Keep Your Sensitive Information Safe
Gain real-time visibility into dark web threats and stop data exposure before it affects your business.
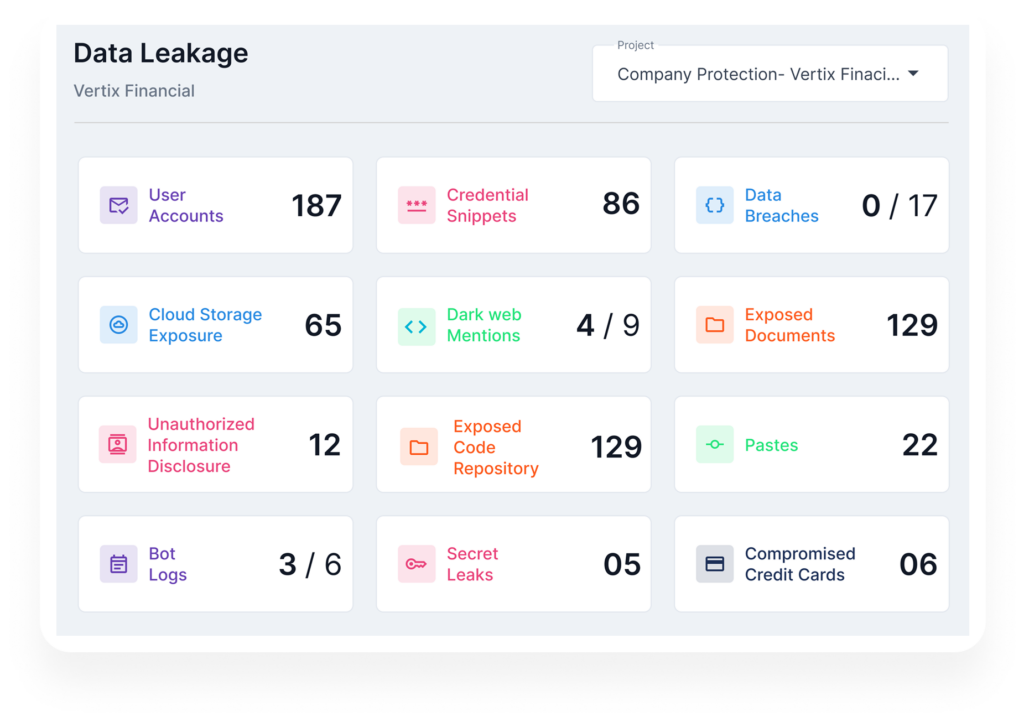
One Platform to Secure Your Sensitive Data
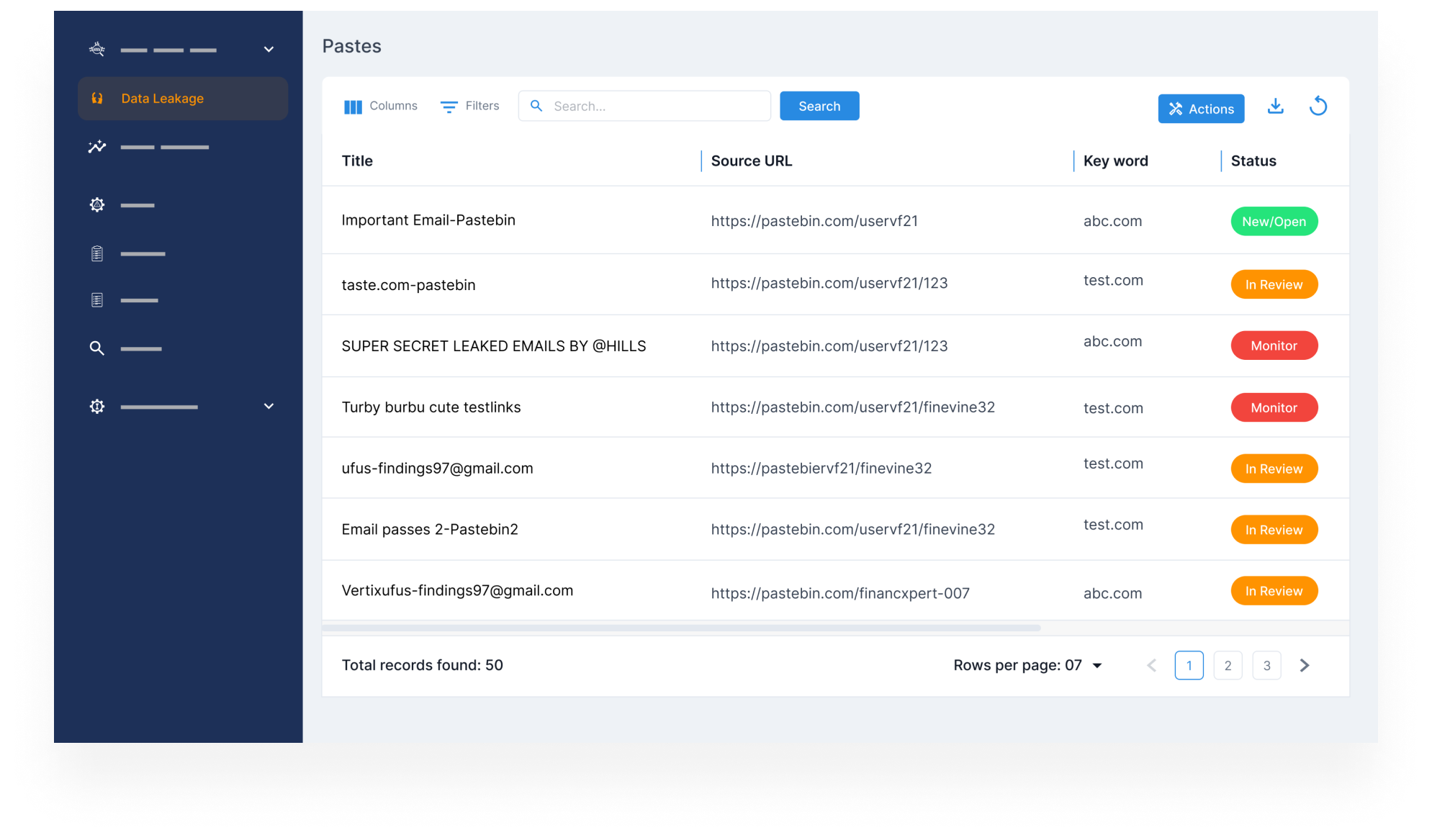
Monitor Compromised Credentials Across Surface, Deep, & Dark Web
- Continuously monitor for exposed employee, executive, and customer credentials across forums, breach dumps, and marketplaces.
- Detect leaked usernames and passwords before they’re used in account takeovers or phishing attacks.
- Get alerted early and act fast to minimize damage, reset access, and protect your systems.
Monitor Compromised Credentials Across Surface, Deep, & Dark Web
Track Dark Web Forums & Marketplaces

