Threat Intelligence That Works for You
Track malware campaigns, targeted attacks, and cybercriminal chatter as they happen. Get the intelligence you need to understand scammer tactics and respond proactively.
Threat Intelligence Solution by STYX
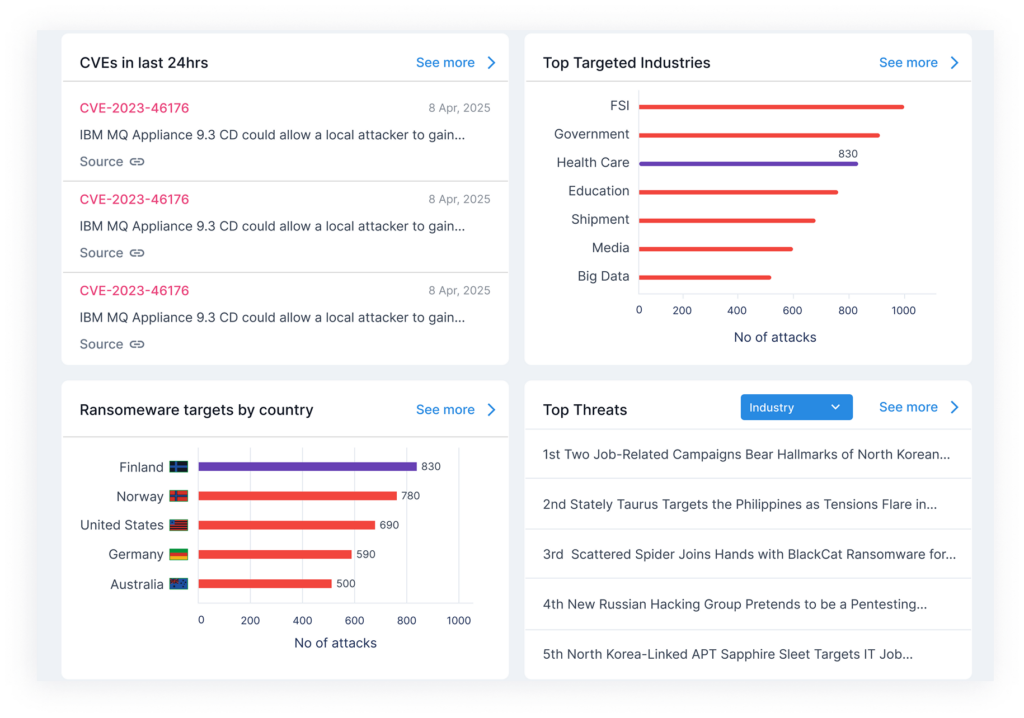
Monitor Cyber Threats in Real Time
- Stay ahead of emerging threats with live intelligence on malware campaigns, targeted attacks, and cybercriminal tactics.
- Receive timely alerts with actionable context so your team can neutralize threats before they escalate.
- Reduce incident response time by knowing what’s happening, before it hits your organization.
