Protect Your Executives. Protect Your Brand.
Executives are prime targets for impersonation, fraud, and data leaks. Secure their digital presence to protect your company’s reputation and customer trust.
Executive Protection Solution by STYX
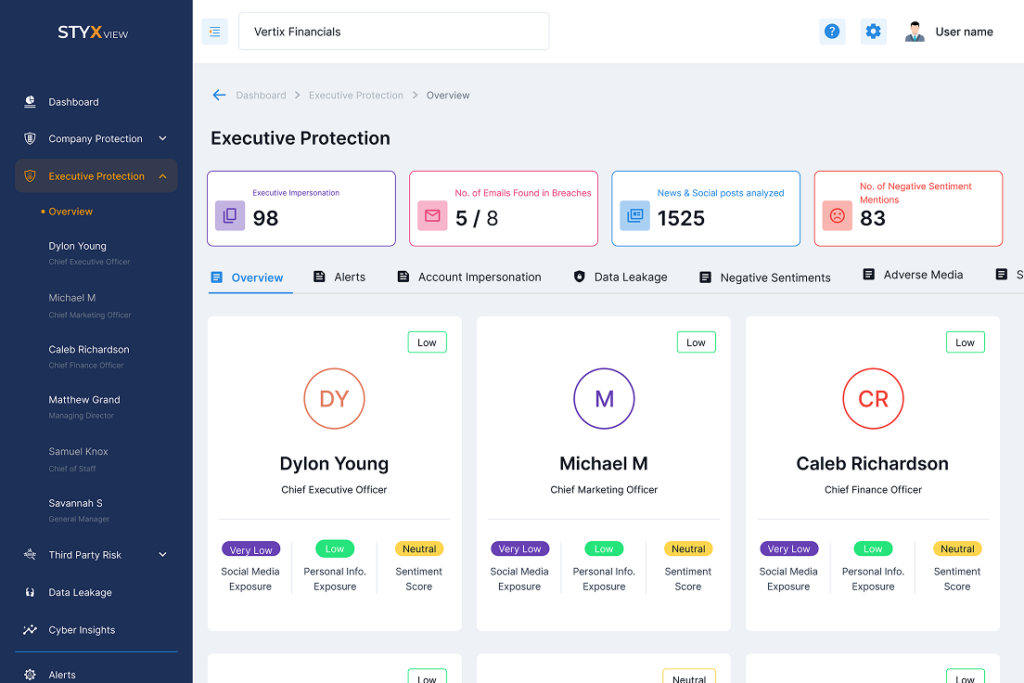
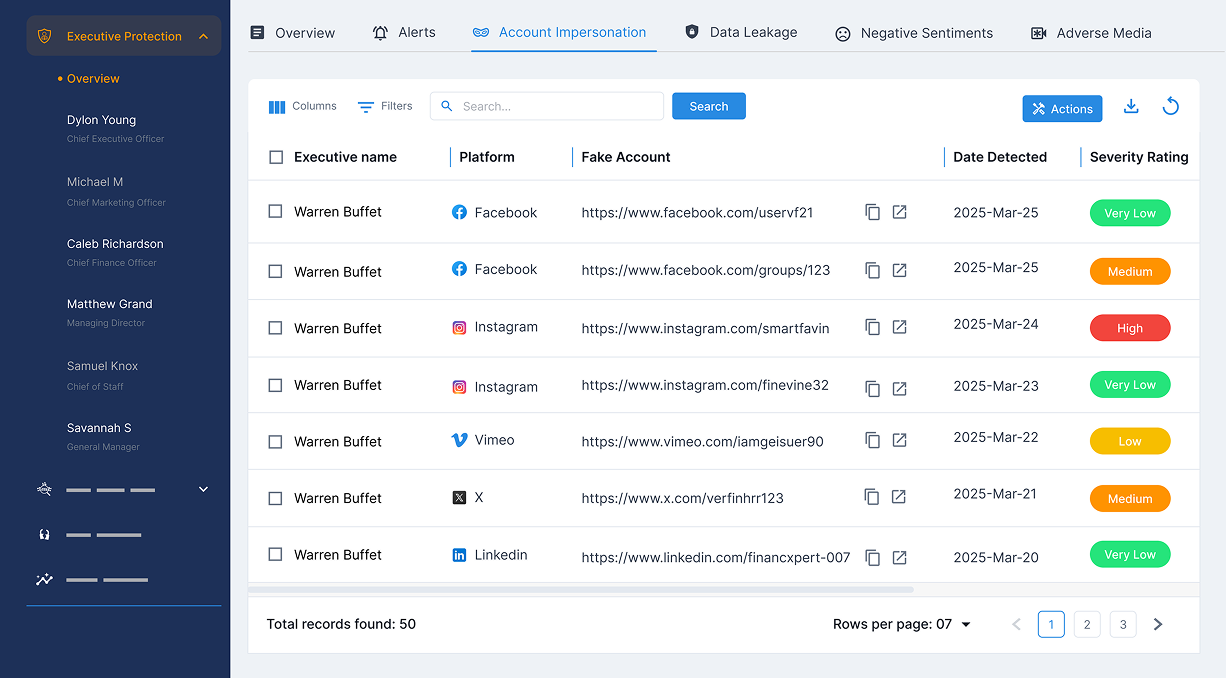
Executive Impersonation Detection
- Detect profiles impersonating executives and lookalike usernames, across social media and messaging platforms.