Track Dark Web Forums & Marketplaces
- Monitor criminal marketplaces where stolen documents, financial data, and corporate access are traded.
- Uncover mentions of your brand, employees, or sensitive data being sold or targeted.
- Gain visibility into criminal intent and prevent fraud, insider threats, or reputational damage.
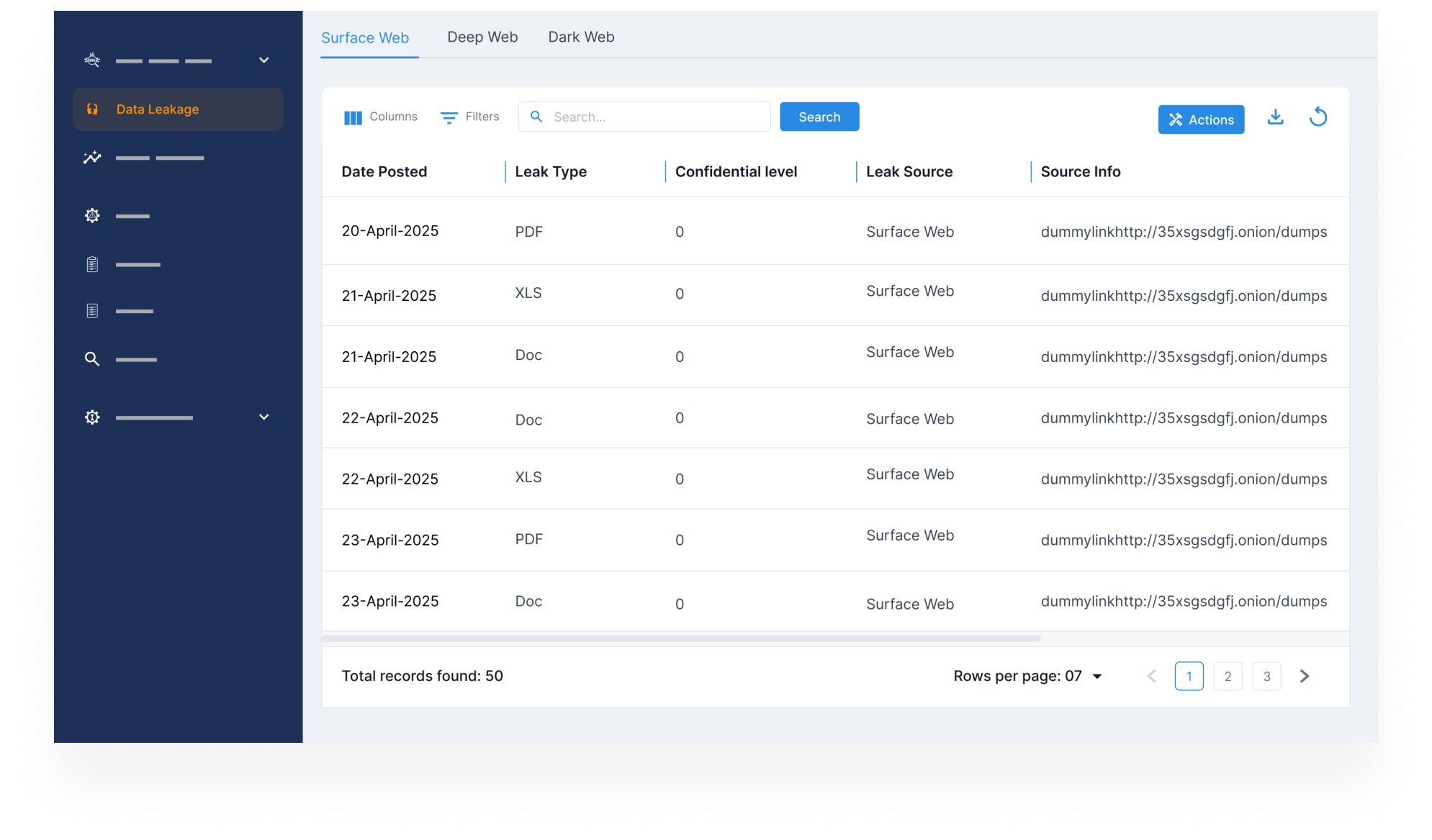
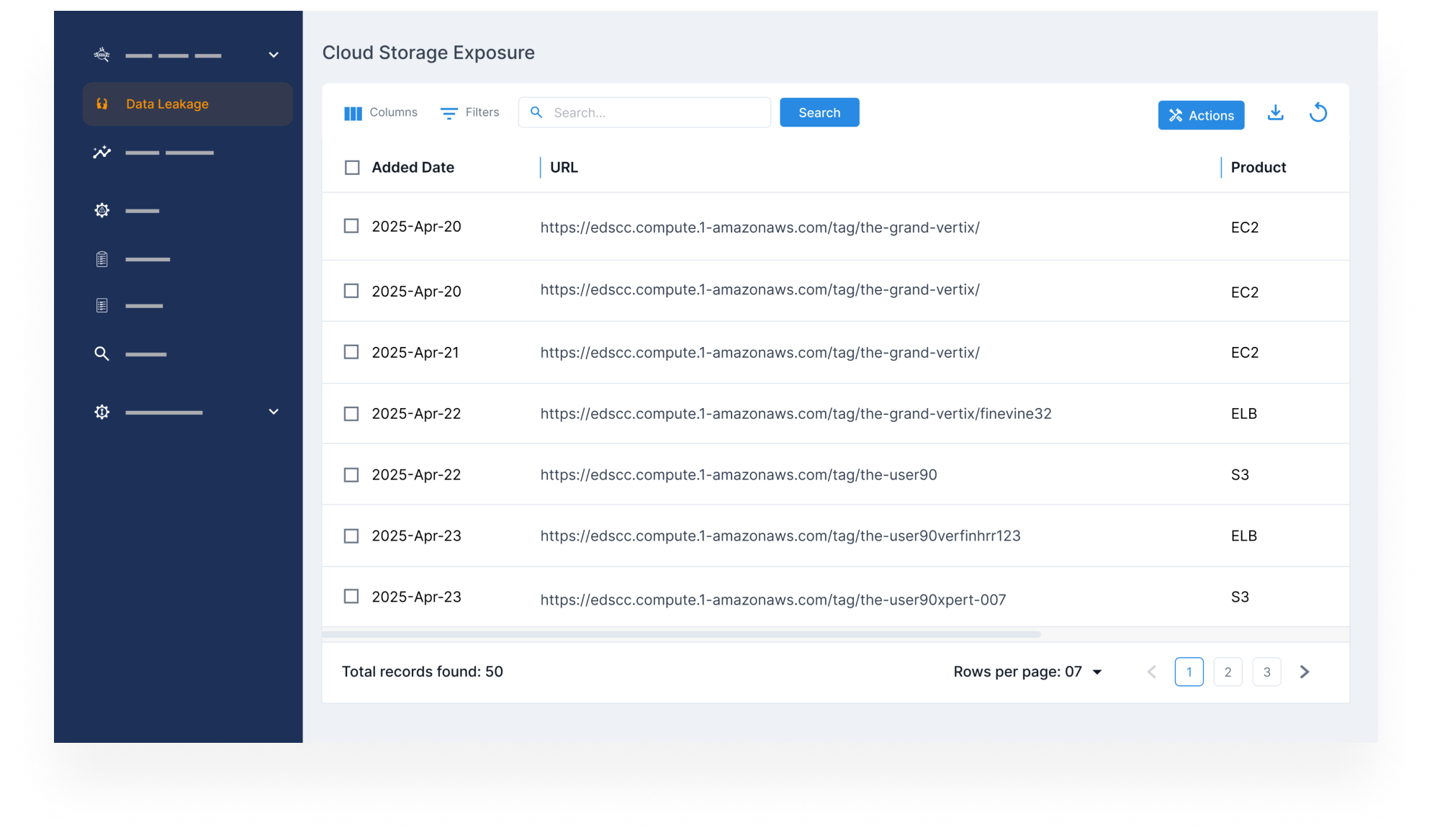
Protect Sensitive Information in Cloud Storage
- Scan platforms like AWS, GCP, and Azure for exposed storage buckets containing business-critical files.
- Identify misconfigured environments and restrict unauthorized public access.
- Prevent leaks of PII, contracts, and other confidential data that could lead to compliance failures.
