In this digital era, it is very common that the data you own may be exposed and there could be plethora of reasons for that. This scenario is part of what is called as Data Leakage. Today, I would like to discuss this in detail with specific focus around its impact on organizations.
Data leakage refers to the unauthorized or unintended exposure of sensitive information. It is a critical security concern for organizations of all sizes, as data breaches can result in significant financial losses, reputational damage, and legal liability. In this blog post, we will explore the causes of data leakage, the different types of data that are at risk, and the steps organizations can take to prevent and detect data breaches.
Causes of Data Leakage
Data leakage can occur in a number of ways, including through human error, technical malfunctions, and cyber-attacks. Some of the most common causes of data leakage include:
- Employee error: Employees may accidentally share sensitive information with unauthorized individuals, such as sending an email to the wrong recipient or storing sensitive information on an unsecured device.
- Malicious insiders: Malicious insiders, such as disgruntled employees or contractors, may intentionally steal or share sensitive information.
- Unsecured data storage: Data that is stored on unsecured systems or devices, such as unencrypted laptops or USB drives, is vulnerable to theft or loss.
- Unsecured networks: Data that is transmitted over unsecured networks, such as public Wi-Fi or unencrypted email, is vulnerable to interception by unauthorized individuals.
- Cyber attacks: Cyber attacks, such as phishing scams or malware infections, can compromise sensitive information and lead to data breaches.
Types of Data at Risk
There are many different types of data that are at risk of being leaked, including:
- Personal information: This includes information such as names, addresses, Social Security numbers, and financial information.
- Intellectual property: This includes trade secrets, proprietary information, and confidential business information.
- Health information: This includes medical records, insurance information, and health-related personal information.
- Financial information: This includes credit card numbers, bank account information, and investment records.
- Confidential business information: This includes business plans, customer lists, and confidential communications between employees.
Preventing Data Leakage
Organizations can take a number of steps to prevent data breaches and minimize the risk of data leakage, including:
- Implementing data security policies: Organizations should establish data security policies that define what data is considered sensitive, who has access to that data, and how that data should be stored, transmitted, and shared.
- Providing employee training: Organizations should educate employees on data security best practices and the consequences of data breaches. This includes training on how to properly store, transmit, and share sensitive information, as well as how to recognize and report potential security threats.
- Encrypting sensitive data: Encryption is a critical tool for protecting sensitive data, as it makes it unreadable to unauthorized individuals. Organizations should encrypt all sensitive data that is stored on systems and devices, as well as any data that is transmitted over networks.
- Securing data storage systems: Organizations should secure all systems and devices that store sensitive data, including laptops, servers, and cloud storage systems. This includes implementing firewalls, anti-malware software, and other security measures to prevent unauthorized access.
- Monitoring networks and systems: Organizations should monitor their networks and systems for signs of security threats, such as unauthorized access or suspicious network activity. This can include using intrusion detection systems, log management tools, and other security technologies to identify potential security breaches.
Detection and Response
Despite the best efforts of organizations to prevent data breaches, data leaks can still occur. It is therefore critical that organizations have plans in place for detecting and responding to data breaches.
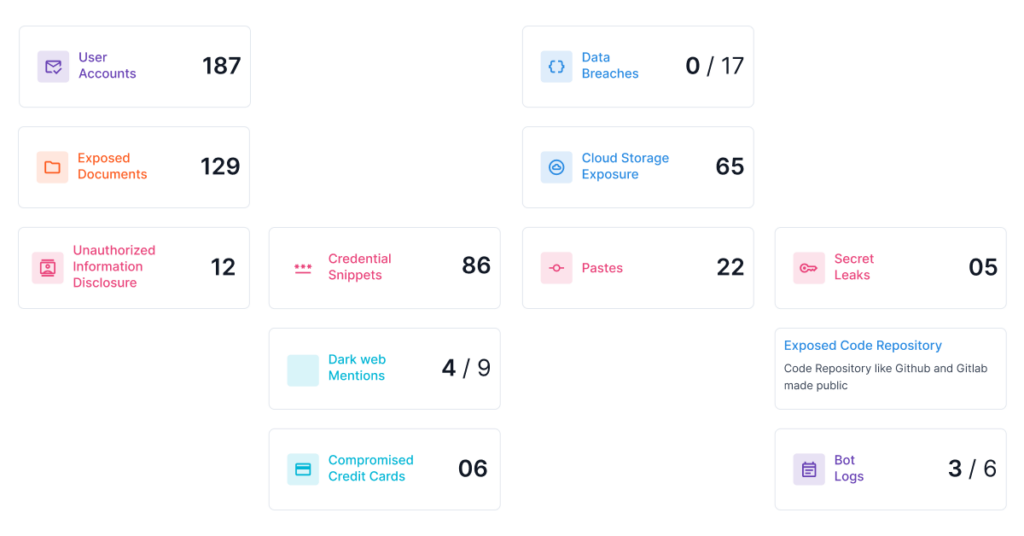
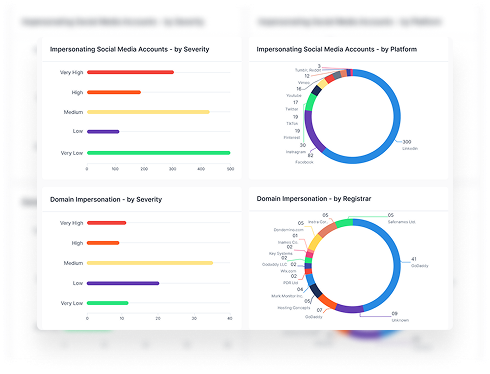
StyxView helps protect your confidential data by monitoring the surface, deep, and dark web for leaked credentials, documents, and code repositories. Be proactive and understand your security vulnerabilities to prevent future data breaches.