Know Every Digital Asset That Represents Your Brand
Untracked domains, misconfigured APIs, and exposed cloud services create risks. Discover, monitor, and secure your brand’s digital footprint before cybercriminals exploit it.
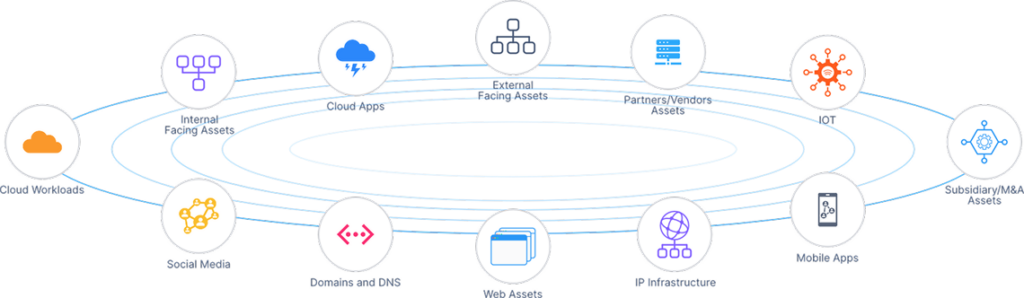
One Platform to Secure Your Digital Footprint
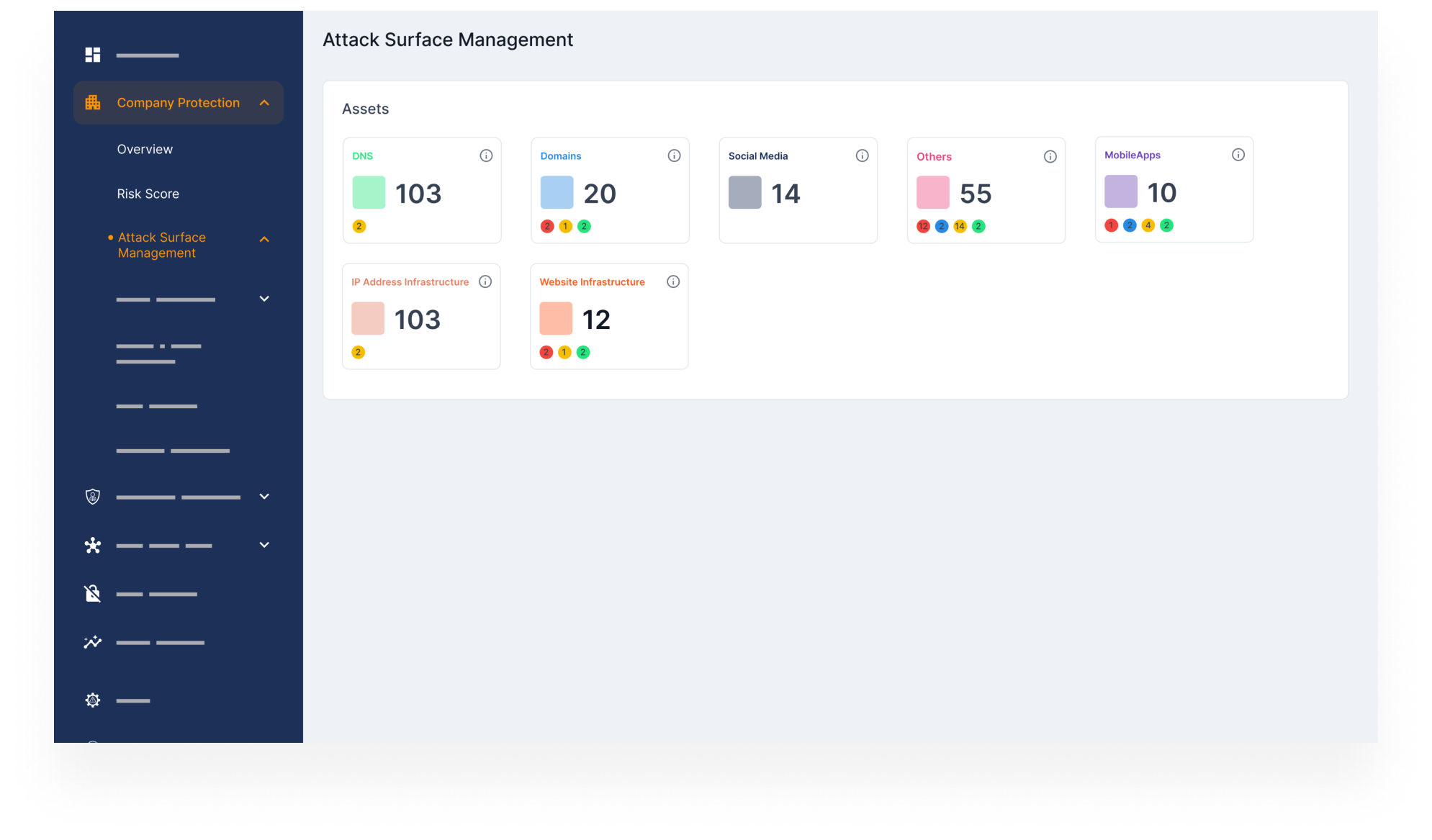
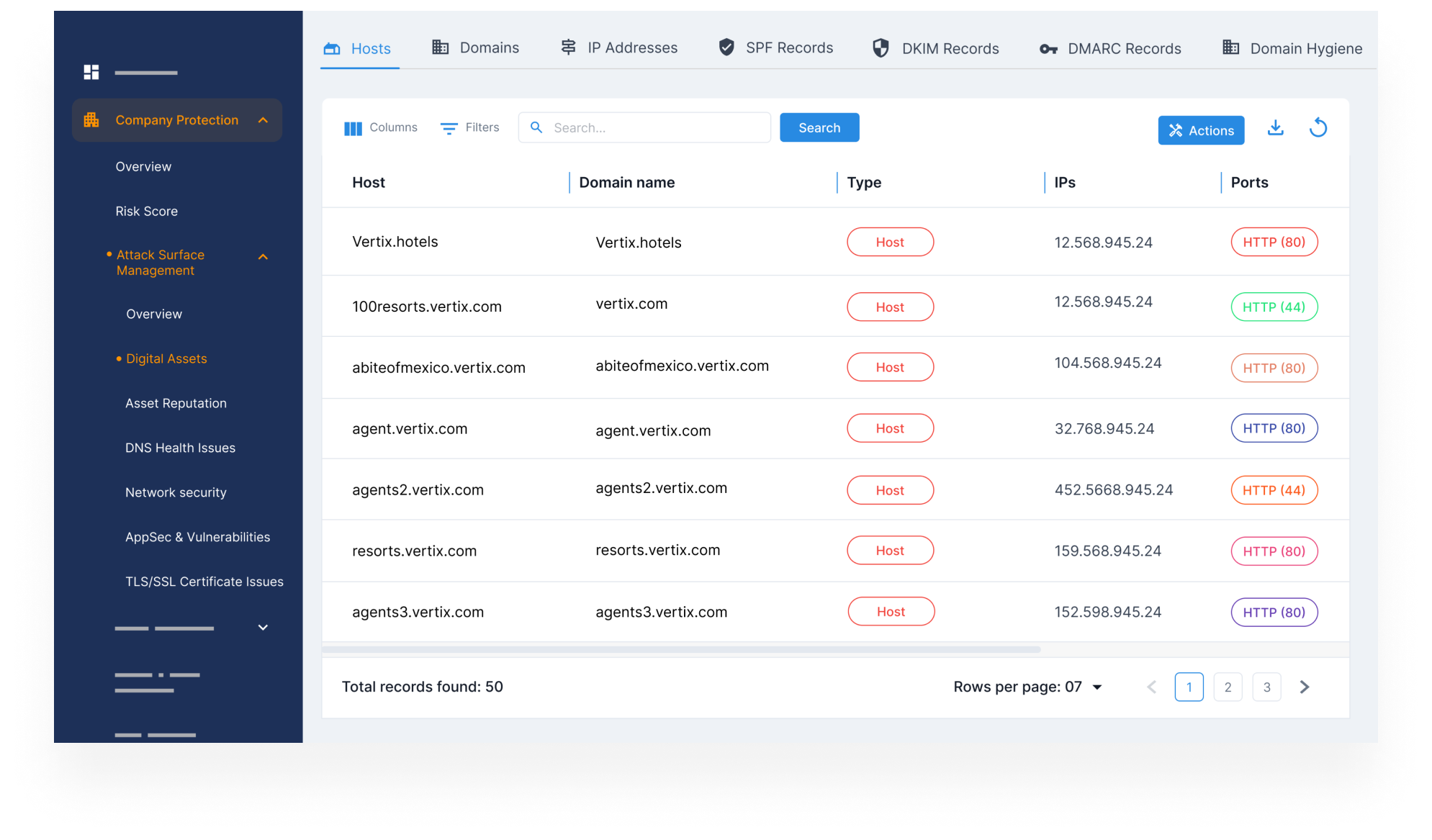
Complete Inventory of Internet-Facing Brand Assets
- Automatically identify and categorize all domains, IPs, cloud apps, and infrastructure linked to your organization — including unknown or shadow assets.