Monitor Cyber Threats in Real Time
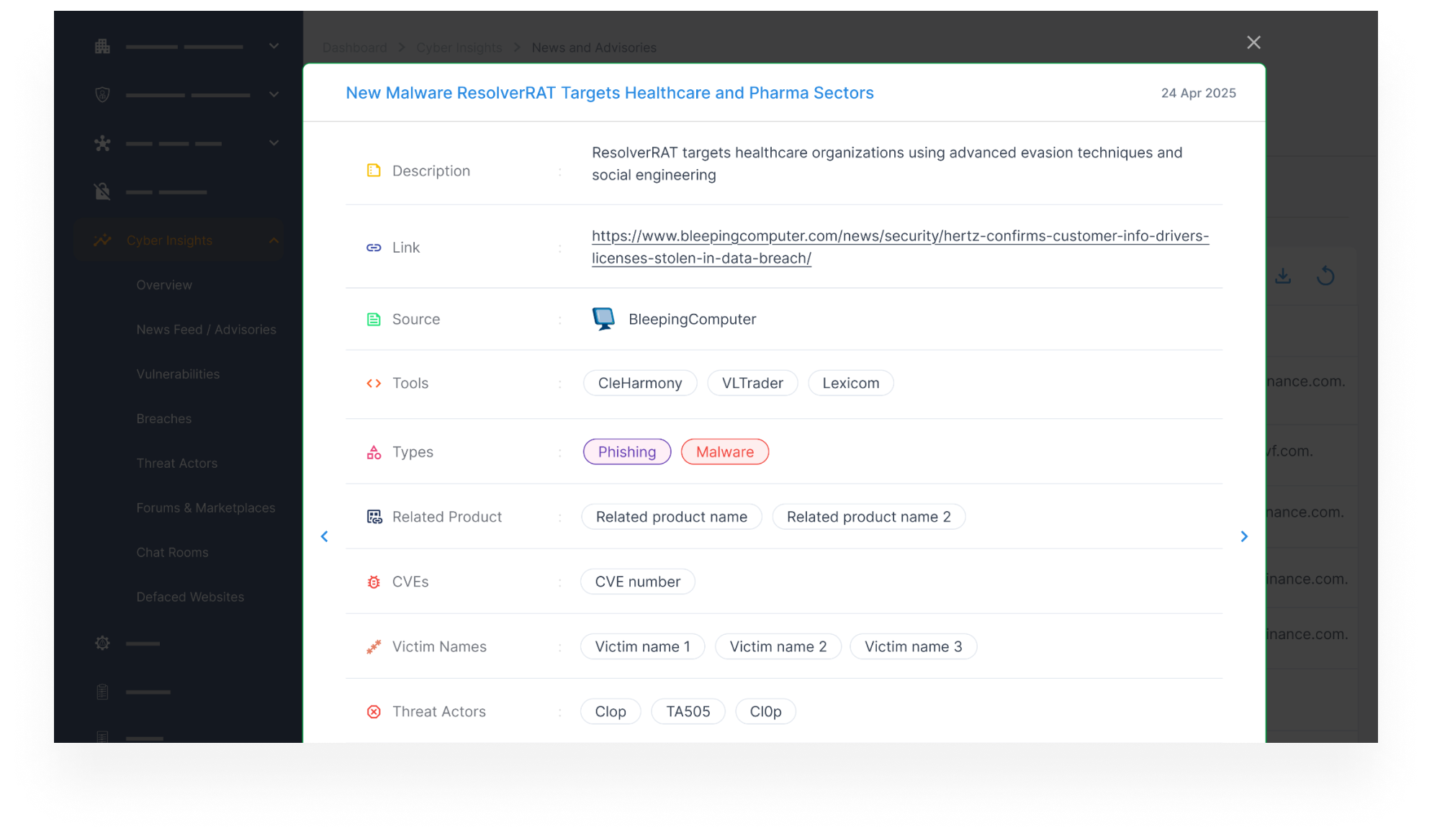
Identify and Prioritize Vulnerabilities
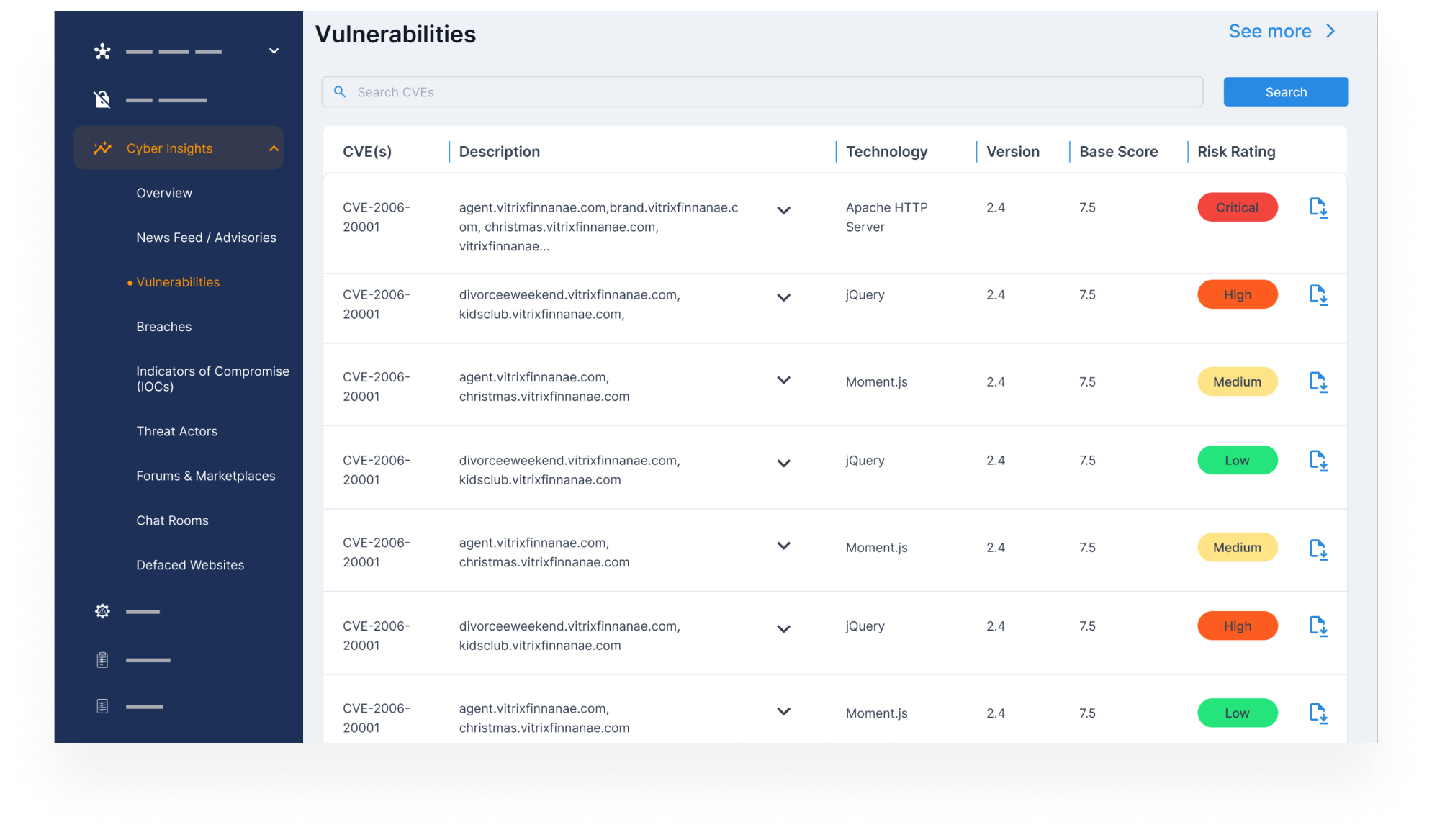
Identify and Prioritize Vulnerabilities
- Track new vulnerabilities (CVEs) across your digital footprint, including brand assets, vendor systems, and exposed infrastructure.
- Prioritize based on exploitability, business impact, and threat actor chatter.
- Focus remediation efforts on what actually puts your brand at risk, not just what’s trending.
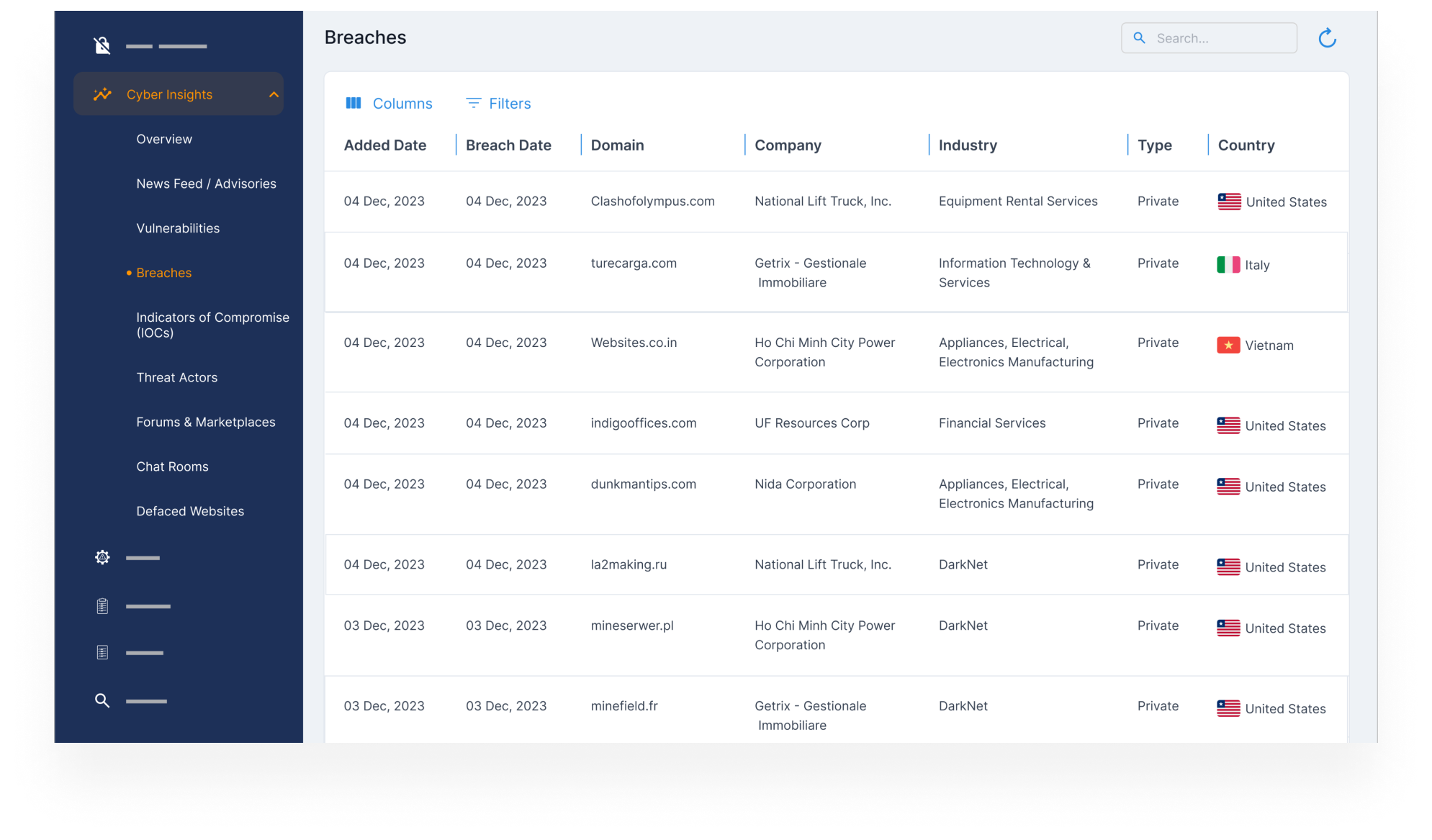
Detect and Analyze Data Breaches