Protect Sensitive Information in Cloud Storage
Detect Leaked Proprietary Code & Confidential Business Files
Detect Leaked Proprietary Code & Confidential Business Files
- Monitor source code repositories, file-sharing platforms, and dark web forums for leaked IP.
- Detect unauthorized distribution of your trade secrets, internal docs, or product blueprints.
- Reduce the risk of competitors or threat actors exploiting exposed business intel.
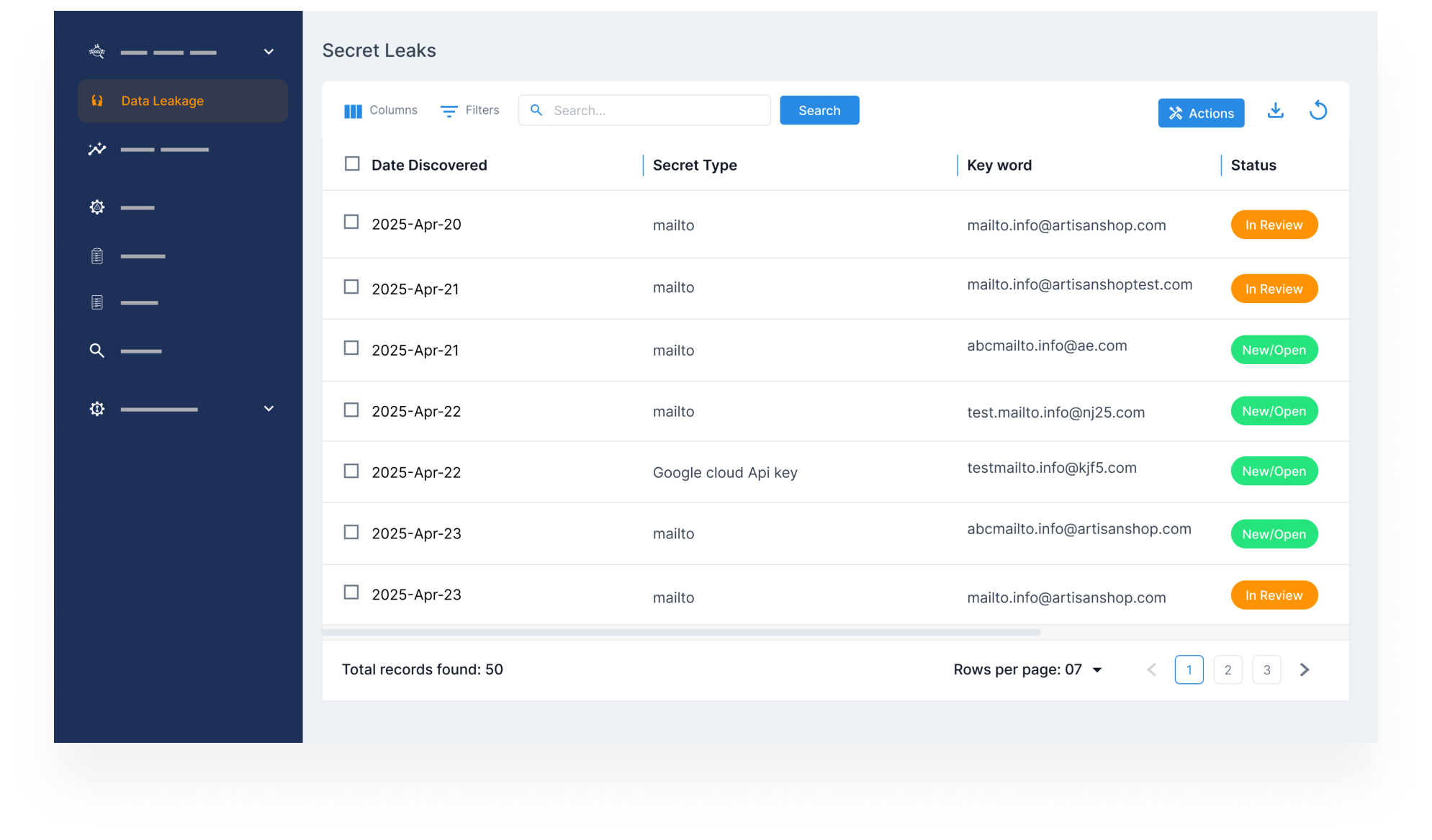
Monitor for Exposed Technical Information & Insider Leaks
- Identify sensitive infrastructure data, such as internal configs, VPN info, and credentials, leaked intentionally or accidentally.
- Detect insider threats, misdirected uploads, and risky disclosures that could aid attackers.