- Visualize and manage your attack surface with a centralized dashboard that shows which assets are public-facing and potentially exploitable.
- Detect weak points that may be overlooked by IT and ensure no critical asset goes unmonitored
Complete Inventory of Internet-Facing Brand Assets
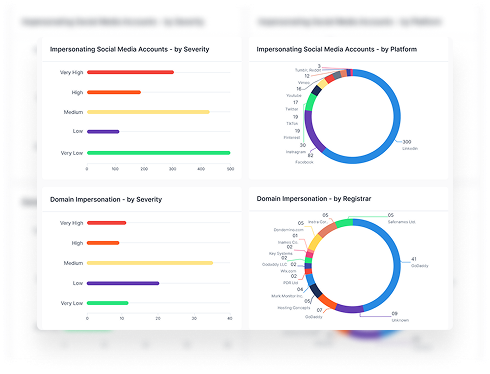
Detect Misconfigured or Vulnerable Assets
Detect Misconfigured or Vulnerable Assets
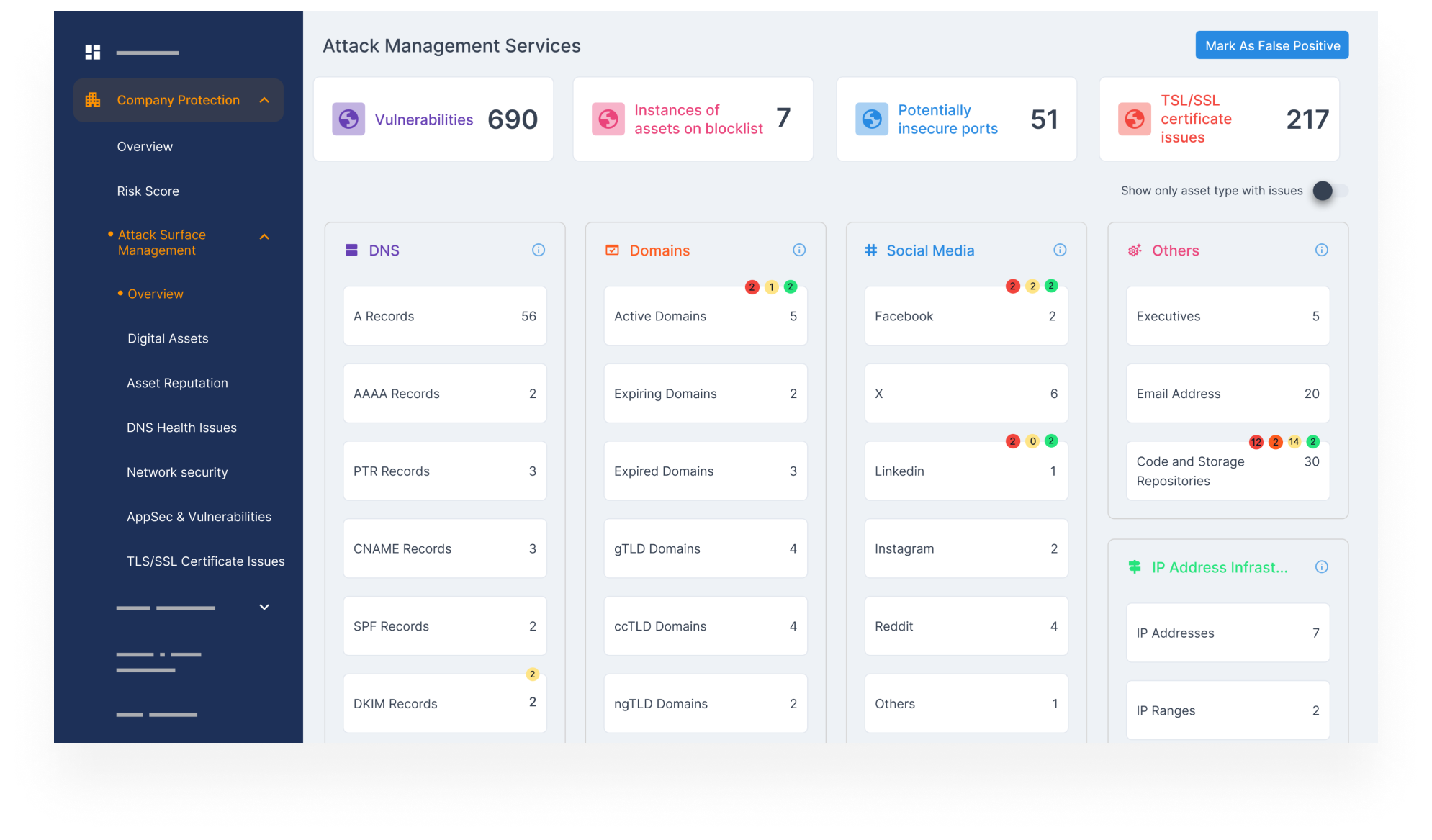
- Spot common misconfigurations like open ports, expired certificates, weak HTTP headers, and TLS/SSL issues that expose your brand to risk.
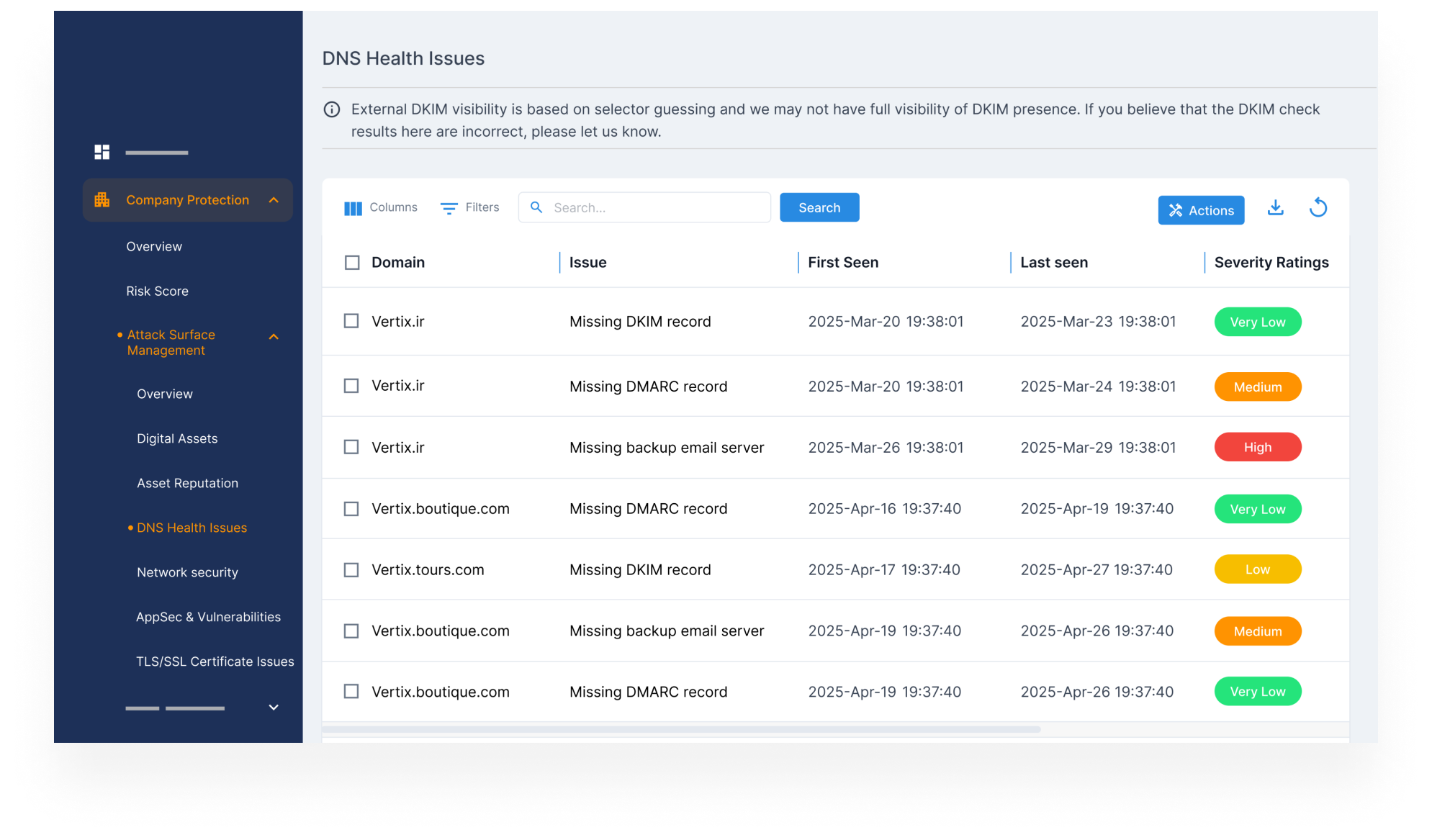
- Identify DNS and email-related errors (MX, SPF, NS records) that can lead to spoofing or email-based threats.