- Monitor for leaked credentials, stolen customer records, or internal business files traded across dark web marketplaces.
- Get full visibility into breach sources, timelines, and data types involved.
- Act quickly to mitigate risk, notify stakeholders, and protect brand trust.
Detect and Analyze Data Breaches
Track Threat Actor Activity and Trends
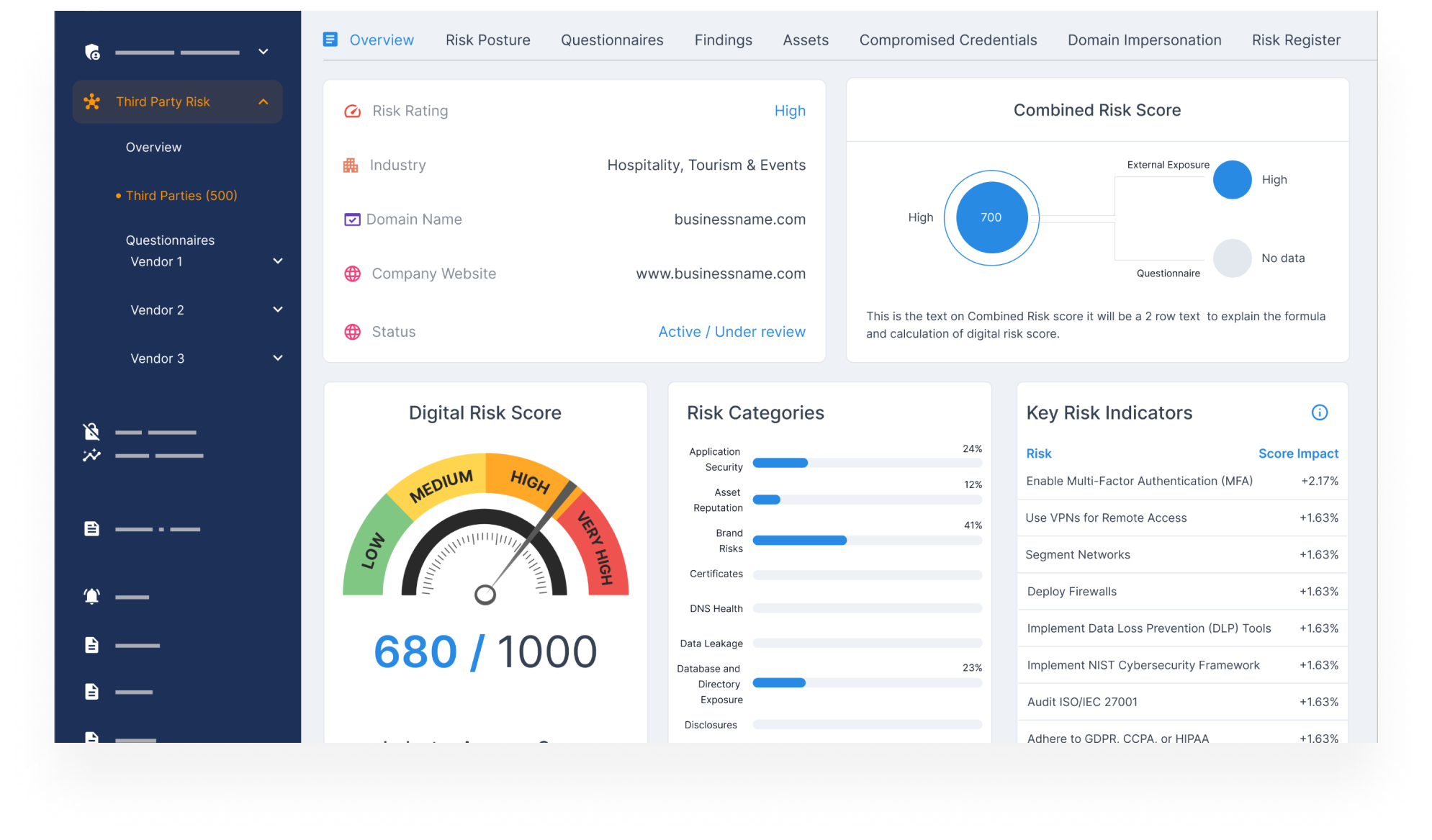
Track Threat Actor Activity and Trends
- Get insights from cybercriminal forums and underground networks — see who’s targeting companies like yours and how.
- Identify new TTPs (tactics, techniques, and procedures) and prepare defenses accordingly.