- Act on impersonation attempts as they go live, before they can mislead your customers, employees, or partners.
- Act on profile activity in the event of account takeover to prevent inappropriate posts.
Executive Impersonation Detection
Personal Information Exposure Monitoring

Personal Information Exposure Monitoring
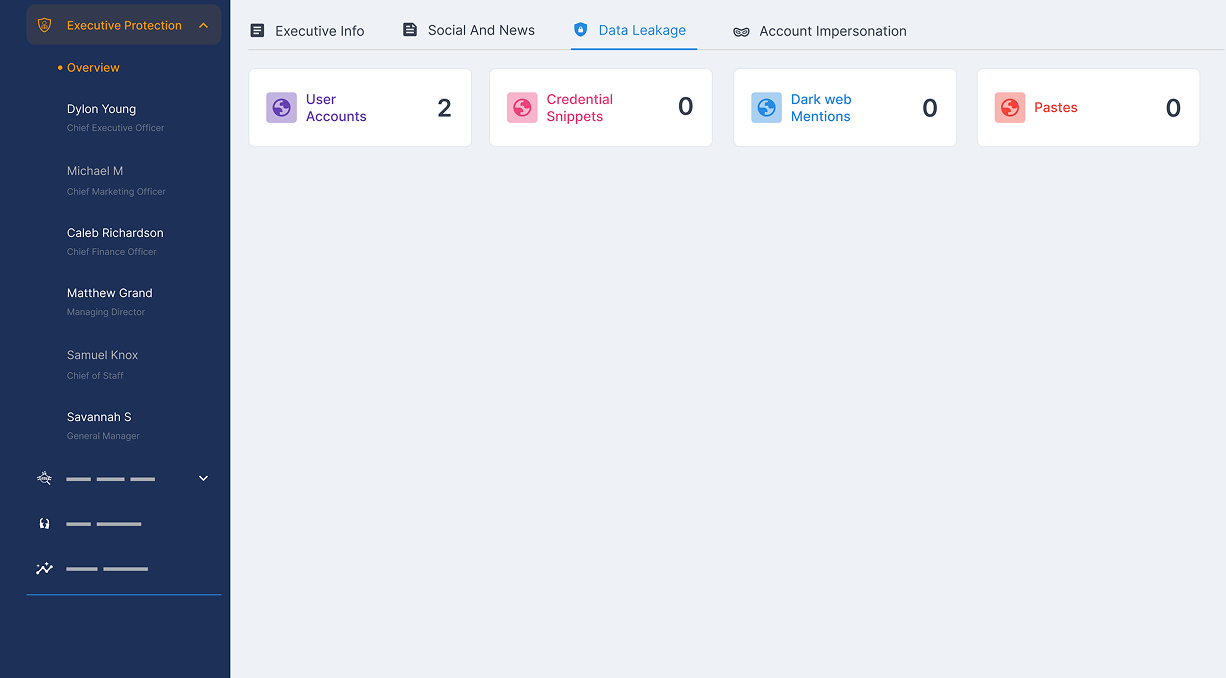
- Monitor the surface, deep, and dark web for leaked personal executive data.
- Detect exposed credentials, emails, addresses, ID numbers, financial information, and personal history.
- Get alerts on executive data breaches and understand the context around the exposure.
- Identify early signs of doxing attempts and protect executives from harassment or threats.