- Get alerts on exposed systems tied to known CVEs, and check the reputation of your IPs across blocklists to maintain trust and deliverability.
Guidance and Prioritized Remediation
- Get clear, actionable recommendations on how to resolve each issue — no guesswork required.
- Use your Digital Risk Score to measure and track cyber posture over time, based on asset exposure, misconfigurations, credential leaks, and IP reputation.
- Focus your team on what matters most with built-in remediation priorities and expert guidance at every step.
Guidance and Prioritized Remediation
Secure Email, Domains, and Network Infrastructure
Secure Email, Domains, and Network Infrastructure
- Audit and monitor your DNS, TLS/SSL, and IP infrastructure to ensure critical security controls are in place.
- Prevent spoofing, phishing, and domain misuse that could compromise trust or deceive your customers.
- Continuously track infrastructure changes and misconfigurations across all environments.
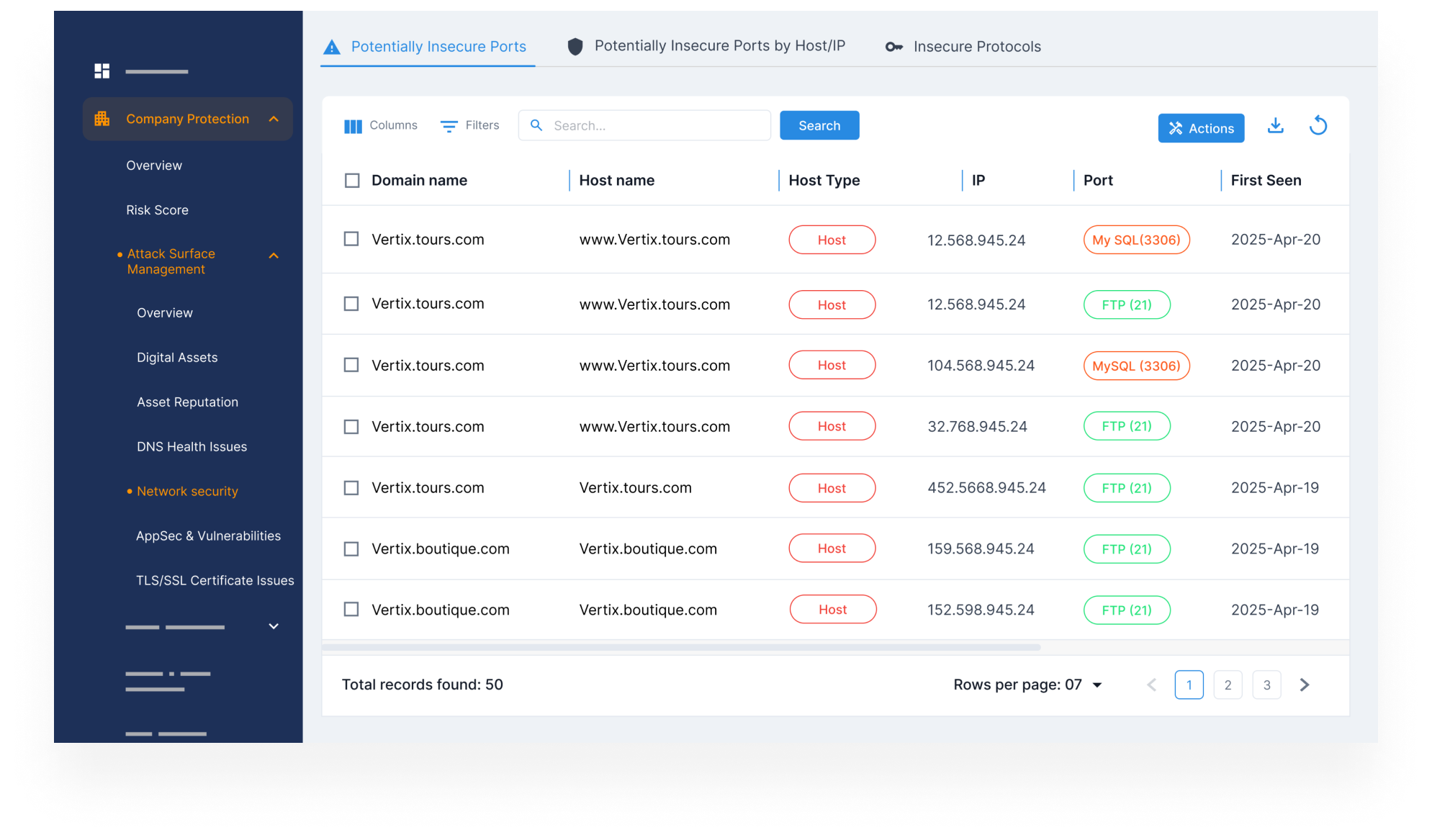
Scan External Assets for Security Gaps
- Run real-time and scheduled scans across your external-facing assets to identify vulnerabilities.
- Detect outdated systems, misconfigured servers, or weak encryption that increase exposure.
- Surface high-priority issues for faster remediation by security teams.
Scan External Assets for Security Gaps
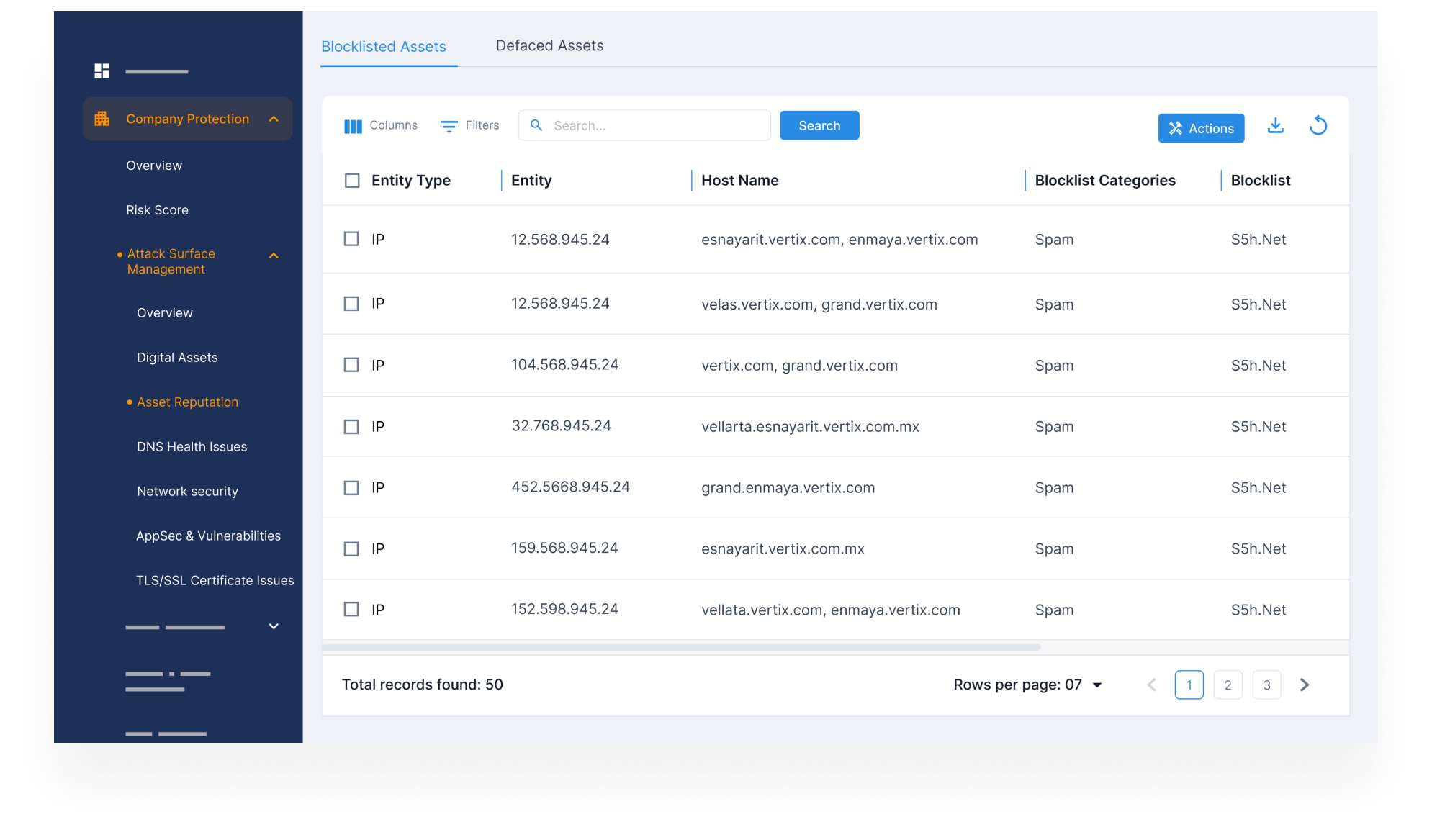
Detect & Remediate Internet-Facing Shadow IT
Detect & Remediate Internet-Facing Shadow IT