- Anticipate high-risk campaigns before they become widespread.
Understand the Impact of Global Cyber Incidents
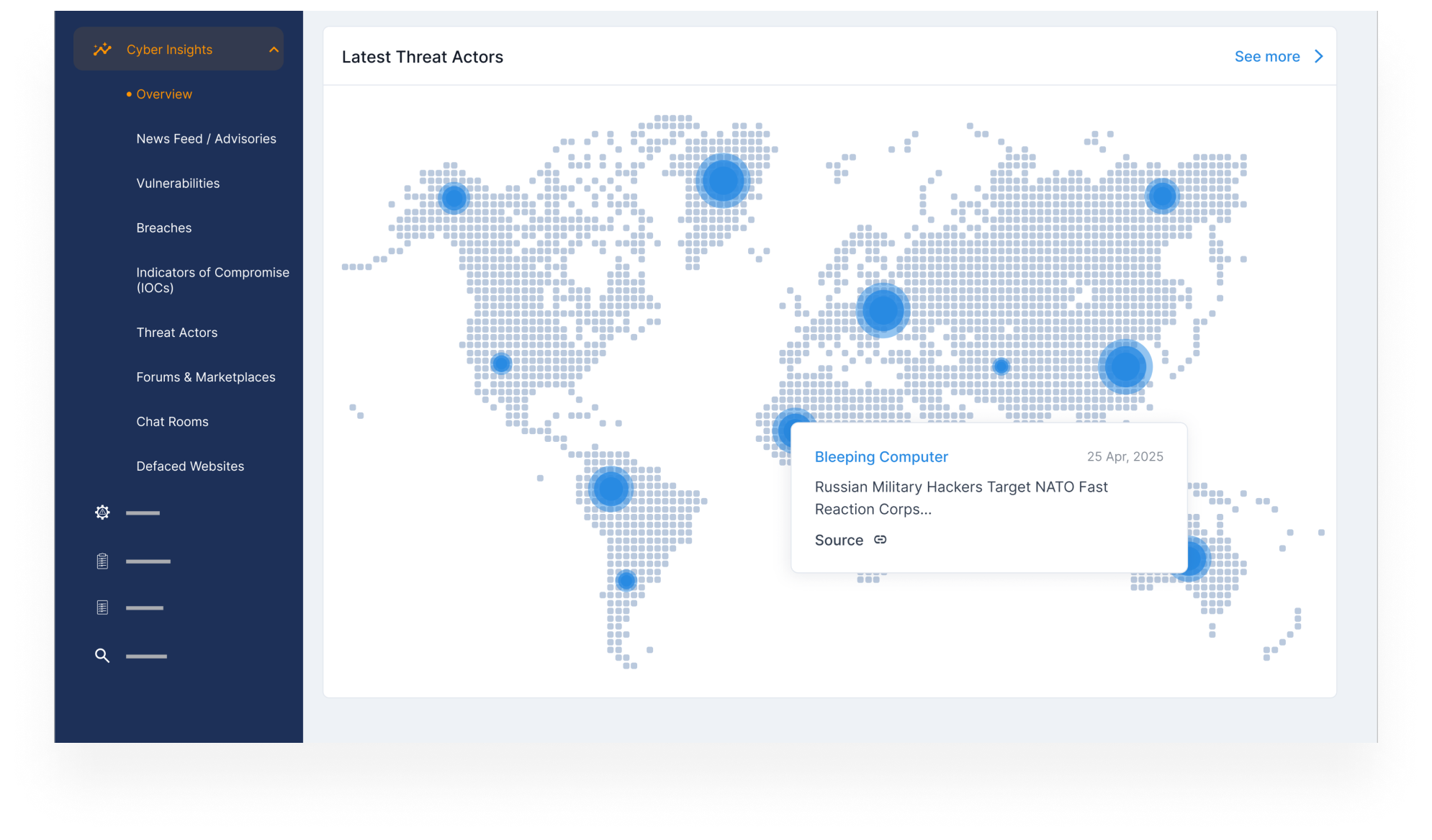
Understand the Impact of Global Cyber Incidents
- Track global ransomware attacks, industry-specific breaches, and major exploit campaigns.
- See how similar companies are being targeted, and use those insights to harden your defenses.
- Strengthen leadership reporting with contextual intelligence on global threats that could affect your operations.
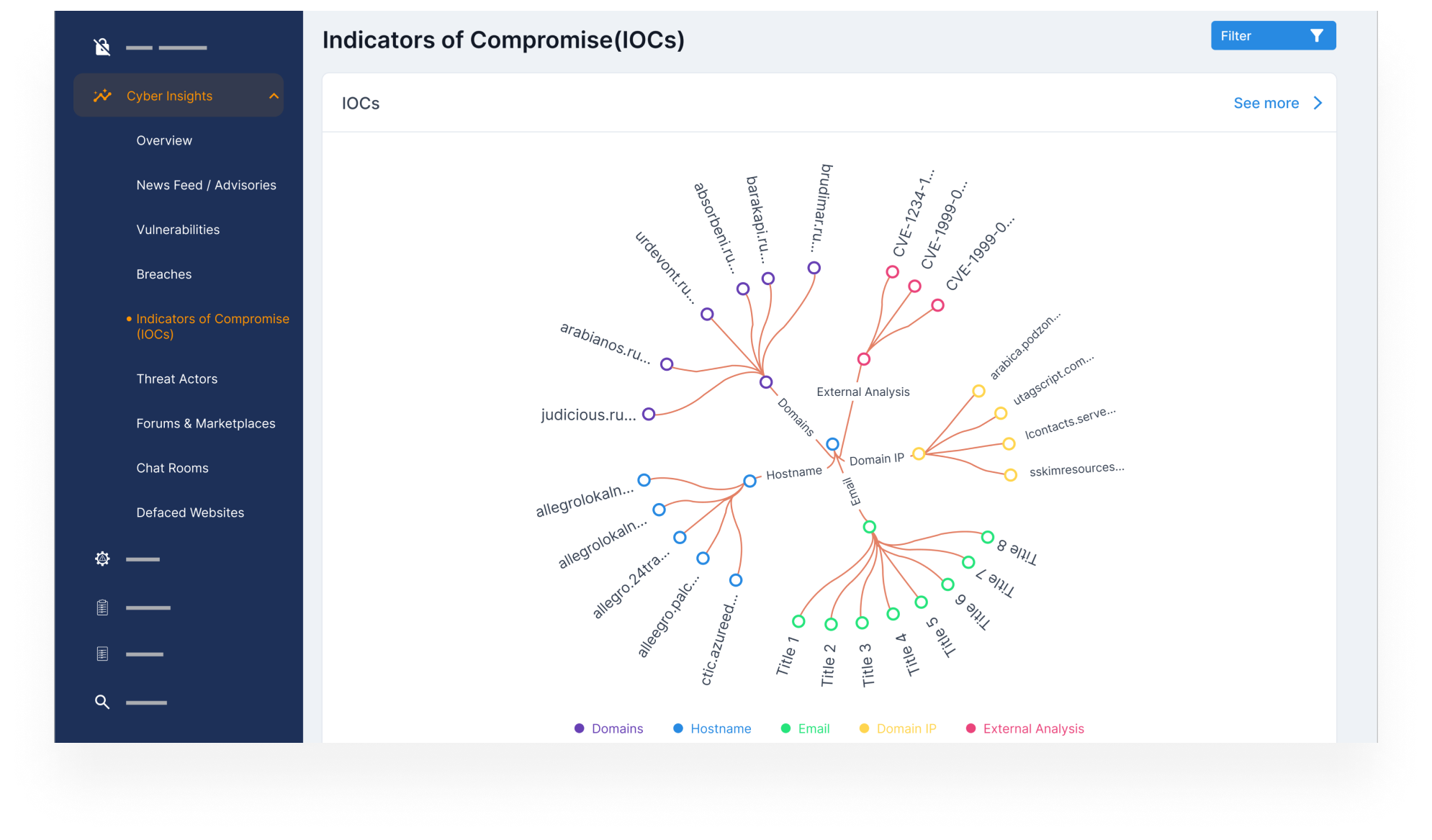
Detect Indicators of Compromise (IOCs)