- Take control of your digital footprint and stop breaches before they begin.
Monitor for Exposed Technical Information & Insider Leaks
Credit card fraud monitoring
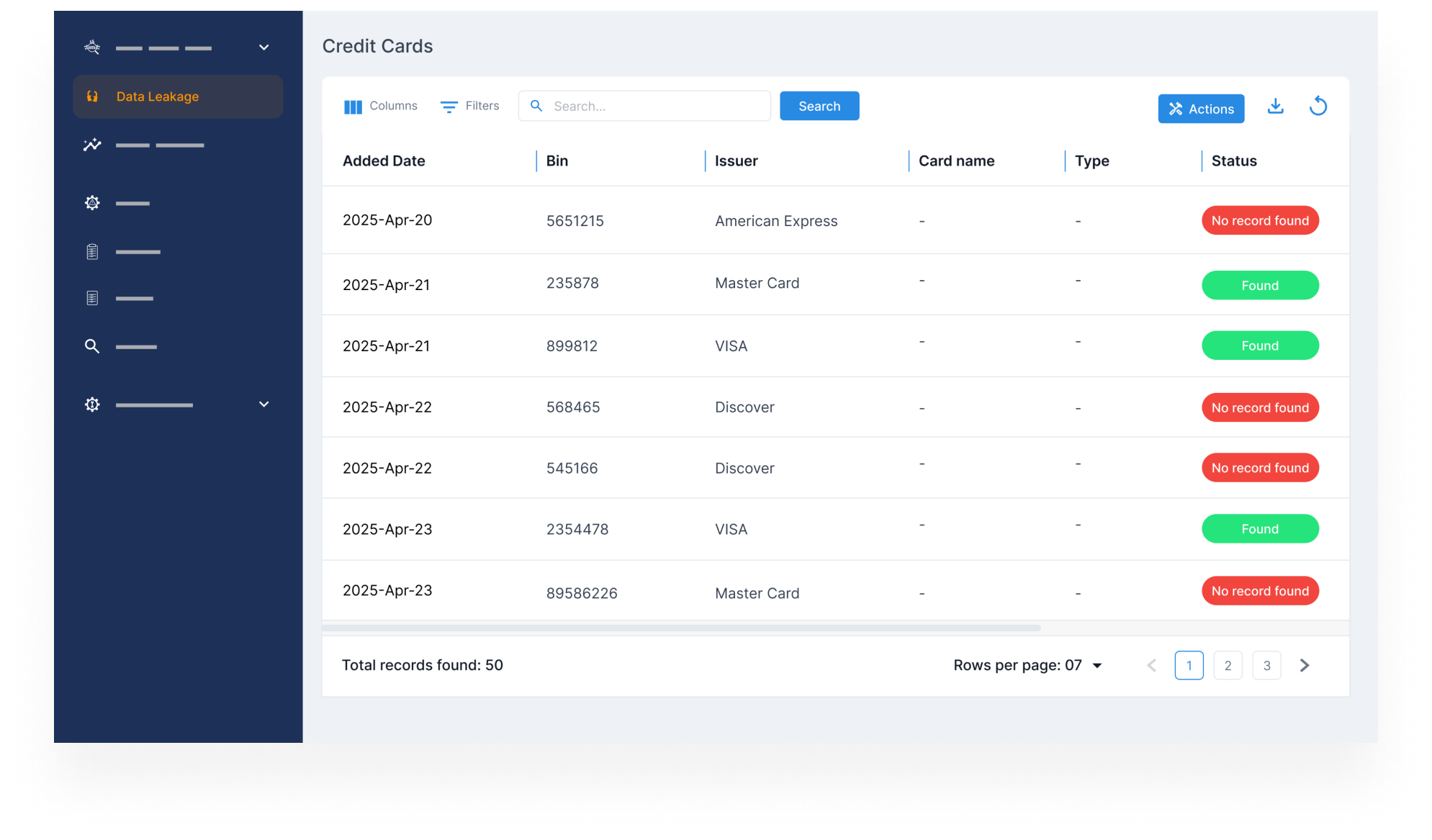
Credit card fraud monitoring
- Monitor dark web marketplaces for stolen credit card numbers tied to your brand, customers, or platforms.
- Get early warnings on fraud campaigns targeting your systems or users.
- Act quickly to prevent unauthorized transactions, reduce liability, and protect your customers’ trust.
Protect Your Sensitive Information At All Times
Monitor leaks, secure exposed data, and prevent cybercriminals from misusing your brand’s information.
Shield your Brand with StyxView’s Threat Intelligence
- Monitor Compromised Credentials Across Surface, Deep, & Dark Web
- Track Dark Web Forums & Marketplaces
- Protect Sensitive Information in Cloud Storage
- Detect Leaked Proprietary Code & Confidential Business Files
- Monitor for Exposed Technical Information & Insider Leaks
- Credit card fraud monitoring
Learn More About How We Protect Brands
Explore the Latest on Digital Risk
FAQs on Data Leakage by Styx Intel
We continuously scan dark web forums, paste sites, and hacker marketplaces to detect leaked credentials, corporate documents, and other sensitive company data. Real-time alerts help you act before attackers exploit the exposed information.
Exposed employee or customer login details can be used for unauthorized account access, fraud, data theft, and large-scale breaches. Attackers can also use them to impersonate employees, escalate privileges, or infiltrate internal systems.
Our system monitors for stolen passwords, leaked corporate documents, exposed cloud storage, dark web mentions, confidential financial records, and compromised API keys that could be used to exploit your business.
While some leaks cannot be erased, we provide real-time alerts, strategic mitigation steps, and coordinate with hosting providers and platform operators to remove sensitive data where possible.
Our system runs continuous scans and provides instant alerts whenever new breaches, leaks, or mentions of your company appear in underground forums and illicit marketplaces.





