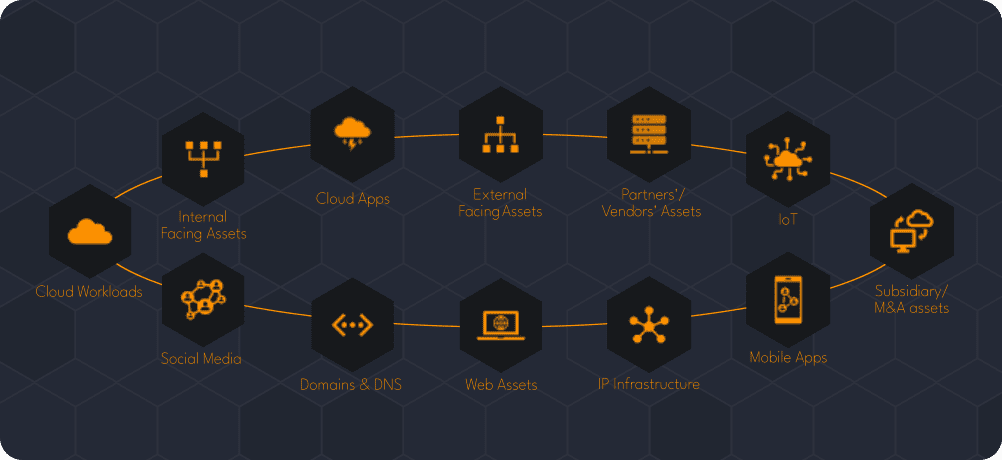
What Is EASM?
External Attack Surface Management (EASM) is a cybersecurity strategy that aims to minimize an organization’s exposure to cyber threats. This is achieved by identifying, assessing, and mitigating potential vulnerabilities in their systems, applications, and networks. Attack surface management aims to reduce the number of entry points available to attackers, making it more difficult for them to successfully penetrate defenses.
Why Is EASM Important?
In today’s interconnected world, organizations rely on a multitude of external systems and assets to carry out their day-to-day operations. While these systems provide substantial benefits, they also pose a significant security risk. By their very nature, external systems may be beyond an organization’s direct control, making it more challenging to ensure that they are secure.
Cyber threats are becoming increasingly sophisticated and are taking advantage of vulnerabilities in external systems. For instance, attackers can use techniques such as phishing scams and cross-site scripting to gain access to sensitive data. Additionally, external systems can be vulnerable to malware, ransomware, and other forms of cyberattacks that can lead to a data breach or other security incidents.
Organizations are considering increasing use of cloud-based services. The attack surface for cloud-based services can be larger than for on-premise systems, and organizations must be prepared to manage the security risks posed by these services. This is especially true as many move critical applications and data to the cloud.
In light of these security risks, organizations must have a robust external attack surface management strategy in place to minimize the risk of a breach. This strategy should include both proactive measures to prevent attacks and reactive measures to detect and respond to incidents when they occur.
How Does EASM Work?
Attack surface management starts with a comprehensive assessment of an organization’s infrastructure. This includes identifying all systems, applications, and networks that make up the organization’s environment, and determining the role each one plays in supporting their operations. This information is then used to create a comprehensive map of the organization’s attack surface, which provides visibility into the threat vectors that attackers could use to penetrate the organization’s defenses as well as visibility into potential shadow IT assets.
Once the attack surface has been mapped, the next step is to assess the security of each system, application, and network. This involves identifying potential vulnerabilities and evaluating the risk they pose to the organization. For example, an outdated software application may contain security weaknesses that could be exploited by attackers, while a weak password policy may make it easier for attackers to gain unauthorized access to sensitive information.
Once potential misconfiguration, vulnerabilities, or shadow IT assets have been identified, the security team must prioritize which ones to address first. This prioritization is based on numerous factors, including the criticality of the system, application, or network; the severity of the potential impact of a successful attack; and the likelihood of an attack. They must then develop and implement mitigation strategies to reduce the risk posed by each vulnerability. This may involve patching or upgrading software, implementing stronger authentication mechanisms, or configuring firewalls and other security technologies to block access from untrusted sources.
Attack surface management is a continuous process as the threat landscape is constantly evolving, and new vulnerabilities are being discovered. Organizations must therefore regularly assess their attack surface and update their mitigation strategies as needed. This requires a commitment to ongoing security awareness training and the adoption of best practices in security governance.
Another important aspect of attack surface management is the use of security tools and technologies. These tools can help organizations to automate many of the tasks involved in attack surface management, such as identifying potential vulnerabilities, assessing risk, and implementing mitigation strategies. They can also provide real-time monitoring and alerts, allowing organizations security teams to respond quickly to potential risks.
What Areas Does EASM Look At?
Styx’s EASM module provides the capability to identify insecure configurations across the below and more:
- Website Infrastructure:
- Insecure Headers
- Vulnerabilities
- Input pages
- Third-party services (SaaS, PaaS)
- Domains:
- WHOIS Data Validation
- DNSSEC
- DNS:
- PTR Record configuration
- Backup Mail servers and Nameservers
- Email Security Records
- IP Address Infrastructure:
- Inventory
- Insecure Ports
- TLS/SSL Certificates:
- Expired certificates
- Incorrectly issued certificates
- Self-signed certificates
- Weak encryption algorithms
- Incomplete certificate chains
- Social Media:
- Links
- Auto-generated profiles
- Mobile Apps:
- Publisher
- Versions
Secure your digital assets with StyxView’s attack surface management solution. Our platform offers full coverage of your attack surface to identify potential vulnerabilities. Our catalogue of digital assets serves as an inventory and allows you to monitor attack points. Our attacker-perspective approach helps you understand your exposure and root causes of security issues. This enables you to improve protocols and prevent future incidents. You are also able to get guidance on best practices for asset management and configuration. Simplify the burden of managing your public-facing assets with our risk-driven platform and safeguard your business against threats.