- Block malicious IPs, domains, hashes, and URLs associated with phishing, malware, or command-and-control infrastructure.
- Continuously update detection rules based on threat intel feeds and analyst insights.
- Reduce dwell time and prevent damage by identifying threats at the earliest stage.
Detect Indicators of Compromise (IOCs)
Turn Cyber Threats Into Security Action
Detect risks early, respond fast, and protect your business with real-time intelligence.
Shield your Brand with StyxView’s Threat Intelligence
- Monitor Cyber Threats in Real Time
- Identify and Prioritize Vulnerabilities
- Detect and Analyze Data Breaches
- Track Threat Actor Activity and Trends
- Understand the Impact of Global Cyber Incidents
- Detect Indicators of Compromise (IOCs)
Learn More About How We Protect Brands
Explore the Latest on Digital Risk
FAQs on Threat Intelligence by Styx Intel
Threat intelligence delivers real-time insights into cyber threats, tracking vulnerabilities, data breaches, and attack methods to help businesses anticipate and neutralize security risks.
Styx continuously scans news sources, dark web forums, hacker chat rooms, and cybercrime marketplaces to identify emerging threats that could target your brand.
Yes. By monitoring exploited vulnerabilities, tracking leaked data, and identifying attack trends in real time, Styx enables security teams to take proactive measures before threats escalate.
Industries handling sensitive data — including financial services, healthcare, retail, and technology — rely on threat intelligence to prevent cyberattacks and maintain regulatory compliance.
Our platform continuously aggregates threat data from open sources, cybercriminal forums, dark web marketplaces, and security advisories, delivering instant alerts and strategic intelligence to mitigate risks.