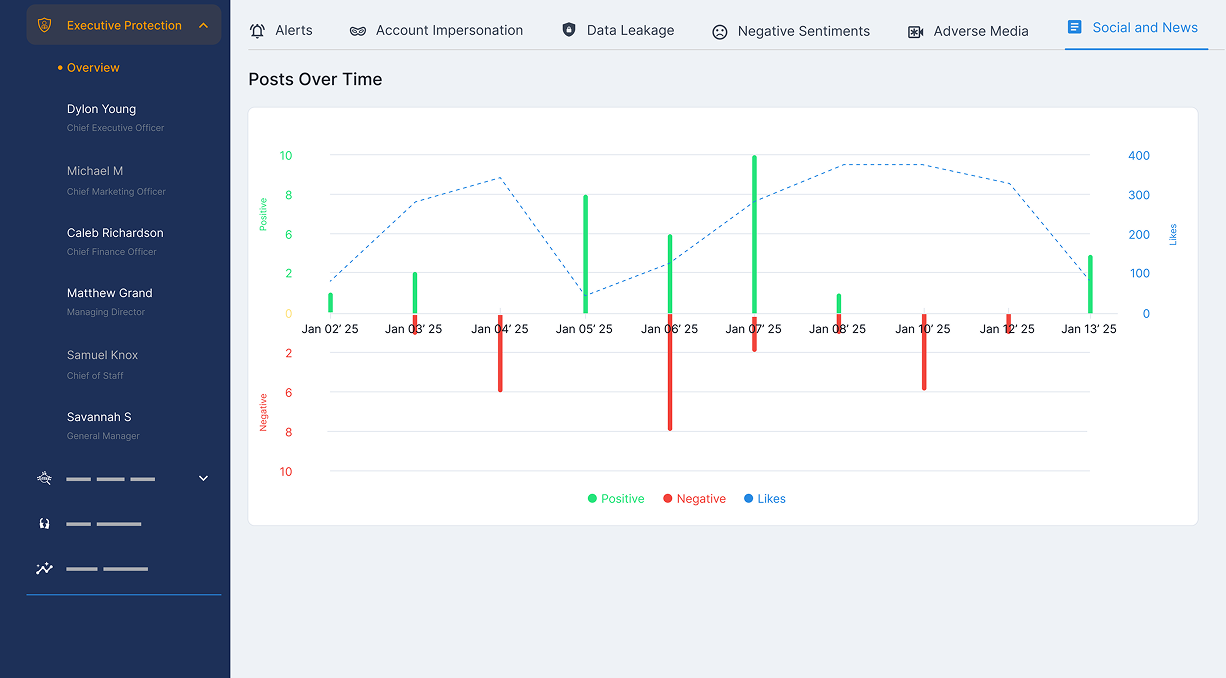
Online Presence Monitoring
- Monitor mentions of executives across social media, news, and forums.
- Identify sentiment trends, reputational risks, and unusual activity.
- Spot anomalies in social content or account behaviour that could signal a compromise.
- Measure online visibility with an exposure score that highlights how often your executives appear in public conversations.
Online Presence Monitoring
Dark Web Monitoring for Executive Threats
Dark Web Monitoring for Executive Threats
- Detect executive mentions in criminal forums and marketplaces.
- Uncover stolen credentials and personal data traded on the dark web.
- Receive alerts about targeting campaigns involving your leadership team.
- Track dark web exposure for high-profile individuals.
Real-Time Alerts & Automated Takedowns
- Get notified instantly when executives are being impersonated or targeted.
- Submit takedown requests for fake profiles, emails, or leaked data directly from the platform.
- Prioritize and act on high-risk alerts before they escalate.
- Monitor takedown resolution status and streamline cross-team response.
Real-Time Alerts & Automated Takedowns
Protect your leadership from cybercriminals
Don’t let cybercriminals exploit leadership for scams and impersonation
Executive Protection Capabilities
- Executive Impersonation Detection
- Personal Information Exposure Monitoring
- Online Presence Monitoring
- Dark Web Monitoring for Executive Threats
- Real-Time Alerts & Automated Takedowns
Learn More About How We Protect Brands
Explore the Latest on Digital Risk
FAQs on Executive Protection
We provide continuous monitoring across social media, hacker forums, and dark web marketplaces to detect executive impersonation, data leaks, and targeted attacks before they cause harm.
Yes! We identify and take down fake executive profiles across LinkedIn, Twitter, and other major platforms to prevent phishing scams, fraud, and misinformation.
We detect email spoofing and phishing attacks impersonating executives, alerting organizations before cybercriminals can deceive employees, partners, or customers.
We monitor leaked executive information such as home addresses, phone numbers, login credentials, and financial records, ensuring sensitive data doesn’t fall into the wrong hands.
Once a threat is identified, we provide real-time alerts and automated takedown workflows to shut down fake profiles, phishing pages, and leaked information quickly and efficiently.