- Discover unapproved websites, tools, or cloud apps using your brand name without your knowledge. Shut them down before they expose sensitive data, confuse customers, or harm your reputation.
Secure Your Brand’s Digital Footprint
Track, assess, and remediate vulnerabilities in domains, APIs, and cloud services before they become attack vectors.
Shield your Brand with StyxView’s External Attack Surface Management
- Complete Inventory of Internet-Facing Brand Assets
- Detect Misconfigured or Vulnerable Assets
- Guidance and Prioritized Remediation
- Secure Email, Domains, and Network Infrastructure
- Scan External Assets for Security Gaps
- Detect & Remediate Internet-Facing Shadow IT
Learn More About How We Protect Brands
Explore the Latest on Digital Risk
FAQs on EASM by Styx Intel
EASM uncovers security gaps in your external digital footprint, detecting vulnerabilities that attackers can exploit to impersonate, defraud, or compromise your brand.
We track domains, subdomains, APIs, cloud services, SaaS applications, and other internet-facing assets to detect security risks before they become threats.
It evaluates your brand’s security posture by analyzing external risks, identifying vulnerabilities, and assigning a risk score to help prioritize mitigation efforts.
Yes, it continuously monitors misconfigurations, third-party integrations, and cloud services that could expose sensitive brand data or create security risks.
We provide real-time monitoring and automated scanning to detect emerging threats, ensuring your brand stays protected against evolving security risks.